Exam 3: Essential Layers of Computer Networking
Exam 1: Networking: Fundamental Concepts33 Questions
Exam 2: Cybersecurity: Fundamentals13 Questions
Exam 3: Essential Layers of Computer Networking40 Questions
Exam 4: Ip Address Planning and Management38 Questions
Exam 5: Intermediary Devices31 Questions
Exam 6: Wi-Fi and Cellular Network43 Questions
Exam 7: Ethernet Lan24 Questions
Exam 8: Cybersecurity: Threats23 Questions
Exam 9: Cybersecurity: Network and Host Protection19 Questions
Exam 10: Cybersecurity: Data Protection24 Questions
Exam 11: Fundamentals of Packet Routing29 Questions
Exam 12: Wide Area Network33 Questions
Exam 13: Physical Layer Data Transmissions19 Questions
Exam 14: Enterprise Network: LAN Topology, Routing, and Connectivity30 Questions
Select questions type
According to the encapsulation and de-encapsulation process between standard layers, the data field of a frame most likely includes a(n) :
Free
(Multiple Choice)
4.9/5  (38)
(38)
Correct Answer:
A
A Class C network that uses 4 bits for the subnet ID can have up to _____ hosts in each subnet.
Free
(Multiple Choice)
4.8/5  (29)
(29)
Correct Answer:
A
According to the encapsulation and de-encapsulation process between standard layers, the data field of a packet may include a(n) :
Free
(Multiple Choice)
4.8/5  (34)
(34)
Correct Answer:
E
Which is the general delegation process of IP space to ISPs?
(Multiple Choice)
4.8/5  (32)
(32)
Standard details of network cables should be defined in the _____ layer
(Multiple Choice)
4.7/5  (30)
(30)
Refer to the figure in which the "www.yahoo.com" server is pinged. What is the protocol used to produce the message for communication between two hosts? ________________________. 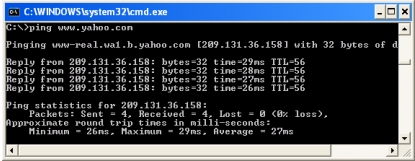
(Multiple Choice)
4.8/5  (32)
(32)
The TTL (time to live) value included in an IP packet indicates:
(Multiple Choice)
4.7/5  (34)
(34)
Which PDU (protocol data unit) contains information necessary for handshaking (or session establishment) between two hosts?
(Multiple Choice)
4.8/5  (38)
(38)
MAC addresses are used at the _________ layer for addressing.
(Multiple Choice)
4.8/5  (30)
(30)
Temporary IP addresses are dynamically allocated by the _________ to requesting hosts.
(Multiple Choice)
4.9/5  (39)
(39)
The following figure demonstrates layer processing necessary to exchange data between two host computers. The device within the ellipse must be a _______. 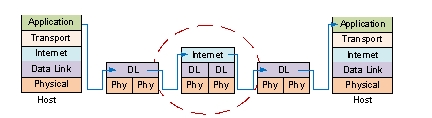
(Multiple Choice)
4.8/5  (36)
(36)
Which of the following is NOT a layer in the hybrid TCP/IP-OSI architecture?
(Multiple Choice)
4.9/5  (35)
(35)
Showing 1 - 20 of 40
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)