Exam 9: Network and Internet Security
Exam 1: Introduction to the World of Computers100 Questions
Exam 2: The System Unit: Processing and Memory100 Questions
Exam 3: Storage100 Questions
Exam 4: Input and Output100 Questions
Exam 5: System Software: Operating Systems and Utility Programs100 Questions
Exam 6: Application Software100 Questions
Exam 7: Computer Networks100 Questions
Exam 8: The Internet and the World Wide Web100 Questions
Exam 9: Network and Internet Security100 Questions
Exam 10: Multimedia and the Web100 Questions
Exam 11: E-Commerce100 Questions
Exam 12: Information Systems and System Development100 Questions
Exam 13: Program Development and Programming Languages100 Questions
Exam 14: Databases and Database Management Systems100 Questions
Exam 15: Computer Security and Privacy100 Questions
Exam 16: Intellectual Property Rights, Ethics, Health, Access, and the Environment100 Questions
Select questions type
It is important to select strong passwords and change them frequently.
(True/False)
4.8/5  (41)
(41)
Biometric authentication uses information that an individual should know or can easily remember.
(True/False)
4.8/5  (31)
(31)
A(n)____________________ access system is an identification system that requires the individual requesting access to provide information that only the authorized user is supposed to know.
(Short Answer)
4.7/5  (38)
(38)
Information used in identity theft can be obtained by skimming or via social engineering.
(True/False)
4.8/5  (30)
(30)
When a digitally signed document is received,the recipient's computer uses the sender's ____ key to verify the digital signature.
(Multiple Choice)
5.0/5  (39)
(39)
Writing a computer virus or other type of malware or even posting the malware code on the Internet is not illegal,but it is considered highly unethical and irresponsible behavior.
(True/False)
4.8/5  (29)
(29)
A(n)denial of service (DoS)attack is an act of sabotage that attempts to flood a network server or Web server with so many requests for action that it cannot handle legitimate requests any longer.
(True/False)
4.8/5  (41)
(41)
Case 9-2
Fernando has been having problems with his computer.He takes it to his local computer repair shop to be checked and finds out that his computer has a number of malware that he was not even aware of.
-The technician tells Fernando that his computer has a ____,which might have gotten into Fernando's computer when he downloaded a free computer game from the Internet.
(Multiple Choice)
4.9/5  (41)
(41)
To protect yourself against ____________________ and other types of online harassment,use gender-neutral,nonprovocative identifying names.
(Short Answer)
4.8/5  (36)
(36)
____ can be extremely distressing for victims,can take years to straighten out,and can be very expensive.
(Multiple Choice)
4.8/5  (34)
(34)
____,the most commonly used type of possessed knowledge,are secret words or character combinations associated with an individual.
(Multiple Choice)
4.9/5  (38)
(38)
The ____,implemented in 2001,grants federal authorities expanded surveillance and intelligence-gathering powers,such as broadening their ability to obtain the real identity of Internet users and to intercept Internet communications.
(Multiple Choice)
4.8/5  (46)
(46)
Possessed knowledge access systems use physical objects for identification purposes and are frequently used to access facilities and computer systems.
(True/False)
4.8/5  (28)
(28)
Like a computer virus,a ____ is a malicious program designed to cause damage.
(Multiple Choice)
4.8/5  (43)
(43)
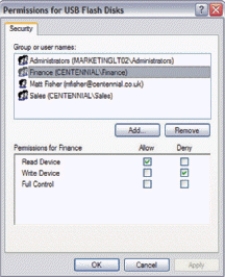 -____ software,such as that shown in the accompanying figure,can control which devices can be connected to an employee's computer.
-____ software,such as that shown in the accompanying figure,can control which devices can be connected to an employee's computer.
(Multiple Choice)
4.8/5  (35)
(35)
Showing 21 - 40 of 100
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)