Exam 8: Security Strategies and Documentation
Exam 1: Windows Versions and Customer Service25 Questions
Exam 2: Installing Windows24 Questions
Exam 3: Setting up a Local Network31 Questions
Exam 4: Maintaining Windows24 Questions
Exam 5: Troubleshooting Windows After Startup24 Questions
Exam 6: Troubleshooting Windows Startup24 Questions
Exam 7: Securing and Sharing Windows Resources25 Questions
Exam 8: Security Strategies and Documentation71 Questions
Exam 9: Supporting Mobile Devices58 Questions
Exam 10: Macos, Linux, and Scripting24 Questions
Exam 11: Appendix: Asafety Procedures and Environmental Concerns8 Questions
Select questions type
Tim has removed a virus from a customer's computer. The virus was a Trojan horse that the customer downloaded while trying to purchase software on the Internet.
What final step should Tim perform?
(Multiple Choice)
4.9/5  (38)
(38)
Samantha is having an issue with Windows crashing and believes that malicious software is causing it to crash. Samantha also has received application errors that have cause the applications to close.
Which event log in the Event Viewer can Samantha inspect to see if malicious software is causing the Windows system to crash and the application errors, system errors, and other types of errors?
(Multiple Choice)
4.9/5  (29)
(29)
James travels for business and is always worried that his laptop will be taken from his room.
Which type of device will ensure that James's laptop will not be stolen while he travels?
(Multiple Choice)
4.7/5  (35)
(35)
The company that you work for has recently had a security breech. During the recover and assessment, it was discovered that the malicious user used the company VPN to gain access to the network. Now your company would like to find a way to verify the identity of a user who requests access to the company through a VPN.
What can you recommend to the company?
(Multiple Choice)
4.8/5  (34)
(34)
Danny received this email message today.
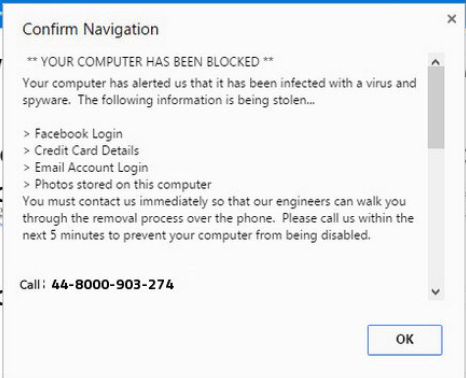 What happened to Danny's computer?
What happened to Danny's computer?
(Multiple Choice)
5.0/5  (32)
(32)
Which authentication service options work with Active Directory and other types of directory servers to authenticate and authorize users and can be used together on the same network? (Select TWO.)
(Multiple Choice)
4.9/5  (38)
(38)
Your company has decided to replace several hundred hard drives. It would like to donate the old hard drives to a local school system that will use them to increase storage on systems for students. However, the company also wants to make sure the hard drives are completely wiped before donating them.
Which disposal method will not allow the company to recycle the device? (Select all that apply.)
(Multiple Choice)
4.9/5  (38)
(38)
Alexandria works for a non-for-profit company that asks for donations to help the homeless people in her community. Recently the database that holds all the contact information about the donners was hacked, and all the data was copied.
What type of data was taken?
(Multiple Choice)
4.9/5  (36)
(36)
Derek's supervisor is concerned that the company's security system does not comply with the new standards the company has decided to employ. She has asked Derek to determine how members of the company are authenticated on the network.
What does the computer or server use to verify the access to a specific resource on the network?
(Multiple Choice)
4.9/5  (35)
(35)
Tracy works for an insurance company that recently received so much spam that the email server became overwhelmed and shut down. Tracy's supervisor has asked her to make sure this does not happen again.
What is the first thing Tracy should do to prevent this problem from happening again?
(Multiple Choice)
4.9/5  (32)
(32)
Jennifer is trying to install an anti-malware program on a computer that she believes might be infected. During the installation, she receives an error message saying the software cannot be installed. The error reports that she does not have the privilege to install software. Jennifer is using the administrator account, so she knows she should be able to install the program.
What can Jennifer try next to install anti-malware software?
(Multiple Choice)
4.8/5  (41)
(41)
Ken has discovered that a vice president of his company has been using his computer to send data about a new product to a competitor. Ken has identified an email from the vice president and has tracked the information to the person at the other company. Ken has archived the evidence that proves the data has been sent.
What should Ken do next?
(Multiple Choice)
4.8/5  (37)
(37)
James has a USB flash drive that he has used at work. The drive needs to be thrown away, but James wants to make sure that the data is no longer on the drive before he throws it away.
What can James use to wipe the data clean? (Select TWO.)
(Multiple Choice)
4.7/5  (34)
(34)
Karen received a call from a client whose computer will not boot. The client explained that he had just received an error message about a virus on the computer. When Karen arrived, she tried to boot the computer in Safe Mode, but that did not work. Karen decided to install the hard drive on a working computer.
What should Karen do after she installs the hard drive on a second computer?
(Multiple Choice)
4.9/5  (46)
(46)
Your company wants to secure the new data center physically. The company has hired a security guard but wants to find a way so that only one person at a time can enter in the data center. As people enter, they will have to show the security guard identification that authorizes them to enter the data center.
What is your company's new security called?
(Multiple Choice)
4.8/5  (32)
(32)
Jackson has completed remediation of a virus-infected system. He eliminated all the startup program issues and uninstalled several browser add-ons. Jackson has scheduled scans to be performed daily and has run updates on Windows and the anti-malware program. He has enabled System Restore and created a new restore point.
What should Jackson do to complete the malware removal process?
(Multiple Choice)
4.8/5  (34)
(34)
Danielle, a help desk technician, receives a call from a client. In a panic, he explains that he was using the Internet to research a new product when his computer emitted an alarm accompanied by a warning that a site had blocked his computer and that information was being stolen from the computer. The message included a phone number and a note to call the number within five minutes so that engineers could walk him through the removal process.
What has happened to the customer computer?
(Multiple Choice)
4.8/5  (38)
(38)
Nick is working on a computer at a customer's house. The customer is concerned that her computer has a problem because recently the Internet home page changed, and when she tried to search the Internet, a strange search engine appeared.
What has happened to the customer's computer?
(Multiple Choice)
4.9/5  (43)
(43)
Shane is working on a new project for the sales department. The company wants a way to allow the sales force to print orders at the company headquarters. Shane has proposed that their computers be able to connect to the system using a VPN.
Who does Shane need to get permission from before he installs the VPN?
(Multiple Choice)
4.8/5  (36)
(36)
The web server at Terry's company recently was attacked by multiple computers. The attack overwhelmed the company's web servers and caused the web servers to crash.
What type of attack occurred?
(Multiple Choice)
4.8/5  (35)
(35)
Showing 41 - 60 of 71
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)