Exam 14: Privacy and Ethical Considerations in Information Management
Green computing is often associated with supporting the triple bottom line known as:
A
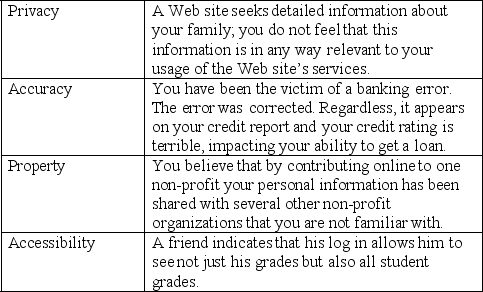
Match the situation below with the area of information control it falls under.
Give reasons why users are so willing to forgo privacy on the Internet.
Users often forgo privacy on the Internet for several reasons, which can be broadly categorized into convenience, social connectivity, lack of awareness, and incentives. Here's a detailed look at each of these factors:
1. **Convenience**: Many online services offer significant convenience to users, such as the ability to shop from home, manage finances, or access a wealth of information and entertainment. To take full advantage of these services, users are often required to provide personal information. The trade-off between personal privacy and convenience is one that many users are willing to make, prioritizing immediate benefits over potential long-term privacy concerns.
2. **Social Connectivity**: Social media platforms encourage users to share personal information to connect with friends, family, and colleagues. The desire to be part of a community and stay connected with others can lead users to disclose more information than they might otherwise be comfortable with, often without considering the privacy implications.
3. **Lack of Awareness**: Many users are not fully aware of the extent to which their personal information can be collected, shared, and used by third parties. Without a clear understanding of the risks and the value of their personal data, users may not take the necessary precautions to protect their privacy online.
4. **Incentives**: Companies often offer incentives for users to share personal information. This can include discounts, personalized services, or access to exclusive content. These incentives can be persuasive, leading users to share more information than they would in the absence of such rewards.
5. **Default Settings and Design Choices**: Websites and applications often use default settings that favor data sharing, and users may not take the initiative to change these settings. Additionally, the design of online services can make it difficult to navigate privacy settings or understand the implications of certain choices.
6. **Trust in Institutions**: Some users trust that the companies collecting their data will protect it and use it responsibly. This trust, whether well-founded or not, can make users more comfortable with sharing personal information.
7. **Normalization of Sharing**: In the digital age, sharing personal information has become normalized. As people see others sharing their lives online, it can reduce the perceived risk or concern associated with giving up privacy.
8. **Resignation**: Some users believe that privacy is already lost or that they have no control over their data. This sense of resignation can lead to a lack of effort in protecting privacy, as users accept that giving up their personal information is an unavoidable part of using the Internet.
9. **Ignorance of Alternatives**: Users may not be aware of privacy-focused alternatives to popular services, or they may find that these alternatives do not meet their needs as effectively. Consequently, they stick with the more mainstream options, which often require giving up more privacy.
10. **Psychological Factors**: The immediate gratification of receiving likes, comments, and other forms of social validation can outweigh privacy concerns. Users may prioritize the positive feelings associated with online engagement over the potential negative consequences of privacy loss.
In summary, the willingness to forgo privacy on the Internet is a complex issue influenced by a variety of factors, including the perceived benefits of online services, social pressures, a lack of understanding about privacy risks, and the psychological effects of online interactions.
Give an example of U.S. legislature designed to ensure the privacy and protection of information for a specific industry.
Explain how green computing can satisfy each of the three normative theories of business ethics.
The European Union Directive on Data Protection does all of the following EXCEPT:
How does the European Union approach data protection differently than the United States?
Matching
Green computing is a passing phase and will likely be less strategic to companies in the very near future.
In today's digital word, individuals can control their privacy through ______, consent, and correction.
This theory of normative business ethics seeks to create value for people in a manner that is just and nondiscriminatory.
Which normative theory of business ethics would TJX have displayed if it had informed customers as soon as the breach was corrected and told other retailers how to prevent future security breaches?
The European Union relies on a government data protection agency and specific privacy protection standards outlined in the ___________.
Those who possess the "best" information and know how to use it, win.
Unlike the European Union, the U.S. has no general legislature ensuring Internet privacy rights. Instead, the U.S. encourages self-regulation and has introduced industry-specific regulations as needed.
An Internet web site that wishes to abide by fair privacy practices will do all of the following EXCEPT:
The concern about privacy on Facebook and other social media sites is greater in the U.S. than it is in Europe.
All of the following are examples of green computing EXCEPT:
TJX's handling of its serious data breach is consistent with which one of the following?
Today's managers must ensure that information about their employees and customers is only available to those who have a right to see it and use it, an issue referred to as:
The Stakeholder theory requires managers to pursue projects in ways that are compatible with the well-being of society.
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)