Exam 9: Network and Internet Security
Exam 1: Introduction to the World of Computers100 Questions
Exam 2: The System Unit: Processing and Memory100 Questions
Exam 3: Storage100 Questions
Exam 4: Input and Output100 Questions
Exam 5: System Software: Operating Systems and Utility Programs100 Questions
Exam 6: Application Software100 Questions
Exam 7: Computer Networks100 Questions
Exam 8: The Internet and the World Wide Web100 Questions
Exam 9: Network and Internet Security100 Questions
Exam 10: Multimedia and the Web100 Questions
Exam 11: E-Commerce100 Questions
Exam 12: Information Systems and System Development100 Questions
Exam 13: Program Development and Programming Languages100 Questions
Exam 14: Databases and Database Management Systems100 Questions
Exam 15: Computer Security and Privacy100 Questions
Exam 16: Intellectual Property Rights, Ethics, Health, Access, and the Environment100 Questions
Select questions type
One of the biggest disadvantages of password-based systems is that passwords can be forgotten.
(True/False)
4.9/5  (33)
(33)
A group of bots that are controlled by one individual and can work together in a coordinated fashion is called a(n)____________________.
(Short Answer)
4.9/5  (42)
(42)
____________________ is a way of temporarily converting data into a form,known as a cipher,that cannot easily be understood in order to protect that data from being viewed by unauthorized people.
(Short Answer)
4.7/5  (34)
(34)
Fortunately,identity theft is declining and does not pose a real danger to individuals today.
(True/False)
4.7/5  (44)
(44)
____ are acts of malicious destruction to a computer or computer resource.
(Multiple Choice)
4.7/5  (44)
(44)
Typically,____________________ begins with obtaining a person's name and Social Security number,often from a credit application,rental application,or similar form.
(Short Answer)
5.0/5  (31)
(31)
Unauthorized use involves using a computer resource for unauthorized activities.
(True/False)
4.9/5  (28)
(28)
A type of computer infection occurs when a hacker breaches a computer system in order to delete data,change data,modify programs,or otherwise alter the data and programs located there.
(True/False)
4.7/5  (45)
(45)
____ identify users by a particular unique biological characteristic.
(Multiple Choice)
4.8/5  (33)
(33)
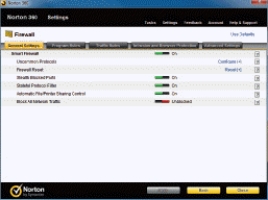 -A(n)____________________,such as the one shown in the accompanying figure,is a security system that essentially creates a barrier between a computer or a network and the Internet in order to protect against unauthorized access.
-A(n)____________________,such as the one shown in the accompanying figure,is a security system that essentially creates a barrier between a computer or a network and the Internet in order to protect against unauthorized access.
(Short Answer)
4.9/5  (33)
(33)
Case 9-2
Fernando has been having problems with his computer.He takes it to his local computer repair shop to be checked and finds out that his computer has a number of malware that he was not even aware of.
-The technician also found a ____ on the computer,which is designed to find sensitive information about the user located on the PC and then send it to the malware creator.The technician explains that this type of malware cannot replicate itself.
(Multiple Choice)
4.9/5  (43)
(43)
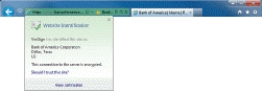 -The green color of the Address bar in the accompanying figure indicates that the site is using a valid ____ SSL certificate.
-The green color of the Address bar in the accompanying figure indicates that the site is using a valid ____ SSL certificate.
(Multiple Choice)
5.0/5  (32)
(32)
A computer that is controlled by a hacker or other computer criminal is referred to as a ____.
(Multiple Choice)
4.7/5  (34)
(34)
A booming area of computer crime involves online fraud,theft,scams,and related activities collectively referred to as ____.
(Multiple Choice)
4.7/5  (43)
(43)
One emerging type of Trojan horse is called a ____-Access Trojan.
(Multiple Choice)
4.7/5  (38)
(38)
____ occurs when someone obtains enough information about a person to be able to masquerade as that person for a variety of activities-usually to buy products or services in that person's name.
(Multiple Choice)
4.9/5  (32)
(32)
To avoid the need to obtain the recipient's public key before sending that person an encrypted e-mail,proprietary encrypted e-mail can be used.
(True/False)
4.9/5  (29)
(29)
Showing 81 - 100 of 100
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)