Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses
Exam 1: Digital Literacy: Introducing a World of Technology200 Questions
Exam 2: The Internet: Accessing, Searching, Sharing, and Communicating200 Questions
Exam 3: Computers and Mobile Devices: Evaluating the Possibilities200 Questions
Exam 4: Programs and Apps: Using Software at Work, School, and Home200 Questions
Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses200 Questions
Exam 6: Internet Services, Devices, and Software140 Questions
Select questions type
One way to reduce electrical waste is for organizations to consolidate servers by user concatenation.
(True/False)
4.9/5  (36)
(36)
COPPA requires that schools and libraries use content filtering software in order to receive certain federal funds.
(True/False)
4.8/5  (28)
(28)
Which of the following refers to the right of individuals and companies to deny or restrict the collection and use of information about them?
(Multiple Choice)
4.9/5  (24)
(24)
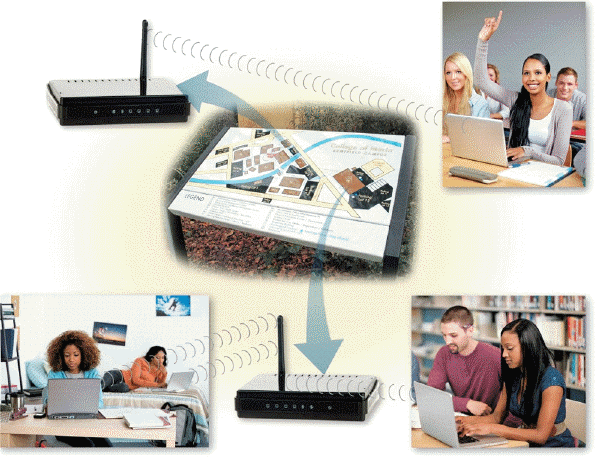 Explain three safeguards you can use to secure your wireless networks like the kind in the accompanying figure.
Explain three safeguards you can use to secure your wireless networks like the kind in the accompanying figure.
(Essay)
4.9/5  (35)
(35)
A(n) ____________________ object is any item that must be carried to gain access to a computer or computer facility.
(Short Answer)
4.8/5  (35)
(35)
Personal firewalls constantly monitor all transmissions to and from a computer and may inform a user of any attempted intrusion.
(True/False)
4.8/5  (32)
(32)
Critical Thinking Questions Case 5-1 One form of software theft is the theft of the software from software manufacturers, which is known as piracy. Because this has historically been rather easy to do, the practice has become very common. As a computer instructor you feel it is your responsibility to explain this practice to students through the use of some examples. Which of the following practice IS permissible under a single-user license agreement?
(Multiple Choice)
4.7/5  (33)
(33)
An IT code of conduct is a written guideline that helps determine whether a specific computer action is which of the following?
(Multiple Choice)
4.9/5  (37)
(37)
Information collected and stored about individuals should be limited to what is necessary to carry out the function of the business or government agency collecting the data.
(True/False)
4.8/5  (24)
(24)
Which of the following does your company use to track your time and attendance?
(Multiple Choice)
4.9/5  (31)
(31)
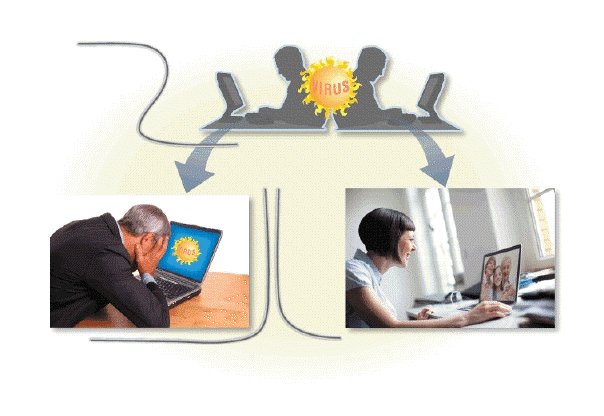 Computer viruses like the kind in the accompanying figure-along with worms, and Trojan horses-deliver their ____________________ on a computer or mobile device when a user opens an infected file or runs an infected program.
Computer viruses like the kind in the accompanying figure-along with worms, and Trojan horses-deliver their ____________________ on a computer or mobile device when a user opens an infected file or runs an infected program.
(Short Answer)
4.9/5  (43)
(43)
 Users can purchase a software program that selectively blocks cookies like the kind shown in the accompanying figure.
Users can purchase a software program that selectively blocks cookies like the kind shown in the accompanying figure.
(True/False)
4.9/5  (36)
(36)
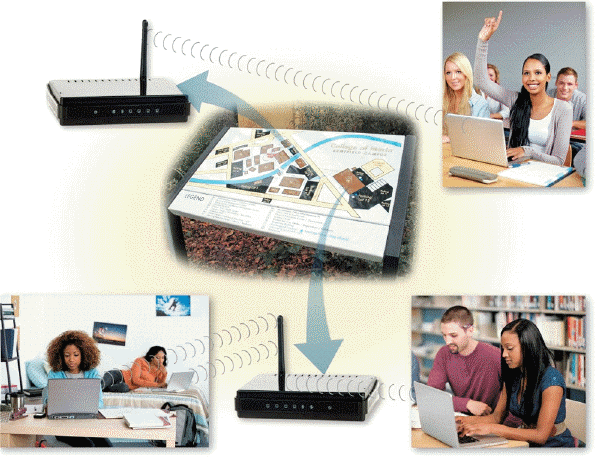 One study found that a certain percentage of wireless connections like the kind in the accompanying figure are unsecured, leaving them susceptible to hackers. What was that percentage?
One study found that a certain percentage of wireless connections like the kind in the accompanying figure are unsecured, leaving them susceptible to hackers. What was that percentage?
(Multiple Choice)
5.0/5  (31)
(31)
With which of the following do users choose which folders and files to include in a backup?
(Multiple Choice)
4.8/5  (33)
(33)
In the case of system failure or the discovery of corrupted files, what do users do to the backed-up files when they bring the files to their original location on a computer?
(Multiple Choice)
4.8/5  (45)
(45)
Which of the following terms is used to describe a file a computer creates that records successful and unsuccessful access attempts?
(Multiple Choice)
4.8/5  (41)
(41)
Many organizations and businesses have strict written policies governing the installation and use of software and enforce their rules by checking networked or online computers periodically to ensure that all software is licensed properly.
(True/False)
4.9/5  (27)
(27)
Which of the following refers to a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network?
(Multiple Choice)
4.9/5  (44)
(44)
Discuss the seven different categories into which perpetrators of cybercrime and other intrusions fall.
(Essay)
4.8/5  (27)
(27)
Showing 181 - 200 of 200
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)