Exam 7: The Web and E-Mail
Exam 1: Computers and Digital Basics147 Questions
Exam 2: Computer Hardware150 Questions
Exam 3: Software149 Questions
Exam 4: Operating Systems and File Management150 Questions
Exam 5: Local Area Networks150 Questions
Exam 6: The Internet149 Questions
Exam 7: The Web and E-Mail150 Questions
Exam 8: Digital Media150 Questions
Exam 9: The Computer Industry: History, careers, and Ethics150 Questions
Exam 10: Information Systems Analysis and Design150 Questions
Exam 11: Databases150 Questions
Exam 12: Computer Programming150 Questions
Select questions type
Melissa has decided to obtain an e-mail account. Although she plans to use the e-mail account to communicate with her many friends, her main purpose in establishing it is to aid in the search for a job. She has a list of e-mail addresses for a group of potential employers. Melissa intends to e-mail her resume, along with a general message, to each of them. She will use the same message for all recipients.
-Melissa is planning to travel a great deal in the coming weeks.She will not be taking her computer with her,but knows that the hotels she will be staying at have business centers with Internet-enabled computers.She plans to access her e-mail account every day so that she can quickly respond should she be contacted by a prospective employer.Which one of the following account types should she use?
(Multiple Choice)
4.8/5  (40)
(40)
The file name for a Web site's main page,like www.cnn.com,is usually short and to the point._________________________
(True/False)
4.9/5  (27)
(27)
A Web server's response to a browser's request includes an HTTP ____ that indicates whether the browser's request could be fulfilled.
(Multiple Choice)
4.8/5  (36)
(36)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-An exploit that redirects users to fake sites by poisoning a domain name server with a false IP address
(Multiple Choice)
4.9/5  (35)
(35)
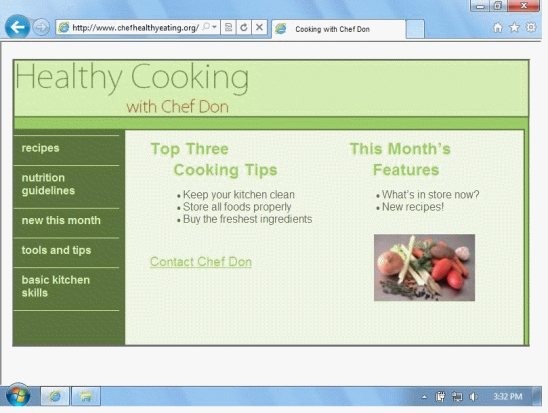 -The image of the vegetables in the accompanying figure is produced by a(n)____ HTML tag when the Web page is displayed by a browser.
-The image of the vegetables in the accompanying figure is produced by a(n)____ HTML tag when the Web page is displayed by a browser.
(Multiple Choice)
4.8/5  (41)
(41)
Melissa has decided to obtain an e-mail account. Although she plans to use the e-mail account to communicate with her many friends, her main purpose in establishing it is to aid in the search for a job. She has a list of e-mail addresses for a group of potential employers. Melissa intends to e-mail her resume, along with a general message, to each of them. She will use the same message for all recipients.
-Melissa is concerned about the security of her computer,and she wants to avoid malicious exploits,which can work their way into her computer through various security holes.Which type of e-mail service has been the target of many such exploits?
(Multiple Choice)
4.8/5  (34)
(34)
The term ____________________ was first used in the mid-1960s to describe a computer system that could store literary documents,link them according to logical relationships,and allow readers to comment and annotate what they read.
(Short Answer)
4.8/5  (37)
(37)
A(n)____ is a collection of related information organized and formatted so it can be accessed using software called a browser.
(Multiple Choice)
5.0/5  (36)
(36)
ActiveX controls use digital licenses to increase their security by including an electronic attachment to a file that verifies the identity of its source._________________________
(True/False)
4.7/5  (35)
(35)
In a(n)POP3 e-mail system,your messages remain on a Web server,rather than being downloaded to your computer._________________________
(True/False)
4.7/5  (33)
(33)
Which of the following Web-based applications is NOT sometimes characterized as Web 2.0?
(Multiple Choice)
5.0/5  (40)
(40)
Which of the following checks a Web server's security certificate to determine if the site is legitimate?
(Multiple Choice)
4.9/5  (36)
(36)
Web 3.0 refers to innovations like cloud computing and other new technologies likely to further change the way we use the Web._________________________
(True/False)
4.9/5  (45)
(45)
A(n)____________________ is a cyberspace version of the metal cart you wheel around a store and fill up with merchandise.
(Short Answer)
4.9/5  (38)
(38)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Software program that runs on your computer and helps you access Web pages
(Multiple Choice)
4.8/5  (33)
(33)
When you purchase a textbook online from a site like www.amazon.com,you are participating in ____ e-commerce.
(Multiple Choice)
4.8/5  (41)
(41)
Online auctions are examples of B2G e-commerce._________________________
(True/False)
4.8/5  (40)
(40)
Showing 61 - 80 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)