Exam 12: Computer Programming
Exam 1: Computers and Digital Basics147 Questions
Exam 2: Computer Hardware150 Questions
Exam 3: Software149 Questions
Exam 4: Operating Systems and File Management150 Questions
Exam 5: Local Area Networks150 Questions
Exam 6: The Internet149 Questions
Exam 7: The Web and E-mail150 Questions
Exam 8: Digital Media150 Questions
Exam 9: The Computer Industry: History,Careers,and Ethics150 Questions
Exam 10: Information Systems Analysis and Design150 Questions
Exam 11: Databases150 Questions
Exam 12: Computer Programming150 Questions
Select questions type
____________________ modeling is a technique that can be used to identify potential vulnerabilities and develop mitigation strategies that can be implemented during coding.
(Short Answer)
4.9/5  (39)
(39)
A(n)____ is a unit of data that represents an abstraction or a real-world entity such as person,place,or thing.
(Multiple Choice)
4.7/5  (27)
(27)
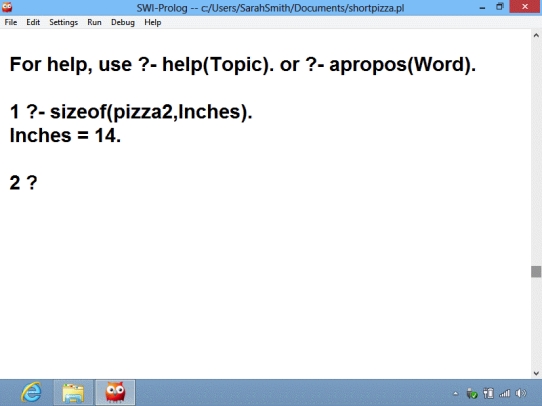 -In the context of a program like the one in the accompanying figure,a(n)____ is a statement that provides the computer with basic information for solving a problem.
-In the context of a program like the one in the accompanying figure,a(n)____ is a statement that provides the computer with basic information for solving a problem.
(Multiple Choice)
4.9/5  (40)
(40)
A hierarchical diagram of potential attacks against a system is an attack ____________________.
(Short Answer)
4.8/5  (38)
(38)
Define and discuss three techniques associated with defensive programming.
(Essay)
4.9/5  (40)
(40)
Polymorpism provides OO programs with easy extensibility and can help simplify program code.
(True/False)
4.8/5  (31)
(31)
Agnes is talking with Bert and Ernesto, and they are discussing object-oriented programming. Agnes is asking some detailed questions that Bert and Ernesto can’t answer. You agree to help answer the questions.
-Bert wants to draw a class.You suggest he use ____ to do so.
(Multiple Choice)
4.9/5  (31)
(31)
 -In the context of a program like the one in the accompanying figure,a(n)____ is a general statement about the relationship between facts.
-In the context of a program like the one in the accompanying figure,a(n)____ is a general statement about the relationship between facts.
(Multiple Choice)
4.9/5  (35)
(35)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Information that you supply to the computer to help it solve a problem
(Multiple Choice)
4.8/5  (38)
(38)
The computer begins executing a Java program by locating a standard method called ____.
(Multiple Choice)
4.8/5  (29)
(29)
Polymorphism refers to the process of hiding the internal details of objects and their methods.
(True/False)
5.0/5  (32)
(32)
When high-level languages were originally conceived in the 1950s,they were dubbed ____-generation languages.
(Multiple Choice)
4.9/5  (30)
(30)
Languages which most closely resemble natural human languages are ____-generation languages.
(Multiple Choice)
4.8/5  (32)
(32)
In the threat model STRIDE,the T stands for ____ or changing,adding,or deleting data.
(Multiple Choice)
4.9/5  (35)
(35)
The ____ paradigm attempts to describe a problem without specifying exactly how to arrive at a solution.
(Multiple Choice)
4.9/5  (32)
(32)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Used to plan classes for a program
(Multiple Choice)
4.7/5  (45)
(45)
The ____ paradigm focuses on an algorithm that describes a solution.
(Multiple Choice)
4.7/5  (30)
(30)
____ refers to passing certain characteristics from one class to another class.
(Multiple Choice)
4.7/5  (41)
(41)
A ____ provides programmers with tools to build substantial sections of a program by pointing and clicking.
(Multiple Choice)
4.7/5  (35)
(35)
Showing 81 - 100 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)