Exam 7: The Web and E-Mail
Exam 1: Computers and Digital Basics147 Questions
Exam 2: Computer Hardware150 Questions
Exam 3: Software149 Questions
Exam 4: Operating Systems and File Management150 Questions
Exam 5: Local Area Networks150 Questions
Exam 6: The Internet149 Questions
Exam 7: The Web and E-Mail150 Questions
Exam 8: Digital Media150 Questions
Exam 9: The Computer Industry: History, careers, and Ethics150 Questions
Exam 10: Information Systems Analysis and Design150 Questions
Exam 11: Databases150 Questions
Exam 12: Computer Programming150 Questions
Select questions type
When you use a search engine,it stores all of the following information about your query EXCEPT ____.
(Multiple Choice)
4.9/5  (36)
(36)
Server-side scripts can be written using any of the following EXCEPT ____.
(Multiple Choice)
4.9/5  (40)
(40)
Give two reasons why it is important to upgrade your browser when a new version becomes available.
(Essay)
4.8/5  (34)
(34)
Web ____________________ software provides tools specifically designed to enter and format Web page text,graphics,and links.
(Short Answer)
4.9/5  (34)
(34)
Elizabeth has to conduct a series of Internet searches to collect information for a number of research papers she is writing. After much trial and error, she is finding that there are efficient and precise ways to do these searches.
-For the next search,she wants only Web pages containing the complete phrase "Mars exploration." Which search operator should she use to formulate her query?
(Multiple Choice)
4.7/5  (35)
(35)
 -In the URL found in the accompanying figure,http is the ____.
-In the URL found in the accompanying figure,http is the ____.
(Multiple Choice)
4.7/5  (45)
(45)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Unwanted electronic junk mail about,say,medical products,low-cost loans,and fake software upgrades that arrives in your online mailbox
(Multiple Choice)
4.8/5  (29)
(29)
Elizabeth has to conduct a series of Internet searches to collect information for a number of research papers she is writing. After much trial and error, she is finding that there are efficient and precise ways to do these searches.
-Her first search is for pages that include the term "railroad history," but she is not interested in "cars." What search operator should she use to precede the keyword "cars"?
(Multiple Choice)
4.9/5  (29)
(29)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-An e-mail based scam that is designed to persuade you to reveal confidential information
(Multiple Choice)
4.8/5  (37)
(37)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Represents one end of a connection
(Multiple Choice)
4.8/5  (34)
(34)
A(n)ActiveX control is a compiled computer program that can be referenced from within an HTML document,downloaded,installed on your computer,and executed within a browser window._________________________
(True/False)
4.8/5  (34)
(34)
The popular term for unwanted electronic junk mail about medical products,low-cost loans,and fake software upgrades that arrives in your online mailbox is ____________________.
(Short Answer)
5.0/5  (34)
(34)
For HTTP,____ usually are associated with port 80 on the client and server.
(Multiple Choice)
4.9/5  (35)
(35)
____________________ is an exploit that redirects users to fake sites by poisoning a domain name server with a false IP address.
(Short Answer)
4.8/5  (42)
(42)
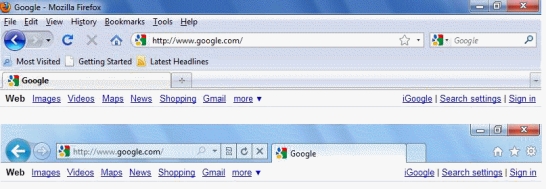 -The applications shown in the accompanying figure are examples of Web browsers._________________________
-The applications shown in the accompanying figure are examples of Web browsers._________________________
(True/False)
4.8/5  (40)
(40)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Maintains no record of previous interactions
(Multiple Choice)
4.9/5  (49)
(49)
____ software is a type of security software designed to identify and neutralize Web bugs,ad-serving cookies,and other types of malware.
(Multiple Choice)
4.9/5  (41)
(41)
A(n)____ is a series of instructions that is embedded directly into an HTML document that instruct the browser to carry out specific actions or to respond to specific user actions.
(Multiple Choice)
4.8/5  (41)
(41)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Used by individuals who prefer not to leave a trail of their Internet activities
(Multiple Choice)
4.8/5  (38)
(38)
Mark is interested in Internet e-commerce security issues. His friend Amelia runs a small B2C site that sells vintage clothing. He discusses the topic with Amelia, and he learns about ActiveX controls, and how browsers and Web servers communicate with each other.
-To identify the creator of an ActiveX control,Amelia tells Mark that he should look at the control's ____.
(Multiple Choice)
4.9/5  (43)
(43)
Showing 101 - 120 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)