Exam 12: Computer Programming
Exam 1: Computers and Digital Basics147 Questions
Exam 2: Computer Hardware150 Questions
Exam 3: Software149 Questions
Exam 4: Operating Systems and File Management150 Questions
Exam 5: Local Area Networks150 Questions
Exam 6: The Internet149 Questions
Exam 7: The Web and E-mail150 Questions
Exam 8: Digital Media150 Questions
Exam 9: The Computer Industry: History,Careers,and Ethics150 Questions
Exam 10: Information Systems Analysis and Design150 Questions
Exam 11: Databases150 Questions
Exam 12: Computer Programming150 Questions
Select questions type
A(n)____ table is a tabular method for visualizing and specifying rules based on multiple factors.
(Multiple Choice)
4.8/5  (37)
(37)
John and Andy are planning a software project. You tell John and Andy there are several software development methodologies that exist to help program designers. These can be classified into two groupings.
-The methodology that you have chosen allows little room for adaptation and change,now that the specifications for the software were completed in the design phase.Which methodology did you choose?
(Multiple Choice)
4.9/5  (31)
(31)
Agnes is talking with Bert and Ernesto, and they are discussing object-oriented programming. Agnes is asking some detailed questions that Bert and Ernesto can’t answer. You agree to help answer the questions.
-Agnes wants to know how to describe the characteristics of a class.You tell her characteristics are described using ____.
(Multiple Choice)
4.9/5  (39)
(39)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-A type of SDK
(Multiple Choice)
4.7/5  (34)
(34)
In the threat model STRIDE,the D stands for ____ or making a system unavailable to legitimate users.
(Multiple Choice)
4.8/5  (31)
(31)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Instructions that are executed one after another
(Multiple Choice)
4.9/5  (41)
(41)
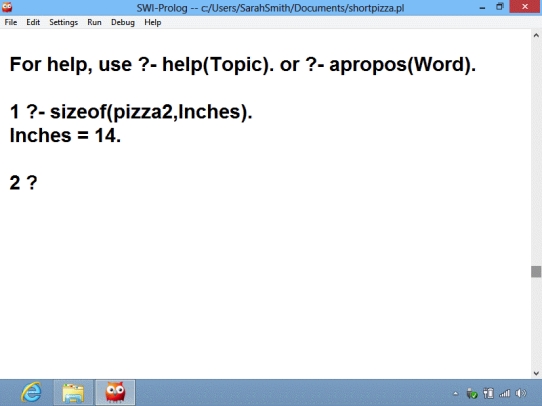 -In the jargon associated with the language in the accompanying figure,when you ask a question,it is a(n)____.
-In the jargon associated with the language in the accompanying figure,when you ask a question,it is a(n)____.
(Multiple Choice)
4.9/5  (32)
(32)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Data in memory exceeds its expected boundaries
(Multiple Choice)
4.8/5  (42)
(42)
In the threat model STRIDE,the S stands for ____ or pretending to be someone else.
(Multiple Choice)
4.9/5  (36)
(36)
A predictive methodology requires extensive planning and documentation up front.
(True/False)
4.8/5  (41)
(41)
A computer program is typically stored as a file and transferred into ____ when needed.
(Multiple Choice)
4.7/5  (43)
(43)
OO programmers often use flowcharts to plan the classes to be programmed.
(True/False)
4.9/5  (33)
(33)
Much of the power and flexibility of the Prolog language stems from its ability to sift through facts.
(True/False)
4.8/5  (40)
(40)
Agnes is talking with Bert and Ernesto, and they are discussing object-oriented programming. Agnes is asking some detailed questions that Bert and Ernesto can’t answer. You agree to help answer the questions.
-Ernesto then wants to know what you call a single instance of an entity,and you tell him that it is a(n)____.
(Multiple Choice)
4.9/5  (42)
(42)
One of the first exploits to take advantage of buffer overflows was the ____.
(Multiple Choice)
4.8/5  (32)
(32)
John and Andy are planning a software project. You tell John and Andy there are several software development methodologies that exist to help program designers. These can be classified into two groupings.
-You tell Andy and John that the ____ methodology is best for projects with a small core of developers working at a single location.
(Multiple Choice)
4.7/5  (35)
(35)
You can express an algorithm as pseudocode._________________________
(True/False)
5.0/5  (44)
(44)
A ____ language uses command words and grammar based on human language.
(Multiple Choice)
4.9/5  (33)
(33)
Showing 21 - 40 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)