Exam 12: Security Through Monitoring and Auditing
Exam 1: Operating Systems Security: Keeping Computers and Networks Secure86 Questions
Exam 2: Viruses, Worms, and Malicious Software86 Questions
Exam 3: Security Through Authentication and Encryption86 Questions
Exam 4: Account-Based Security86 Questions
Exam 6: Firewalls and Border Security86 Questions
Exam 7: Physical and Network Topology Security86 Questions
Exam 8: Wireless Security86 Questions
Exam 9: Web, Remote Access, and VPN Security86 Questions
Exam 10: E-Mail Security86 Questions
Exam 11: Security Through Disaster Recovery86 Questions
Exam 12: Security Through Monitoring and Auditing86 Questions
Select questions type
Which type of intrusion detection focuses on monitoring network traffic associated with a specific network segment?
(Multiple Choice)
4.9/5  (33)
(33)
In the event log, what type of event is indicated with a white "x" that appears inside a red circle?
(Multiple Choice)
4.9/5  (40)
(40)
Which active intrusion-detection tool is a distributed system that works on servers and clients and denies application requests that are not permitted, on the basis of a security policy applying to the servers and clients?
(Multiple Choice)
4.9/5  (41)
(41)
Which event log records events that are associated with Active Directory?
(Multiple Choice)
4.7/5  (35)
(35)
Can Network Monitor filter frames and packets on the basis of SAP or ETYPE?
(True/False)
4.7/5  (46)
(46)
Active intrusion detection is effective as long as the server or network administrator regularly checks the logs and recorded information for possible intrusion attempts.
(True/False)
4.9/5  (35)
(35)
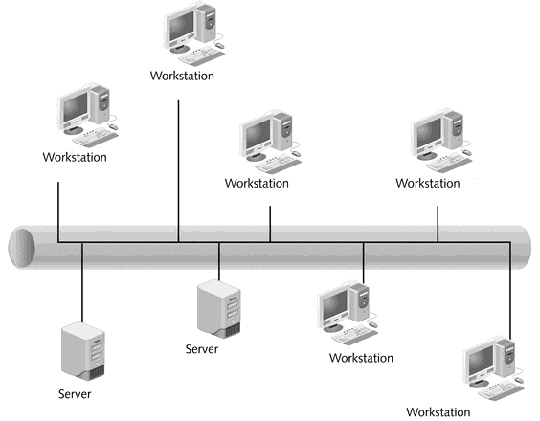 If a network administrator wants to use host-based intrusion detection, which devices in the figure above would need to be configured?
If a network administrator wants to use host-based intrusion detection, which devices in the figure above would need to be configured?
(Multiple Choice)
4.8/5  (39)
(39)
Network Monitor is a utility which comes with Windows 2000 Server and Windows Server 2003.
(True/False)
4.9/5  (42)
(42)
The default folder for saved Network Monitor capture information in Windows Server 2003 is \WINNT\system32\NETMON\CAPTURES .
(True/False)
4.9/5  (32)
(32)
Network-based intrusion-detection software is categorized as host wrappers or host-based agents.
(True/False)
4.9/5  (29)
(29)
A(n) ____________________ can be acquired by using performance monitoring to establish slow, average, and peak periods for a network, and keeping records on these periods.
(Short Answer)
4.8/5  (42)
(42)
At minimum, ____________________ intrusion detection alerts a server or network administrator about an attack or intrusion, so the administrator can take action.
(Short Answer)
4.9/5  (40)
(40)
Can the version of Network Monitor that comes with Windows Server 2003 capture and read the contents of any frames transported on the network segment to which the host computer is connected?
(True/False)
4.8/5  (37)
(37)
In Netware, in which directory are the Access log and the Error log kept?
(Multiple Choice)
5.0/5  (39)
(39)
Which passive intrusion-detection tool monitors network activity and includes a proprietary programming language to customize the way it captures and analyzes information?
(Multiple Choice)
4.8/5  (30)
(30)
Showing 61 - 80 of 86
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)