Exam 11: Computer Crime and Information Security
Exam 1: Why Study Computers and Digital Technologies149 Questions
Exam 2: Hardware Designed to Meet the Need148 Questions
Exam 3: Software Solutions for Personal and Professional Gain147 Questions
Exam 4: The Internet and World Wide Web147 Questions
Exam 5: Telecommunications, Wireless Technologies, and Computer Networks148 Questions
Exam 6: Digital Media for Work and Leisure149 Questions
Exam 7: Database Systems147 Questions
Exam 8: E-Commerce149 Questions
Exam 9: Information, Decision Support, and Special-Purpose Systems146 Questions
Exam 10: Systems Development148 Questions
Exam 11: Computer Crime and Information Security150 Questions
Exam 12: Digital Society, Ethics, and Globalization148 Questions
Select questions type
A ____ protects secrets or proprietary information of individuals and organizations as long as it is adequately protected.
(Multiple Choice)
4.8/5  (39)
(39)
A social engineer may go junkyard diving; that is, rummaging through trash to steal credit card numbers or other personal information. _________________________
(True/False)
4.7/5  (33)
(33)
Passwords are considered the weakest form of authentication because they can be used by others to access systems without your knowledge.
(True/False)
4.9/5  (38)
(38)
____________________ has been defined as a security technique that uses high-level mathematical functions and computer algorithms to encode data so that it is unintelligible to all but the intended recipient.
(Short Answer)
4.8/5  (36)
(36)
Diana Andrews is in charge of keeping e-mail safe for the 400 employees of a mail order company. To increase employee awareness of security threats, Diana sends out a weekly e-zine with helpful updates.
-Today, Diana explains that ____ combine(s) both spoofed e-mail and a spoofed Web site in order to trick a person into providing private information.
(Multiple Choice)
4.9/5  (40)
(40)
A payroll program multiplying a person's pay rate by 2 for overtime instead of 1.5 is an example of ____.
(Multiple Choice)
4.8/5  (30)
(30)
Each time you use software, listen to music, read a book or newspaper article, or see a movie, you are enjoying someone else's physical property. _________________________
(True/False)
4.7/5  (39)
(39)
The most common cause of data loss, according to engineers at data recovery vendor Ontrack, is ____.
(Multiple Choice)
4.8/5  (47)
(47)
Voice recognition is sometimes classified as behaviormetrics rather than biometrics, since the analysis is based on the study of the manner in which a person speaks, which is a behavior rather than a physical trait.
(True/False)
4.9/5  (35)
(35)
There are three common forms of authentication. The first one is "Something you know." Please name the other two, and also give a brief description of all three forms.
(Essay)
4.7/5  (42)
(42)
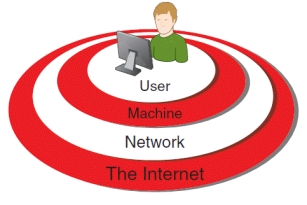 -The accompanying figure illustrates that the ____ level is the most important component of total information security.
-The accompanying figure illustrates that the ____ level is the most important component of total information security.
(Multiple Choice)
4.9/5  (30)
(30)
Every Wi-Fi adapter, the hardware used by computers to connect to Wi-Fi networks, has a unique ____ address that is usually printed on the adapter.
(Multiple Choice)
4.7/5  (39)
(39)
The system administrator is responsible for setting the access rights of users and for setting the permissions on system resources. _________________________
(True/False)
4.8/5  (35)
(35)
JoAnn is writing a paper on malicious spyware for her Mass Media and the Internet class. She has just started her first draft of the paper.
-JoAnn's school has firsthand experience with DDOS, so she explains that it is ____ that apply the power of many PCs to overwhelm Web sites and cause DDOS.
(Multiple Choice)
4.9/5  (39)
(39)
Facial ____________________ uses a mathematical technique to measure the distances between 128 points on the face.
(Short Answer)
4.9/5  (29)
(29)
Security vulnerabilities or security ____ are software bugs that allow violations of information security.
(Multiple Choice)
4.9/5  (39)
(39)
Connecting to the Internet increases risks ____ times that of a stand-alone computer.
(Multiple Choice)
4.9/5  (38)
(38)
Viruses and security attacks have decreased consistently each year.
(True/False)
4.9/5  (43)
(43)
 -Referring to the accompanying figure, as you move from the machine level to the network level to the Internet level, you face ____ exposure and risks.
-Referring to the accompanying figure, as you move from the machine level to the network level to the Internet level, you face ____ exposure and risks.
(Multiple Choice)
4.8/5  (31)
(31)
Today the most popular wireless protocol is ____________________.
(Short Answer)
4.9/5  (41)
(41)
Showing 101 - 120 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)