Exam 10: Distributed DBMSs-Advanced Concepts and Object-Oriented DBMSs-Concepts and Design
Give your definition of an Object-Oriented Database Management System (OODBMS). Discuss what you consider to be the three most important advantages of a DDBMS over a relational DBMS. Justify your selection of the three advantages.
See Sections 27.2 and 27.5. Expect some justification for the top three selection. Also expect detailed discussion of the advantages, not just bullet points.
Discuss why traditional transaction management protocols are too restrictive for advanced database applications.
• Conventional transaction management systems (TMSs) synchronize simple read and write operations. However, TMSs for advanced database applications must be able to deal with abstract operations. It may even be possible to improve concurrency by utilizing semantic knowledge about the objects and their abstract operations.
• Advanced database applications have different database access patterns than conventional database applications where the access is competitive (e.g., two users accessing the same bank account). Instead, sharing may be more cooperative as in the case, for example, multiple users accessing and working on the same design document. In this case, users accesses need to be synchronized, but users are willing to cooperate rather than compete for access to shared objects.
• Conventional transactions access 'flat' objects (e.g., pages, tuples) whereas transactions for advanced database applications may require synchronized access to composite and complex objects. Synchronization of access to such objects requires synchronization of access to the component objects.
• These applications require the support of long-duration transactions spanning hours, days or even weeks (e.g., working on a design object). Therefore, the transaction mechanism must support the sharing of partial results. Furthermore, to avoid the failure of partial tasks jeopardizing a long activity, it is necessary to distinguish between those activities that are essential for the completion of the transaction and those that are not, and to provide for alternative actions in case the primary activity fails.
• These applications may benefit from active capabilities for timely response to events and changes in the environment. This new database paradigm requires the monitoring of events and the execution of system triggered activities within running transactions.
(a) 'Pointer swizzling' is a technique that can be used to optimize access to main memory resident persistent objects. Discuss in general terms how pointer swizzling works.(b) Classify and evaluate the different approaches to pointer swizzling.(c) Briefly discuss any alternative approach that could be used to handle persistence in an ODBMS.
(a) The basic objective of pointer swizzling is to convert main memory pointers representing interobject references to disk pointers when an object is being written to disk and subsequently to convert disk pointers to main memory pointers when the object is being read back in again. Thus, the program language can access the interobject references as though they are normal pointers, thereby improving performance.
(b) Three dimensions:
(i) eager v. lazy
(ii) direct v. indirect
(iii) copy v. in-place
1. Eager: Guarantees that all the pointers in the main memory are swizzled. When an object is loaded from disk, the object is scanned through and all the pointers in the object are immediately swizzled.
2. Lazy: Only swizzles pointers on demand; i.e., a pointer is not swizzled until the object it refers to is accessed via this particular pointer.
Advantage is that that no pointers are swizzled unnecessarily. On negative side, lazy swizzling must handle two different kinds of pointers at run-time: swizzled and non-swizzled.
3. Direct: Requires that the referenced object be resident in memory. A directly swizzled pointer contains the main memory address of the object it references.
Problem is that if an object is displaced from the system buffer (i.e., is no longer resident) all the directly swizzled objects that reference the displaced object need to be unswizzled.
In the case of eager direct swizzling, one cannot simply unswizzle pointers because eager swizzling guarantees that all pointers in the buffer are swizzled. Instead, these pointers (i.e., their home objects) must be displaced too - possible snowball effect.
4. Indirect: Permits the swizzling of pointers that reference non-resident objects.
Induces an additional overhead when it comes to simple object lookups - leads to an additional level of indirection (due to existence of a descriptor that stores the main memory address of object) and to a residency check, a check of whether the descriptor is valid or not. For direct swizzling, the information that an object is resident is coded in the swizzled pointer.
5. Copy: When faulting objects in, data is copied into the application's local object cache.
6. In-place: When faulting objects in, data is accessed within the data manager's cache.
Copy swizzling may be more efficient as, in worst case, only modified objects have to be swizzled back to their OIDs, whereas with in-place may have to unswizzle an entire page of objects if one object on the page is modified. On other hand, with copy approach, every object must be explicitly copied into the local object cache.
(c) Several alternative strategies (e.g.):
• Leave it to user.
• Map to relational system
• Use a one pointer strategy that leaves it to the run-time system to determine whether object is transient or volatile. Could trap references to persistent objects, for example, by using illegal values such as negative values for pointers to persistent objects.
Object databases have roots in both programming languages and database management. However, not all aspects of these two technologies blend together easily. One area of potential conflict arises when we try to completely separate persistence and type.
(a) Define the orthogonality of persistence and type.
(b) Discuss this issue for any three of the following subsystems:
(1) Queries
(2) Schemas
(3) Transactions
(4) Existence Semantics.
Case Study - Library System
The librarian will access the system to issue books, record reservations, generate return requests for reserved books and record books being returned. Returning a book may involve generating an availability notification if the returned book has been reserved by another member. If an availability notification is generated then the librarian sends it out to the member. When a book is requested to be issued or requested to be reserved then the system validates details on the membership card as well as validating that the requested book is one stocked by the library. If the membership card is invalid or the library does not stock the book then the request is rejected. If a book is requested for issue but is on-loan then that book will be reserved. Members of the library can display details of books stocked. The subscriptions section deals with membership issues e.g. renewing membership cards on an annual basis etc. The purchasing section deals with adding new books to the library.
There may be multiple copies of books held in the library. When a book is borrowed the borrowing date is noted and when the book is returned the return date is noted. The details held about each reservation include who the current borrower(s) is and who has reserved the book.
When a copy of a book arrives from the suppliers, it is held in storage until its details are registered on the system. These details include the number, author and title of the book. Once registered the copy is put in the lending shelf which means that it is available to be borrowed. When a copy is returned, if the book has been reserved then the copy is held in a reservation area otherwise it is returned to the lending shelf. If a copy is reported lost by the borrower then the copy details are deleted from the system by the librarian.
A reservation
Reservation
Number:
Date:
Book
Number:
Title:
Author:
Reserver
Number:
Name:
Address:
Current Borrower
Number:
Name:
Address:
-Produce use case diagrams and a set of associated sequence diagrams for the above case study.
Despite the superior expressive power of the Object-Oriented Database Management System (OODBMS) in comparison to the established relational systems, the acceptance of the OODBMS will ultimately depend on its performance. The key to this may well lie with how persistent objects are accessed. Discuss the design goals for the incorporation of persistence in a programming language.
Under the three-phase commit protocol, discuss how the coordinator and participants would recover following a failure. Consideration should be given to the various stages of the commit protocol.
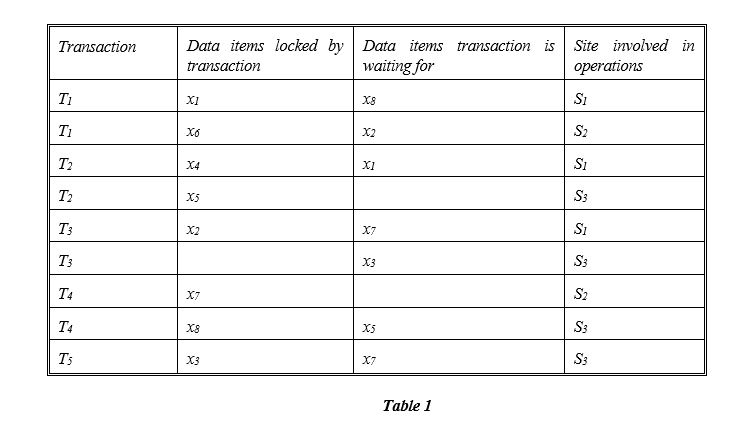
Using the above transactions, demonstrate how Obermarck's method for distributed deadlock detection works.
One of the most well-known methods for distributed deadlock detection was developed by Obermarck. Explain how Obermarck's method works and how deadlock is detected and resolved.
Discuss the concept of object identifiers (OIDs) in an object DBMS and discuss four different approaches for the representation of OIDs.
Consider six transactions T1, T2, T3, T4, and T5 with:
- T1 initiated at site S1 and spawning an agent at site S2,
- T2 initiated at site S3 and spawning an agent at site S1,
- T3 initiated at site S1 and spawning an agent at site S3,
- T4 initiated at site S2 and spawning an agent at site S3,
- T5 initiated at site S3.
The locking information for these transactions is shown in Table 1. Produce the local wait-for-graphs (WFGs) for each of the sites. What can you conclude from the local WFGs?
The centralized two-phase commit protocol uses a series of timeouts to prevent unnecessary blocking. Discuss the actions for both coordinator and participants when a timeout occurs. Consideration should be given to the various stages of the commit protocol.
(a) Discuss why traditional transaction management protocols are too restrictive for advanced database applications.(b) 'Only Object-Oriented Database Management Systems can support alternative transaction management protocols effectively.' Discuss the validity of this statement.
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)