Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
Which command line syntax invokes the Symantec Endpoint Protection Client Service to determine whether a more recent copy of the configuration file is available on the management server?
(Multiple Choice)
4.9/5  (35)
(35)
Multiple Windows virtual clients running on an ESX server need to be scanned daily by a scheduled scan. Which feature should an administrator use to improve scan performance on the clients?
(Multiple Choice)
4.8/5  (43)
(43)
You have just started a relayout operation in a live test environment, and you want to limit the impact of your work on concurrent testing activities. You also want to accommodate the need to constrain a relayout job's performance impact on concurrent activities. What would you do to perform this task?
(Multiple Choice)
4.8/5  (36)
(36)
A manufacturing company runs three shifts. Employees at the facility must share computers. The administrators need to apply different policies/configurations for each shift. The administrator will need to switch the clients to User mode. Which two additional configuration changes need to be made to allow policies to be applied to each shift? (Select two.)
(Multiple Choice)
4.9/5  (40)
(40)
An administrator is using the SylinkDrop tool to update a Symantec Endpoint Protection client install on a system. The client fails to migrate to the new Symantec Endpoint Protection Manager (SEPM), which is defined correctly in the Sylink.xml file that was exported from the SEPM. Which settings must be provided with SylinkDrop to ensure the successful migration to a new Symantec Endpoint Protection environment with additional Group Level Security Settings?
(Multiple Choice)
4.9/5  (35)
(35)
Refer to the exhibit. 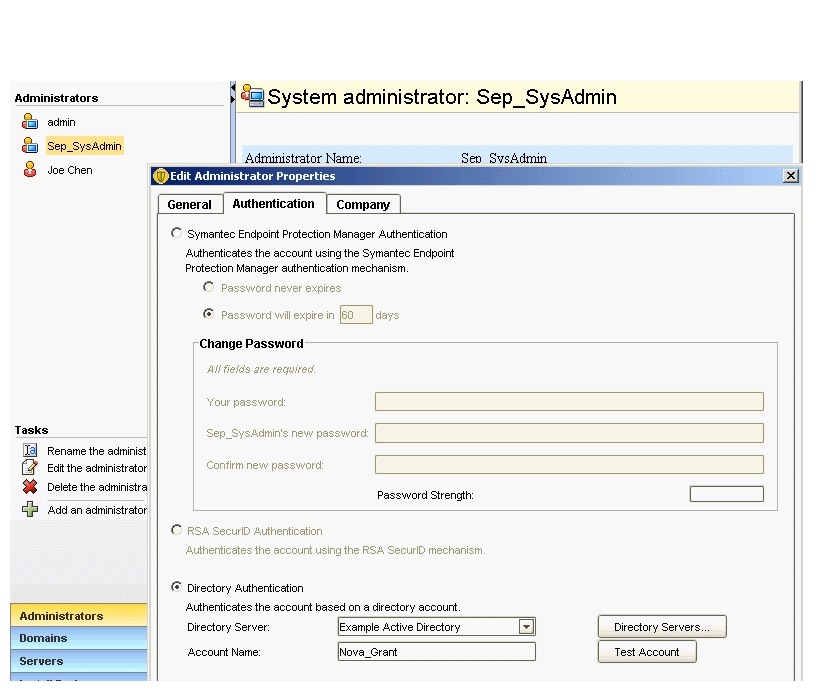 An administrator has configured the Symantec Endpoint Protection Manager (SEPM) to use Active Directory authentication. The administrator defines a new Symantec Endpoint Protection administrator named Sep_SysAdmin, configured to use Directory Authentication. Which password needs to be entered when the administrator logs in to the SEPM console as Sep_SysAdmin?
An administrator has configured the Symantec Endpoint Protection Manager (SEPM) to use Active Directory authentication. The administrator defines a new Symantec Endpoint Protection administrator named Sep_SysAdmin, configured to use Directory Authentication. Which password needs to be entered when the administrator logs in to the SEPM console as Sep_SysAdmin?
(Multiple Choice)
5.0/5  (39)
(39)
An administrator plans to implement a multi-site Symantec Endpoint Protection (SEP) deployment. The administrator needs to determine whether replication is viable without needing to make network firewall changes or change defaults in SEP. Which port should the administrator verify is open on the path of communication between the two proposed sites?
(Multiple Choice)
4.9/5  (38)
(38)
Which two sources can a Macintosh client use to download content? (Select two.)
(Multiple Choice)
4.9/5  (37)
(37)
For replication, Symantec recommends that the number of sites be kept to five for optimum performance. What can be done to reduce the number of sites?
(Multiple Choice)
4.7/5  (38)
(38)
Which step is unnecessary when an administrator creates an application rule set?
(Multiple Choice)
4.8/5  (37)
(37)
An administrator changes the Virus and Spyware Protection policy for a specific group that disables Auto-Protect. The administrator assigns the policy and the client systems applies the corresponding policy serial number. Upon visual inspection of a physical client system, the policy serial number is correct. However, Auto-Protect is still enabled on the client system. Which action should the administrator take to ensure that the desired setting is in place on the client?
(Multiple Choice)
4.8/5  (31)
(31)
Which two considerations must an administrator make when enabling Application Learning in an environment? (Select two.)
(Multiple Choice)
4.8/5  (32)
(32)
A company uses a remote administration tool that is detected and quarantined by Symantec Endpoint Protection (SEP). Which step can an administrator perform to continue using the remote administration tool without detection by SEP?
(Multiple Choice)
4.9/5  (29)
(29)
A clean file in a proprietary application has been quarantined by SONAR. How can an administrator fix the broken application from the Symantec Endpoint Protection Manager console?
(Multiple Choice)
4.9/5  (32)
(32)
Refer to the exhibit. 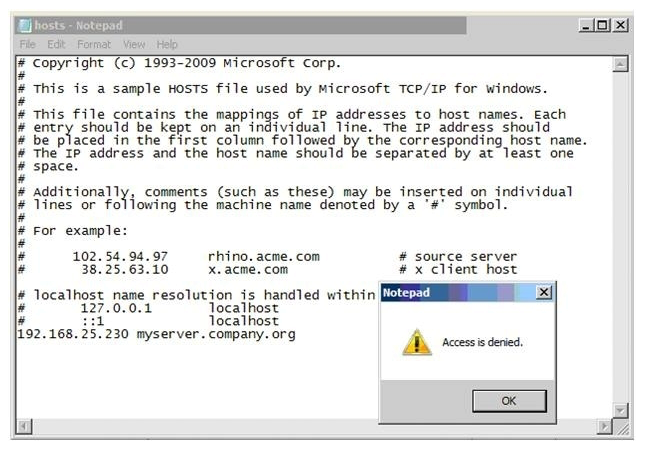 A user runs a full scan on a system and is confused by the "Files trusted" count. Which option will result in the files being left unscanned?
A user runs a full scan on a system and is confused by the "Files trusted" count. Which option will result in the files being left unscanned?
(Multiple Choice)
4.7/5  (29)
(29)
An administrator has defined a rule to allow traffic to and from a specific server by its Fully Qualified Domain Name (FQDN), because the server's IP address varies based on the office in which a client is located. The administrator attempts to verify the rule and finds that the traffic is being blocked. The logs list the IP address of the server instead of its FQDN. What does the administrator need to do within the firewall policy to allow the rule to work correctly?
(Multiple Choice)
4.7/5  (33)
(33)
Refer to the exhibit. 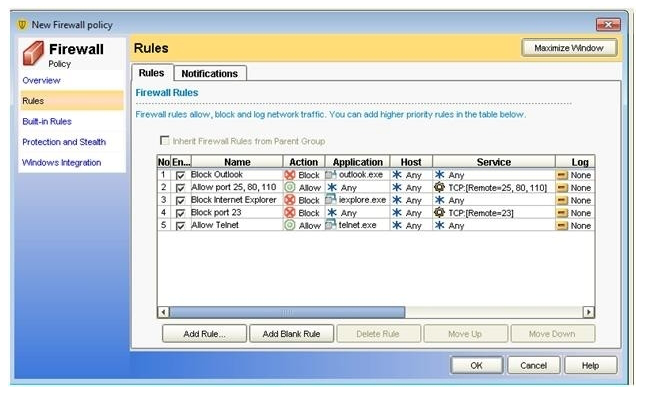 A company has created a specific firewall policy that allows only certain traffic. Which traffic is allowed in the firewall policy displayed in the exhibit?
A company has created a specific firewall policy that allows only certain traffic. Which traffic is allowed in the firewall policy displayed in the exhibit?
(Multiple Choice)
4.8/5  (41)
(41)
A Symantec Endpoint Protection 12.1 (SEP) administrator discovers that a firewall is blocking Windows file sharing. Which method can bypass the firewall and allow the SEP clients to be installed with a minimum amount of effort?
(Multiple Choice)
5.0/5  (36)
(36)
A company deploys Symantec Endpoint Protection (SEP) to 50 virtual machines running on a single ESXi host. Which configuration change can the administrator make to minimize sudden IOPS impact on the ESXi server while each SEP endpoint communicates with the Symantec Endpoint Protection Manager?
(Multiple Choice)
4.8/5  (39)
(39)
Showing 141 - 160 of 165
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)