Exam 12: Managing Systems Support and Security
Exam 1: Introduction to Systems Analysis and Design80 Questions
Exam 2: Analyzing the Business Case81 Questions
Exam 3: Managing Systems Projects78 Questions
Exam 4: Requirements Modeling98 Questions
Exam 5: Data and Process Modeling84 Questions
Exam 6: Object Modeling78 Questions
Exam 7: Development Strategies82 Questions
Exam 8: User Interface Design82 Questions
Exam 9: Data Design86 Questions
Exam 10: System Architecture78 Questions
Exam 11: Managing Systems Implementation81 Questions
Exam 12: Managing Systems Support and Security81 Questions
Exam 13: Appendix-The Systems Analyst’s Toolkit45 Questions
Exam 14: CASE Tools45 Questions
Exam 15: Financial Analysis Tools45 Questions
Exam 16: Internet Resource Tools44 Questions
Select questions type
A(n) _____ can prevent an unauthorized person from booting a computer by using a CD-ROM or USB device.
(Multiple Choice)
4.7/5  (46)
(46)
_____ costs include expenses for items such as supplies, equipment rental, and software leases.
(Multiple Choice)
4.9/5  (35)
(35)
As enterprise-wide information systems grow more complex, configuration management becomes trivial.
(True/False)
5.0/5  (35)
(35)
The first step in managing IT security is to develop a _____ based on confidentiality, integrity, and availability.
(Multiple Choice)
4.8/5  (34)
(34)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-Combination of hardware and software that allows computers to interact with a network
(Multiple Choice)
4.9/5  (36)
(36)
Wrapping refers to the practice of storing backup media away from the main business location, in order to mitigate the risk of a catastrophic disaster, such as a flood, fire, or earthquake.
(True/False)
4.8/5  (28)
(28)
When a new version of a system is installed, the prior release is _____, or stored.
(Multiple Choice)
4.9/5  (35)
(35)
As another one of his responsibilities, George captures information from clients about attacks they have borne and from their description, he identifies the kind of attack they have experienced.
-Another of George's clients describes a situation in which a caller to their service desk pretended to be a legitimate user and requested that his password to his company account be changed. How does George categorize this incident?
(Multiple Choice)
4.7/5  (38)
(38)
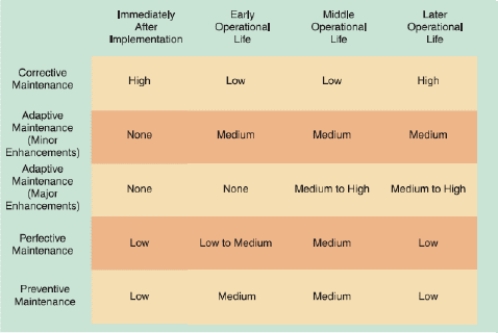 -As shown in the accompanying figure, near the end of a system's useful life, _____ when it becomes clear that a company plans to replace the system.
-As shown in the accompanying figure, near the end of a system's useful life, _____ when it becomes clear that a company plans to replace the system.
(Multiple Choice)
4.8/5  (36)
(36)
To measure system performance, companies use _____, which uses a set of standard tests on one system to compare its performance and capacity to that of other systems.
(Multiple Choice)
4.7/5  (37)
(37)
In addition to benchmark testing, performance measurements, called _____, can monitor the number of transactions processed in a given time period, the number of records accessed, and the volume of online data.
(Multiple Choice)
4.9/5  (43)
(43)
A _____ is a formal reference point that measures system characteristics at a specific time.
(Multiple Choice)
4.8/5  (31)
(31)
As another one of his responsibilities, George captures information from clients about attacks they have borne and from their description, he identifies the kind of attack they have experienced.
-One of George's clients reports that the traffic on their network is being intercepted and scanned for valuable information. How does George categorize this incident?
(Multiple Choice)
4.7/5  (27)
(27)
_____ analyzes an organization's assets, threats, and vulnerabilities.
(Multiple Choice)
4.7/5  (36)
(36)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-Hostile act that targets systems or a company itself
(Multiple Choice)
4.9/5  (24)
(24)
In maintenance management, _____ involves studying the parts of a system to understand the overall system.
(Multiple Choice)
4.9/5  (31)
(31)
_____, a risk control strategy, eliminates risks by adding protective safeguards.
(Multiple Choice)
4.8/5  (33)
(33)
If significant changes take place in an existing system or if a new version is released, the IT department might develop a _____.
(Multiple Choice)
5.0/5  (41)
(41)
_____ is a process for controlling changes in system requirements during software development.
(Multiple Choice)
4.8/5  (43)
(43)
The systems support and _____ phase begins when a system becomes operational and continues until the system reaches the end of its useful life.
(Multiple Choice)
4.8/5  (36)
(36)
Showing 41 - 60 of 81
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)