Exam 11: Computer Crime and Information Security
Exam 1: Why Study Computers and Digital Technologies149 Questions
Exam 2: Hardware Designed to Meet the Need148 Questions
Exam 3: Software Solutions for Personal and Professional Gain147 Questions
Exam 4: The Internet and World Wide Web147 Questions
Exam 5: Telecommunications, Wireless Technologies, and Computer Networks148 Questions
Exam 6: Digital Media for Work and Leisure149 Questions
Exam 7: Database Systems147 Questions
Exam 8: E-Commerce149 Questions
Exam 9: Information, Decision Support, and Special-Purpose Systems146 Questions
Exam 10: Systems Development148 Questions
Exam 11: Computer Crime and Information Security150 Questions
Exam 12: Digital Society, Ethics, and Globalization148 Questions
Select questions type
$264 million were reported lost to Internet fraud in 2008 in ____ alone.
(Multiple Choice)
4.8/5  (44)
(44)
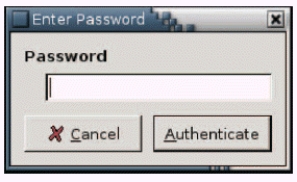 -The accompanying figure, showing an "Enter Password" dialog box, is an example of ____ security.
-The accompanying figure, showing an "Enter Password" dialog box, is an example of ____ security.
(Multiple Choice)
4.9/5  (42)
(42)
A ____ Trojan opens up ports on the computer to allow access to intruders.
(Multiple Choice)
4.7/5  (33)
(33)
Users do not have the power to set permission settings of the files they own.
(True/False)
4.8/5  (30)
(30)
Unlike speech recognition, voice recognition is not concerned with determining what words are being spoken, but with who is speaking them.
(True/False)
4.9/5  (28)
(28)
A ____ is a program that attaches itself to a file, spreads to other files, and delivers a destructive action.
(Multiple Choice)
4.7/5  (45)
(45)
Wireless communications can be encrypted by using Wired Equivalent Privacy (WEP) and ____.
(Multiple Choice)
4.8/5  (38)
(38)
Most software has an update feature that applies patches to ____ discovered in the software after release.
(Multiple Choice)
4.8/5  (33)
(33)
By default, the personal files and folders on both Windows Vista and Mac OS X computers are available to others on a network.
(True/False)
4.7/5  (38)
(38)
The three primary ways of keeping unregistered users out of a system include all of these EXCEPT ____.
(Multiple Choice)
4.9/5  (33)
(33)
Showing 141 - 150 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)