Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses
Exam 1: Digital Literacy: Introducing a World of Technology200 Questions
Exam 2: The Internet: Accessing, Searching, Sharing, and Communicating200 Questions
Exam 3: Computers and Mobile Devices: Evaluating the Possibilities200 Questions
Exam 4: Programs and Apps: Using Software at Work, School, and Home200 Questions
Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses200 Questions
Exam 6: Internet Services, Devices, and Software140 Questions
Select questions type
Which of the following does your financial institution use to reduce fraud?
(Multiple Choice)
4.9/5  (36)
(36)
____________________ is the process of converting readable data into unreadable characters to prevent unauthorized access.
(Short Answer)
4.8/5  (32)
(32)
Which of the following statements is not true about backing up?
(Multiple Choice)
4.8/5  (26)
(26)
Which of the following has the same intent as a cracker, but does not have the technical skills and knowledge?
(Multiple Choice)
4.8/5  (37)
(37)
Which of the following is someone who demands payment in order to stop an attack on an organization's technology infrastructure?
(Multiple Choice)
4.8/5  (32)
(32)
Which of the following terms refers to someone who accesses a computer or network illegally with the intent of malicious action?
(Multiple Choice)
4.8/5  (40)
(40)
To remove spyware, users need to obtain a special program that can detect and delete it.
(True/False)
4.8/5  (40)
(40)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
A common infringement of copyright.
Responses:
digital certificate
iris recognition system
web filtering software
Correct Answer:
Premises:
Responses:
(Matching)
4.8/5  (39)
(39)
A perpetrator is using a botnet. Which of the following is the least likely use of his botnet?
(Multiple Choice)
4.8/5  (30)
(30)
Which of the following replaces each character in the plaintext with a different letter by shifting the alphabet a certain number of positions?
(Multiple Choice)
4.8/5  (40)
(40)
____________________ is the unauthorized and illegal duplication of copyrighted software.
(Short Answer)
4.9/5  (25)
(25)
Critical Thinking Questions Case 5-2 In your introductory course on computers, your professor has decided to dedicate a lecture to computer ethics. There is a lot of ambiguity in this topic, and she has presented a range of circumstances for you and your classmates to review.Which of the following is NOT a question of computer ethics?
(Multiple Choice)
4.9/5  (40)
(40)
Which of the following refers to unique and original works such as ideas, inventions, writings, art, processes, company and product names, and logos?
(Multiple Choice)
4.9/5  (36)
(36)
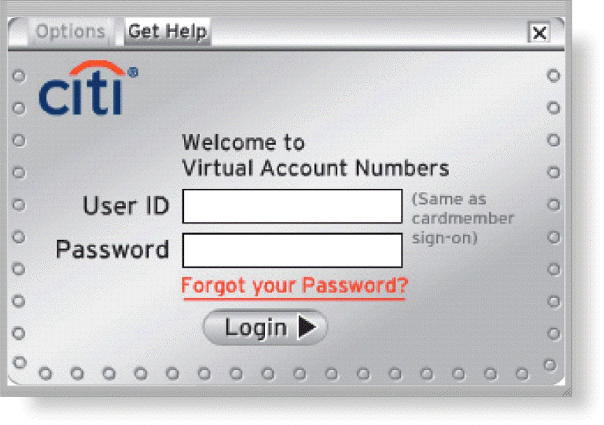 As shown in the accompanying figure, most operating systems require that users correctly enter a user name and password before they can access the data, information, and programs stored on a computer, mobile device, or network.
As shown in the accompanying figure, most operating systems require that users correctly enter a user name and password before they can access the data, information, and programs stored on a computer, mobile device, or network.
(True/False)
5.0/5  (30)
(30)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
A notice that guarantees a user or a website is legitimate.
Responses:
web filtering software
digital signature
DoS attack
Correct Answer:
Premises:
Responses:
(Matching)
4.8/5  (34)
(34)
Showing 21 - 40 of 200
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)