Exam 10: Information Systems Controls for Systems Reliability Part 3: Processing Integrity and Availability
Exam 1: Accounting Information Systems: an Overview79 Questions
Exam 2: Overview of Transaction Processing and Erp Systems74 Questions
Exam 3: Systems Documentation Techniques83 Questions
Exam 4: Relational Databases80 Questions
Exam 5: Computer Fraud46 Questions
Exam 6: Computer Fraud and Abuse Techniques45 Questions
Exam 7: Control and Accounting Information Systems96 Questions
Exam 8: Information Systems Controls for System Reliability Part 1: Information Security53 Questions
Exam 9: Information Systems Controls for Systems Reliability Part 2: Confidentiality and Privacy24 Questions
Exam 10: Information Systems Controls for Systems Reliability Part 3: Processing Integrity and Availability63 Questions
Exam 11: Auditing Computer-Based Information Systems72 Questions
Exam 12: The Revenue Cycle: Sales to Cash Collections81 Questions
Exam 13: The Expenditure Cycle: Purchasing to Cash Disbursements83 Questions
Exam 14: The Production Cycle68 Questions
Exam 15: The Human Resources Management and Payroll Cycle58 Questions
Exam 16: General Ledger and Reporting System57 Questions
Exam 17: The Rea Data Model61 Questions
Exam 18: Implementing an Rea Model in a Relational Database68 Questions
Exam 19: Special Topics in Rea Modeling72 Questions
Exam 20: Introduction to Systems Development Systems Analysis90 Questions
Exam 21: Ais Development Strategies73 Questions
Exam 22: Systems Design, implementation, and Operation70 Questions
Select questions type
Chaz Finnerty called the IT Help Desk in a huff."I'm trying to open an Excel file and I get a message that says that the file is locked for editing.What's going on?" The answer is likely that
Free
(Multiple Choice)
4.8/5  (45)
(45)
Correct Answer:
C
If invoices are processed in groups of fifty,which fields from the document shown below would not be used to create a hash control total? 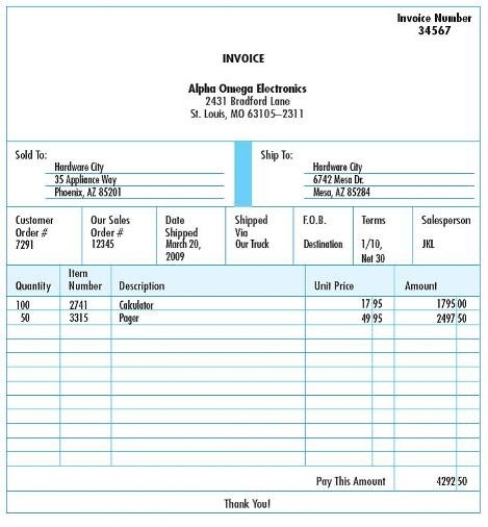
Free
(Multiple Choice)
4.9/5  (30)
(30)
Correct Answer:
A
A specific inventory record indicates that there were 12 items on hand before a customer brings two of the items to the check stand to be purchased.The cashier accidentally entered quantity 20 instead of 2.Which data entry control would best have prevented this error?
(Multiple Choice)
4.7/5  (45)
(45)
This control entails verifying that the proper number of bits are set to the value 1 in each character received.
(Multiple Choice)
4.8/5  (45)
(45)
________ copies all changes made since the last full backup.
(Multiple Choice)
4.8/5  (44)
(44)
When I enter a correct customer number,the data entry screen displays the customer name and address.This is an example of
(Multiple Choice)
4.9/5  (36)
(36)
The accounting department at Synergy Hydroelectric records an average of 10,000 transactions per hour.By cost-benefit analysis,managers have concluded that the maximum acceptable loss of data in the event of a system failure is 40,000 transactions.The firm's recovery point objective is therefore
(Multiple Choice)
4.8/5  (41)
(41)
This tests a numerical amount to ensure that it does not exceed a predetermined value.
(Multiple Choice)
4.7/5  (42)
(42)
The best example of a hash total for a payroll transaction file could be
(Multiple Choice)
4.9/5  (30)
(30)
A computer operator accidentally used the wrong master file when updating a transaction file.As a result,the master file data is now unreadable.Which control could best have prevented this from happening?
(Multiple Choice)
4.9/5  (35)
(35)
The maximum acceptable down time after a computer system failure is determined by a company's
(Multiple Choice)
4.7/5  (30)
(30)
The accounting department at Synergy Hydroelectric records an average of 12,500 transactions per hour.By cost-benefit analysis,managers have concluded that the maximum acceptable loss of data in the event of a system failure is 25,000 transactions.The firm's recovery point objective is therefore
(Multiple Choice)
4.9/5  (29)
(29)
Modest Expectations Investment Services (MEIS)allows customers to manage their investments over the Internet.If customers attempt to sell more shares of a stock than they have in their account,an error message is displayed.This is an example of a
(Multiple Choice)
4.8/5  (41)
(41)
This tests a numerical amount to ensure that it does not exceed a predetermined value nor fall below another predetermined value.
(Multiple Choice)
4.9/5  (32)
(32)
Showing 1 - 20 of 63
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)