Exam 7: Security, Administration and Transaction Management
Exam 1: Introduction to Databases and Database Environment8 Questions
Exam 2: The Relational Model, Relational Algebra and Relational Calculus9 Questions
Exam 3: SQL: Data Manipulation and Advanced SQL18 Questions
Exam 4: Object-Relational DBMSs, Database Planning, Design, and Administration12 Questions
Exam 5: Entity-Relationship Modeling and Normalization19 Questions
Exam 6: Methodology-Conceptual Database Design and Methodology-Physical Database Design for Relational Databases9 Questions
Exam 7: Security, Administration and Transaction Management12 Questions
Exam 8: Query Processing8 Questions
Exam 9: Distributed DBMSs Concepts and Design10 Questions
Exam 10: Distributed DBMSs-Advanced Concepts and Object-Oriented DBMSs-Concepts and Design14 Questions
Exam 11: Object-Oriented DBMSs-Standards and Systems7 Questions
Exam 12: Web Technology and DBMSs, Semistructured Data and XML and Data Warehousing Concepts18 Questions
Exam 13: Data Warehousing Design15 Questions
Exam 14: OLAP and Data Mining11 Questions
Select questions type
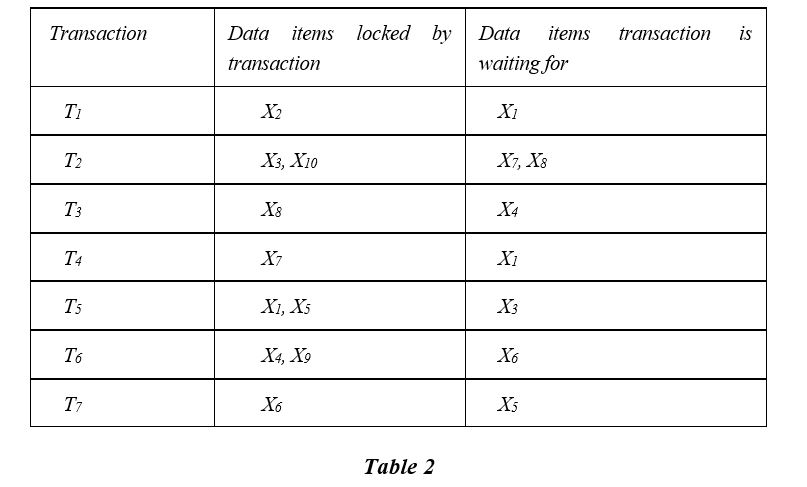
The locking information for several transactions is shown in Table 2. Produce a wait-for-graph (WFG) for the transactions and determine whether deadlock exists.
Free
(Essay)
4.9/5  (36)
(36)
Correct Answer:
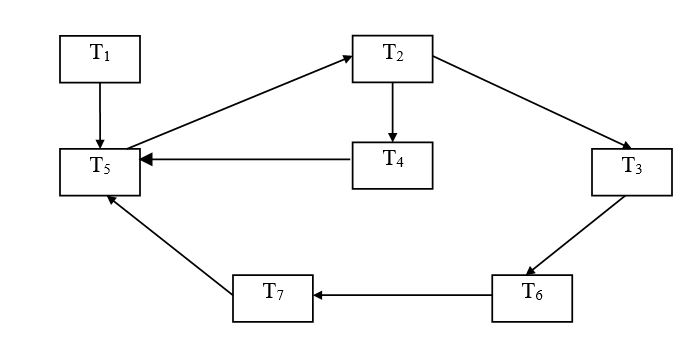
WFG will show that system is in deadlock.
Locking-based algorithms for concurrency control can be employed to synchronize the execution of transactions. Explain the rules for two-phase locking in a centralized Database Management System and why each of these is necessary to avoid the database becoming inconsistent.
Free
(Essay)
4.8/5  (39)
(39)
Correct Answer:
See Section 22.2.3.
Discuss the problems associated with microcomputer security, and contrast the measures required to provide a secure environment with those of a mainframe computing environment.
Free
(Essay)
4.9/5  (32)
(32)
Correct Answer:
The problems concern data security and physical security. Problems and precautions in dealing with these are generally as for part two of the previous question. It is important that a contrast is made with a mainframe environment. For example, in dealing with microcomputers, you are dealing with individual machines and staff, possibly over a wide location. Much of the responsibility rests with members of staff, consequently, all staff training is important. In the mainframe environment it is possible to set up centralized controls (physical and logical). Consequently, it should be an easier environment to control, with the responsibility residing in the IT manager.
(a) Locking-based algorithms for concurrency control can be employed to synchronize the execution of transactions. Explain what is meant by a serializable schedule and show that the following locking-based schedule is not serializable:
S = [wl1(y), wl2(y), R1(y), W1(y), R2(y), W2(y), rl1(y), rl2(y), wl2(z), R2(z), W2(z), rl2(z), C2,
wl1(z), R1(z), W1(z), rl1(z), C1]
where Ri(x)/Wi(x) indicates a read/write by transaction i on data item x
rli(x)/wli(x) indicates a release/write lock by transaction i on item x
Ci indicates a commit operation by transaction i.
(b) Identify the problem with the above schedule, and produce a correct locking-based serializable schedule.
(Essay)
4.7/5  (39)
(39)
Detail the types of problems associated with microcomputer security and the types of countermeasures that could be installed against loss.
(Essay)
4.9/5  (37)
(37)
A taxonomy of concurrency control algorithms can classify algorithms as pessimistic or optimistic. Compare and contrast these algorithms.
(Essay)
4.9/5  (36)
(36)
Explain the integrity features that a database management system may provide making reference to the system used, and indicate the disadvantages that arise where they are not available.
(Essay)
4.8/5  (35)
(35)
'One of the potential advantages of Distributed Database Management Systems is improved reliability and availability.'
(a) The consistency and reliability aspects of transactions are due to the 'ACIDity' properties of transactions. Discuss each of these properties and how they relate to the concurrency control and recovery mechanisms. Give examples to illustrate your answer.
(Essay)
4.9/5  (40)
(40)
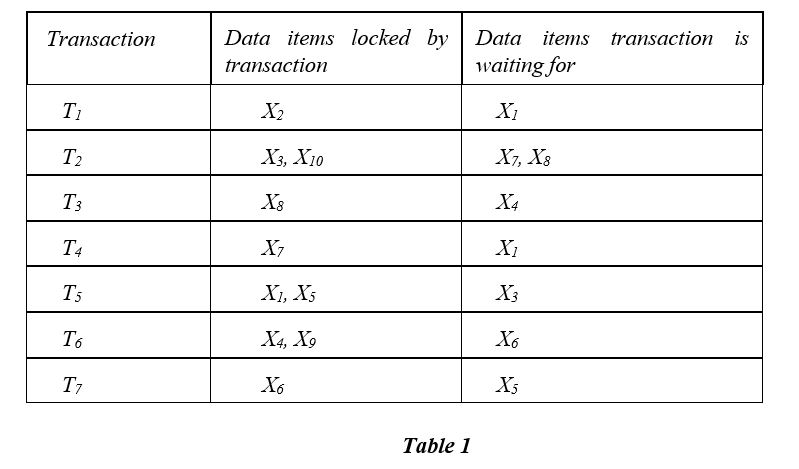
(a) Produce a wait-for-graph for the transactions with locking information shown in Table 1. What can you conclude for this graph?
 (b) Compare and contrast the approaches to deadlock management in database systems.
(b) Compare and contrast the approaches to deadlock management in database systems.
(Essay)
4.9/5  (42)
(42)
The increasing accessibility of databases on the Internet and intranets requires a reanalysis and extension of the normal approaches to security. Discuss some of the issues associated with the database system security in these environments.
(Essay)
4.7/5  (36)
(36)
Discuss the types of threat that might occur within the general database environment, and indicate the measures that could be taken to safeguard against them.
(Essay)
4.9/5  (33)
(33)
Describe a general plan of action for initiating a security policy, elaborating on each stage that might be undertaken.
(Essay)
4.8/5  (44)
(44)
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)