Exam 7: The Web and E-Mail
Exam 1: Computers and Digital Basics170 Questions
Exam 2: Computer Hardware175 Questions
Exam 3: Computer Software175 Questions
Exam 4: Operating Systems and File Management175 Questions
Exam 5: Lans and Wlans175 Questions
Exam 6: The Internet175 Questions
Exam 7: The Web and E-Mail175 Questions
Exam 8: Digital Media175 Questions
Exam 9: The Computer Industry: History, Careers, and Ethics175 Questions
Exam 10: Information Systems Analysis and Design175 Questions
Exam 11: Databases175 Questions
Exam 12: Computer Programming175 Questions
Select questions type
Case Based Critical Thinking Questions Case 1 Marissa is concerned about Internet security for e-commerce. While researching the topic, she has learned about ActiveX controls and Java applets. Which of the following is NOT true?
(Multiple Choice)
4.7/5  (35)
(35)
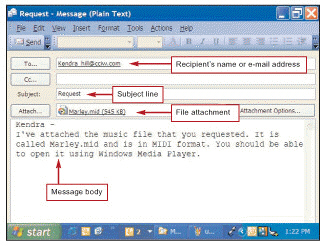 The message header and body of an e-mail are usually displayed in a(n) ____, as shown in the above figure.
The message header and body of an e-mail are usually displayed in a(n) ____, as shown in the above figure.
(Multiple Choice)
4.8/5  (37)
(37)
Antispam software usually includes the technology to block common spams, but you can create your own ____ for spam that that misses.
(Multiple Choice)
4.9/5  (32)
(32)
Individuals who prefer not to leave a trail of their Internet activities surf through a(n) ____________________ proxy service, which uses an intermediary server to relay Web page requests after masking the originating IP address.
(Short Answer)
4.9/5  (27)
(27)
Critical Thinking questions (Multiple Choice) If a Web page author includes meta keywords such as "free" and "money" even though the term has little to do with the information on the page, in what practice is this person engaging?
(Multiple Choice)
4.7/5  (38)
(38)
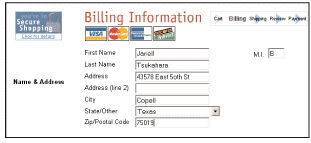 HTML ____, as shown in the figure above, are typically used to collect payment and shipping information at the checkout counter of e-commerce Web sites.
HTML ____, as shown in the figure above, are typically used to collect payment and shipping information at the checkout counter of e-commerce Web sites.
(Multiple Choice)
4.9/5  (32)
(32)
Case 4 Elizabeth is doing a series of Internet searches. She is finding that there are efficient and precise ways to do these searches. For the next search, she wants to make sure that complete phrase - Mars exploration - exists on a Web page for it to be included in the results. What would be the search operator or way to achieve this objective?
(Multiple Choice)
4.9/5  (42)
(42)
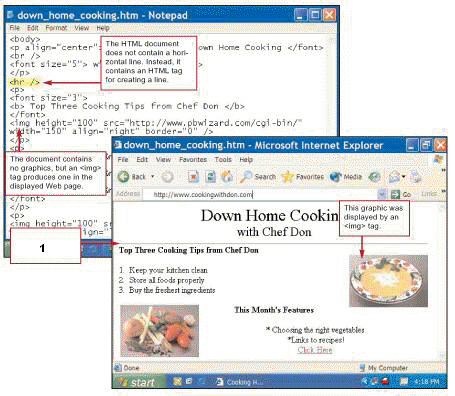 The design element marked 1 in the figure above was created by the ____ tag.
The design element marked 1 in the figure above was created by the ____ tag.
(Multiple Choice)
4.9/5  (30)
(30)
____ e-commerce involves one enterprise buying goods or services from another enterprise.
(Multiple Choice)
4.8/5  (32)
(32)
Critical Thinking questions (Multiple Choice) Melissa has some digital pictures of the last party she and her friends attended and would like to e-mail them to all of the recipients in her address book. As people are worried about viruses, what can she do to assure her recipients of the e-mail attachments that the e-mail is from a reliable source?
(Multiple Choice)
4.8/5  (46)
(46)
Whereas S-HTTP creates a secure connection between a client and a server over which any amount of data can be sent securely, SSL is simply designed to encrypt and then transmit an individual message.
(True/False)
4.9/5  (38)
(38)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Unwanted electronic junk mail about medical products, low-cost loans, and fake software upgrades that arrives in your online mailbox
Responses:
helper application
Ajax
electronic wallet
Correct Answer:
Premises:
Responses:
(Matching)
4.9/5  (36)
(36)
Web-based e-mail gives you the option of downloading your mail or leaving it on the server.
(True/False)
4.8/5  (40)
(40)
HTML is called a markup language because authors mark up their documents by inserting special instructions, called HTML tags, that specify how the document should appear when displayed on a computer screen.
(True/False)
4.9/5  (32)
(32)
Give two reasons why it is important to upgrade your browser when new versions become available.
(Essay)
4.7/5  (37)
(37)
Every Web page has a unique address called a(n) Uniform Resource Locator .
(True/False)
4.9/5  (31)
(31)
____ is a protocol that works in conjunction with TCP/IP to get Web resources to your desktop.
(Multiple Choice)
4.8/5  (34)
(34)
Showing 121 - 140 of 175
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)