Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
A system administrator created a firewall policy that allows certain applications and blocks others. However, some applications are being blocked that should be allowed. Which log should be viewed to troubleshoot this issue?
(Multiple Choice)
4.8/5  (39)
(39)
A threat was detected by Auto-Protect on a client system. Which command can an administrator run to determine whether additional threats exist?
(Multiple Choice)
4.8/5  (35)
(35)
Which two instances could cause Symantec Endpoint Protection to be unable to remediate a file? (Select two.)
(Multiple Choice)
4.9/5  (37)
(37)
Which type of email does Internet Email Auto-Protect support?
(Multiple Choice)
4.9/5  (31)
(31)
An administrator installed Symantec Endpoint Protection 12.1 (SEP) in the environment. However, the administrator wants to use secure communication and SSL authentication between clients and the Symantec Endpoint Protection Manager (SEPM). How should the administrator proceed?
(Multiple Choice)
4.8/5  (38)
(38)
Where is a file encrypted and saved to when the "Backup files before attempting to repair them" setting is enabled?
(Multiple Choice)
4.8/5  (34)
(34)
A company has an application that requires network traffic in both directions to multiple systems at a specific external domain. A firewall rule was created to allow traffic to and from the external domain, but the rule is blocking incoming traffic. What should an administrator enable in the firewall policy to allow this traffic?
(Multiple Choice)
4.9/5  (45)
(45)
A computer is configured in Mixed Control mode. The administrator creates and applies a Firewall policy to the computer that has a rule that allows FTP traffic above the blue line and another rule that blocks LDAP traffic below the blue line. On the computer, local rules are created to allow LDAP traffic and block FTP traffic. Which traffic flow behavior should be expected on the local computer?
(Multiple Choice)
4.9/5  (39)
(39)
An administrator wants to deploy the Symantec Endpoint Protection 12.1 (SEP) client to computers that are lacking the Symantec Endpoint Protection client. Which tool should the administrator use to discover and deploy the SEP client to the computers?
(Multiple Choice)
4.8/5  (34)
(34)
An administrator needs to add an Application Exception. When the administrator accesses the Application Exception dialog window, applications fail to appear. What is the likely problem?
(Multiple Choice)
4.9/5  (36)
(36)
A Symantec Endpoint Protection (SEP) administrator performed a disaster recovery without a database backup. In which file should the SEP administrator add "scm.agent.groupcreation=true" to enable the automatic creation of client groups?
(Multiple Choice)
4.9/5  (27)
(27)
Refer to the exhibit. 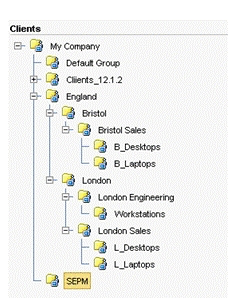 A manufacturing company runs three shifts at their Bristol Sales office. These employees currently share desktops in the B_Desktops group. The administrators need to apply different policies/configurations for each shift. Which step should the administrator take in order to implement shift policies after switching the clients to user mode?
A manufacturing company runs three shifts at their Bristol Sales office. These employees currently share desktops in the B_Desktops group. The administrators need to apply different policies/configurations for each shift. Which step should the administrator take in order to implement shift policies after switching the clients to user mode?
(Multiple Choice)
4.7/5  (37)
(37)
An administrator is recovering from a Symantec Endpoint Manager (SEPM) site failure. Which file should the administrator use during an install of SEPM to recover the lost environment according to Symantec Disaster Recovery Best Practice documentation?
(Multiple Choice)
4.8/5  (36)
(36)
A company is deploying Symantec Endpoint Protection 12.1 and configuring remediation options within the Virus and Spyware Protection policy. They are considering enabling "Terminate processes automatically" within the remediation options. If this feature is enabled, which two characteristics will the user see when the client must terminate a process to remove or repair a risk? (Select two.)
(Multiple Choice)
4.8/5  (35)
(35)
Refer to the exhibit. 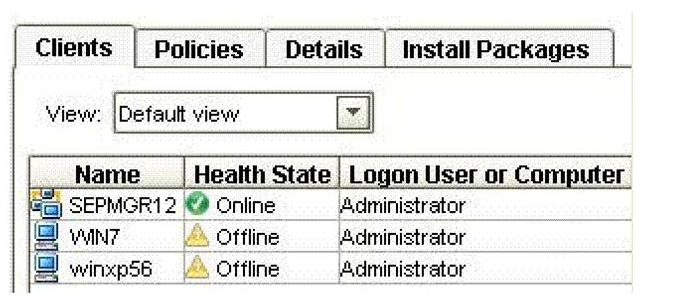 What does the symbol to the left of the system name, SEPMGR12, indicate?
What does the symbol to the left of the system name, SEPMGR12, indicate?
(Multiple Choice)
4.7/5  (34)
(34)
An administrator needs to configure Secure Socket Layer (SSL) communication for clients. In the httpd.conf file, located on the Symantec Endpoint Protection Manager (SEPM), the administrator removes the hashmark (#) from the text string displayed below. #Include conf/ssl/sslForcClients.conf< Which two tasks must the administrator perform to complete the SSL configuration? (Select two.)
(Multiple Choice)
4.7/5  (32)
(32)
What is a function of the Symantec Endpoint Protection client?
(Multiple Choice)
4.9/5  (41)
(41)
Which action can an administrator take to improve the Symantec Endpoint Protection Manager (SEPM) dashboard performance and report accuracy?
(Multiple Choice)
4.8/5  (31)
(31)
After several failed logon attempts, the Symantec Endpoint Protection Manager (SEPM) has locked the default admin account. An administrator needs to make system changes as soon as possible to address an outbreak, but the admin account is the only account. Which action should the administrator take to correct the problem with minimal impact to the existing environment?
(Multiple Choice)
4.8/5  (36)
(36)
Showing 21 - 40 of 165
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)