Exam 2: Cybersecurity: Fundamentals
Exam 1: Networking: Fundamental Concepts33 Questions
Exam 2: Cybersecurity: Fundamentals13 Questions
Exam 3: Essential Layers of Computer Networking40 Questions
Exam 4: Ip Address Planning and Management38 Questions
Exam 5: Intermediary Devices31 Questions
Exam 6: Wi-Fi and Cellular Network43 Questions
Exam 7: Ethernet Lan24 Questions
Exam 8: Cybersecurity: Threats23 Questions
Exam 9: Cybersecurity: Network and Host Protection19 Questions
Exam 10: Cybersecurity: Data Protection24 Questions
Exam 11: Fundamentals of Packet Routing29 Questions
Exam 12: Wide Area Network33 Questions
Exam 13: Physical Layer Data Transmissions19 Questions
Exam 14: Enterprise Network: LAN Topology, Routing, and Connectivity30 Questions
Select questions type
Below email is an example of _________: 
Free
(Multiple Choice)
4.7/5  (32)
(32)
Correct Answer:
D
Maintaining a reliable backup system of corporate database satisfies what aspect of security requirements?
Free
(Multiple Choice)
4.8/5  (36)
(36)
Correct Answer:
E
The following elements/activities cut across all security layers in realizing defense-in-depth EXCEPT:
Free
(Multiple Choice)
4.9/5  (37)
(37)
Correct Answer:
A
In realizing the defense-in-depth principle, the perimeter security technologies of a business organization include the following EXCEPT:
(Multiple Choice)
4.9/5  (31)
(31)
Which of the following is NOT a technology solution intended for authentication?
(Multiple Choice)
4.9/5  (31)
(31)
Maintaining data privacy achieves the _________ aspect of security requirement.
(Multiple Choice)
4.9/5  (41)
(41)
_____ is a process that validates "you are the person/system you claim to be."
(Multiple Choice)
4.7/5  (39)
(39)
The following technology solution represents an example of the 'simplicity' principle EXCEPT:
(Multiple Choice)
4.9/5  (34)
(34)
Which CORRECTLY pairs a security layer and an available technology in realizing the defense-in-depth principle?
(Multiple Choice)
4.8/5  (37)
(37)
The defense-in-depth principle may include security measures of the following layers. Which layer is LEAST relevant?
(Multiple Choice)
4.9/5  (34)
(34)
The following figure demonstrates the ________ principle in security. 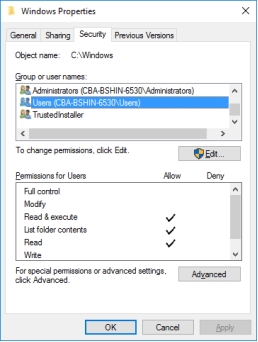
(Multiple Choice)
4.9/5  (45)
(45)
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)