Exam 8: Security Strategies and Documentation
Exam 1: Windows Versions and Customer Service25 Questions
Exam 2: Installing Windows24 Questions
Exam 3: Setting up a Local Network31 Questions
Exam 4: Maintaining Windows24 Questions
Exam 5: Troubleshooting Windows After Startup24 Questions
Exam 6: Troubleshooting Windows Startup24 Questions
Exam 7: Securing and Sharing Windows Resources25 Questions
Exam 8: Security Strategies and Documentation71 Questions
Exam 9: Supporting Mobile Devices58 Questions
Exam 10: Macos, Linux, and Scripting24 Questions
Exam 11: Appendix: Asafety Procedures and Environmental Concerns8 Questions
Select questions type
While researching a network issue, Randy discovered a diagram that he can use to see the design of the network.
What type of documentation did Randy discover?
(Multiple Choice)
4.8/5  (24)
(24)
Roger's company is trying to increase the level of security for its network. Roger is researching ways to increase the security by making passwords more complex.
What can Roger change in Windows to require more complex passwords?
(Multiple Choice)
4.7/5  (38)
(38)
Jerry was recently contacted by a coworker who received an email that seemed suspicious. Jerry investigated her email account and noticed that she had been sending hundreds of emails every day for a week. He also noticed that this problem started after the coworker sent a reply email agreeing to participate in a contest to win a free car wash.
What happened to the coworker's email account?
(Multiple Choice)
4.8/5  (38)
(38)
Recently, Jessica has been receiving reports at the help desk that clients cannot log in to their computers and need to rest their passwords. After checking the log file, Jessica decided to ask one client who had recently changed his password, why he decided to change it. The client reported that someone from the help desk had called him and asked him for his password two days ago. He gave the caller the password, and now he can't log in to his system. Jessica has discovered that the client was a victim of social engineering.
What can the company do to prevent this from happening again?
(Multiple Choice)
4.8/5  (42)
(42)
Hector is trying to use Windows Defender to run an antivirus scan. Windows Defender refuses to run. When he opens the Action Center, Hector realizes that Windows Defender has been disabled and another antivirus software is running. Hector does not recognize the other antivirus software.
What type attack has infected Hector's computer?
(Multiple Choice)
4.8/5  (34)
(34)
Dylan is working on a system that has been having issues with files. Recently, Dylan has noticed that some of the filenames have strange characters, and the file sizes seem to be excessively large. File have been disappearing and Windows system files have been changed.
What might be the problem with the computer?
(Multiple Choice)
4.8/5  (38)
(38)
David would like to add extra security to his network device. He is afraid that someone might try and connect an unauthorized device to the network via an open network drop.
What type of security can David deploy to prevent this type of security issue from occurring?
(Multiple Choice)
4.9/5  (35)
(35)
Allison's computer is displaying a strange error message saying that Allison, who is an administrator, does not have access to a folder in the Documents library of her user account. Allison tried to take ownership of the folder but was still denied access. She tried running an antivirus scan on the folder, and again access to the folder was denied.
What can Allison do to fix this security issue?
(Multiple Choice)
4.7/5  (38)
(38)
Gwen has discovered a program that has copied itself throughout the network. The program does not appear to have a host program and is overloading the network as it replicates. It has even installed a web server on the network and is allowing other computers to connect.
What type of malware has Gwen discovered?
(Multiple Choice)
4.8/5  (37)
(37)
Zach believes someone is trying to log in to a computer system in order to gain access to the company's network. He wants to use Windows to determine if that is the case.
Where can Zach go to check the security logs?
(Multiple Choice)
4.9/5  (38)
(38)
Holly is trying to use Windows Defender to run an antivirus scan. Windows Defender refuses to run. She notices a problem when she tries to update Windows Defender and it fails. When Holly opens the Action Center she sees this screen.
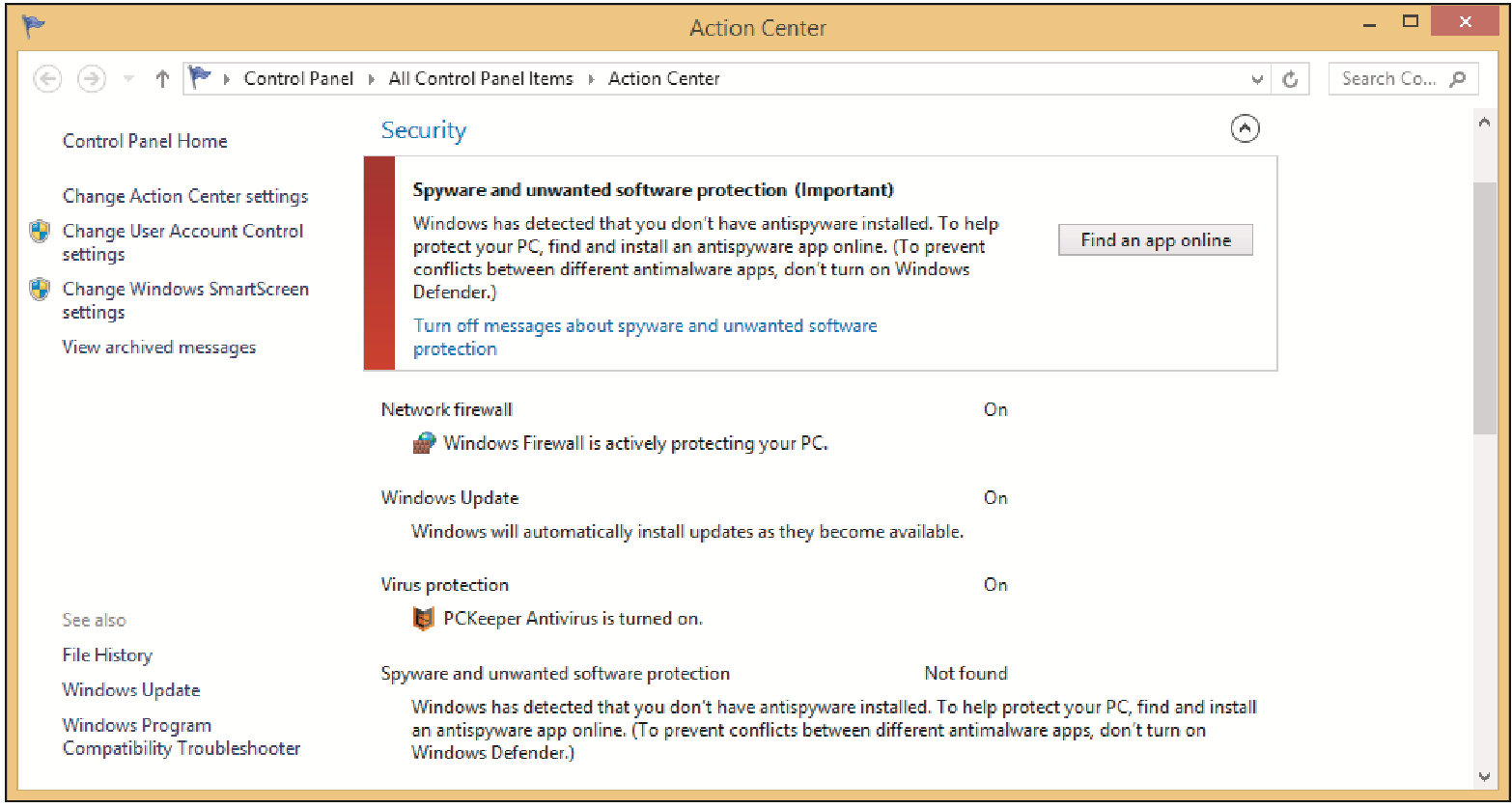 What has happened to Holly's computer?
What has happened to Holly's computer?
(Multiple Choice)
4.9/5  (47)
(47)
Showing 61 - 71 of 71
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)