Exam 8: Security Strategies and Documentation
Exam 1: Windows Versions and Customer Service25 Questions
Exam 2: Installing Windows24 Questions
Exam 3: Setting up a Local Network31 Questions
Exam 4: Maintaining Windows24 Questions
Exam 5: Troubleshooting Windows After Startup24 Questions
Exam 6: Troubleshooting Windows Startup24 Questions
Exam 7: Securing and Sharing Windows Resources25 Questions
Exam 8: Security Strategies and Documentation71 Questions
Exam 9: Supporting Mobile Devices58 Questions
Exam 10: Macos, Linux, and Scripting24 Questions
Exam 11: Appendix: Asafety Procedures and Environmental Concerns8 Questions
Select questions type
Lin received 200 new laptops to be issued to company employees. Lin was asked to set them up and distribute them to everyone on a list provided by his supervisor. Lin has completed installing all the software on each computer and is ready to distribute them, but he needs to keep track of who received each laptop.
How can Lin keep track of all the laptops?
Free
(Multiple Choice)
4.9/5  (23)
(23)
Correct Answer:
C
One of Kyle's clients called to complain that his computer was running really slow. Kyle went to the client's work area and started troubleshooting the problem. Kyle ran the Disk Defragmenter and Disk Clean-up utilities. He checked the processes running in Task Manger and noticed that the SVC host was running several processes. While Kyle was looking at Task Manager, the computer crashed. Kyle restarted the computer and noticed a long load time for Windows. He checked Task Manager and saw several processes that he did not recognize.
What might be the issue with Kyle's client's computer?
Free
(Multiple Choice)
4.9/5  (30)
(30)
Correct Answer:
C
If your Internet home page has changed and a strange-looking search engine appears when you try to search the Internet, what type of attack are you experiencing?
Free
(Multiple Choice)
4.8/5  (40)
(40)
Correct Answer:
D
Jeff owns a health care company that sells medical supplies. The company bills health insurance companies for their customers. They are required by the insurance companies to complete paperwork that includes personal and health information. What type of regulated data does Jeff's company need to secure?
(Multiple Choice)
4.7/5  (31)
(31)
An operating system is responsible for validating certificates used to secure communication. For Windows, Microsoft maintains a database of trusted root certificates issued by Certificate Authorities (CAs). A root certificate is the original certificate issued by the CA. When a Windows system opens a secure email or visits a secure website and encounters a new digital certificate, it requests Microsoft's trusted root certificate, which is downloaded to the computer. The download happens seamlessly without the user's knowledge unless there's a problem. If Windows cannot obtain the root certificate to validate the email or website, an error is displayed.
Where do you go in the Windows operating system to view and delete root certificates?
(Multiple Choice)
4.7/5  (35)
(35)
Sharon's company has written a new computer program, and she has been asked to find a way to prevent people from copying the software they purchase and giving it to others who have not purchased the software.
What can Sharon's company do to make sure a customer who purchases the program does not give it to someone else?
(Multiple Choice)
4.9/5  (39)
(39)
Jordan is talking with a client on the phone. Jordan's company recently completed updates on the client's system and something is not working properly. The client asks Jordan why the company is always doing updates. Jordan explain that updates help to secure computer systems.
What specific vulnerability do updates help prevent?
(Multiple Choice)
4.8/5  (39)
(39)
Recently, Frank's computer has slowed down dramatically. He has also noticed that the time on the computer is not accurate. Frank has run several antivirus scans, but has not found an issue. Today while surfing the web, he was redirected several times to a website that he did not request. Then a BSOD error occurred on his computer, and when he turned on his computer, the antivirus software was disabled.
What kind of malware could be causing the issues on Frank's computer?
(Multiple Choice)
4.8/5  (28)
(28)
Your company is using RADIUS for AAA services to connect wireless users to the Windows Active Directory domain. However, the company wants to upgrade to a Cisco-based wireless network and would like to upgrade the older RADIUS.
What will you recommend as an upgrade to RADIUS?
(Multiple Choice)
4.9/5  (34)
(34)
Your company's email server has been filling up employee's email boxes with advertisements for things they did not request. You have been asked to research how to stop these types of messages from getting to your coworker's email client software.
What will you recommend to your supervisor?
(Multiple Choice)
4.8/5  (37)
(37)
Lana has just taken a job as an IT professional in Europe and would like to get a head start on what to expect.
What regulated data would you recommend that she research?
(Multiple Choice)
4.7/5  (33)
(33)
The computer that you are working on is not able to complete a Windows update. The update process begins to download the file, but then you receive an error message saying that the Windows update was unable to download. You have checked your Internet connection, and it is working. You have tried the update on your other computer, and it worked.
What should you do first to fix the problem with the Windows update?
(Multiple Choice)
4.8/5  (43)
(43)
Christian has malware that is preventing him from installing anti-malware on his laptop.
What can Christian try if he does not have another computer available to run the anti-malware program?
(Multiple Choice)
4.9/5  (35)
(35)
Holly has been tasked to design the plan the IT department will use when making a change to systems. The plan will be used anytime the company needs to change a system and should include which people are to be contacted when changes are made and what the changes will do to other equipment.
While Holly writes the change document, what types of things will she need to include in the scope of change? (Select all that apply.)
(Multiple Choice)
4.8/5  (31)
(31)
Your company has decided that security is very important and wants to add a second security check that will identify its employees while they are logging in to their computers.
What type of security do you recommend?
(Multiple Choice)
4.9/5  (37)
(37)
Joe works for a company that has a traveling sales force. The company has asked Joe to research a way for the sales force to have real-time information on the availability of its salable products. The company has an intranet application that allows it to see up-to-the minute information. The company does not want to make this information public.
What should Joe recommend?
(Multiple Choice)
4.9/5  (31)
(31)
A customer called Derek to complain that her computer was running slow, so he went to the client work area and started troubleshooting the problem. Derek ran the Disk Defragmenter and Disk Clean-up utilities. He checked the processes running in Task Manger.
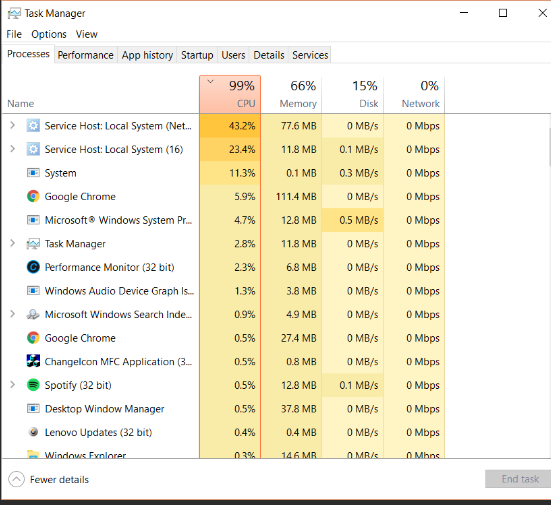 Derek found that the CPU was running several processes. While Derek was looking at Task Manager, the computer crashed. Derek restarted the computer and noticed a long load time for Windows. Derek checked Task Manager and saw several processes that he did not recognize.
What should Derek perform next on the client's computer?
Derek found that the CPU was running several processes. While Derek was looking at Task Manager, the computer crashed. Derek restarted the computer and noticed a long load time for Windows. Derek checked Task Manager and saw several processes that he did not recognize.
What should Derek perform next on the client's computer?
(Multiple Choice)
4.8/5  (35)
(35)
Jerry has received an email on his company's email system. The email is in regard to a new update the company plans to implement. The administrators are requesting that everyone send their username and password so that the administrators can compile a list and avoid having everyone change their passwords.
What type of attack is this?
(Multiple Choice)
5.0/5  (41)
(41)
Oscar has a client who has been receiving unsolicited emails from several companies. Oscar recommended that the client unsubscribe from the email lists, but that just increased the number of unsolicited emails she received.
What can Oscar do to stop the unsolicited emails on the email server?
(Multiple Choice)
4.8/5  (34)
(34)
If you receive this error when trying to go to a website, where can you go in Windows to verify the certificate settings for the website?
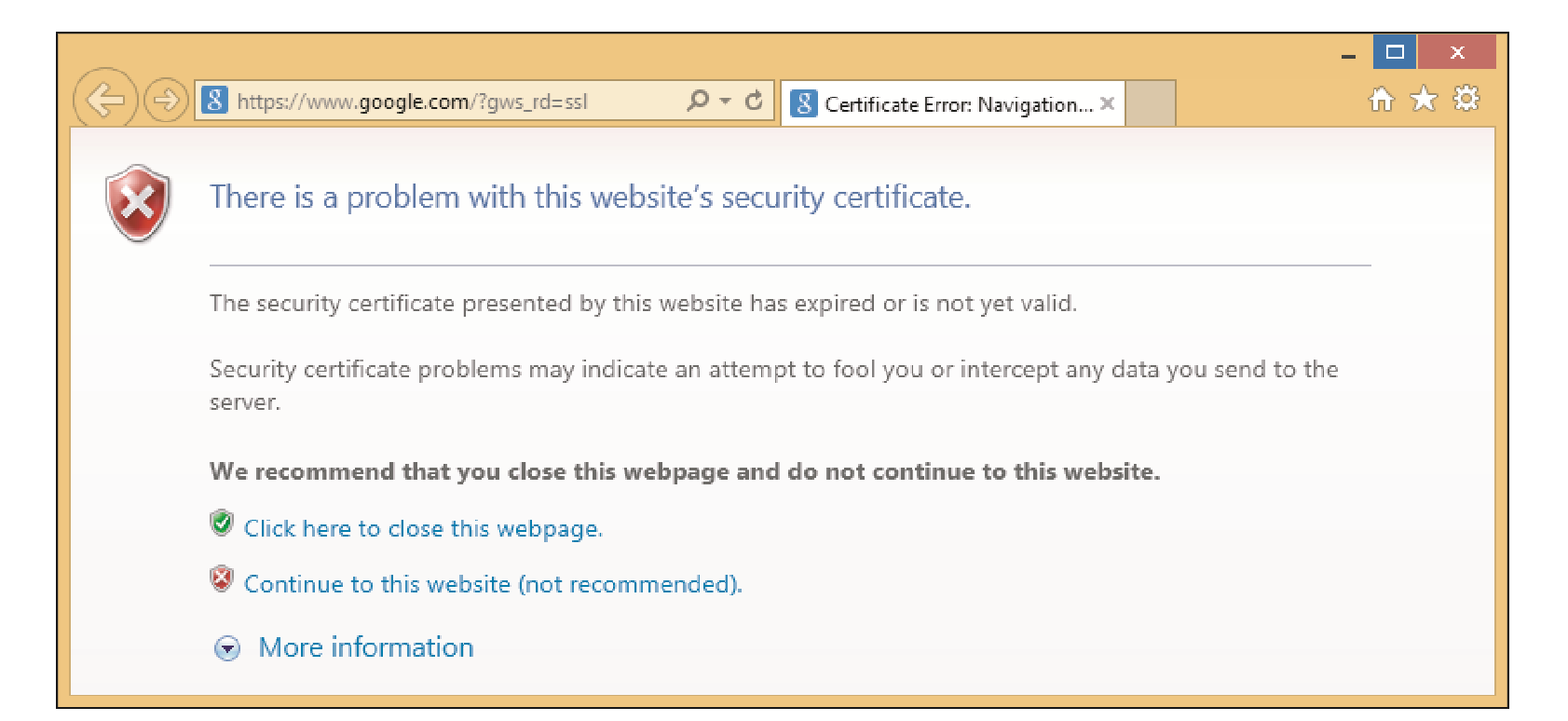
(Multiple Choice)
4.8/5  (31)
(31)
Showing 1 - 20 of 71
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)