Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses
Exam 1: Digital Literacy: Introducing a World of Technology200 Questions
Exam 2: The Internet: Accessing, Searching, Sharing, and Communicating200 Questions
Exam 3: Computers and Mobile Devices: Evaluating the Possibilities200 Questions
Exam 4: Programs and Apps: Using Software at Work, School, and Home200 Questions
Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses200 Questions
Exam 6: Internet Services, Devices, and Software140 Questions
Select questions type
Which of the following provides the mobile user with a secure connection to the company network server?
(Multiple Choice)
4.7/5  (35)
(35)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Makes it illegal to circumvent antipiracy schemes in commercial software.
Responses:
password
zombie
digital security risk
Correct Answer:
Premises:
Responses:
(Matching)
4.9/5  (45)
(45)
Which of the following categories are the rights to which creators are entitled for their work?
(Multiple Choice)
4.9/5  (30)
(30)
Which of the following gives authors and artists the exclusive rights to duplicate, publish, and sell their materials?
(Multiple Choice)
4.9/5  (29)
(29)
A(n) ____________________ attack is an assault whose purpose is to disrupt computer access to an Internet service such as the web or email.
(Short Answer)
4.7/5  (35)
(35)
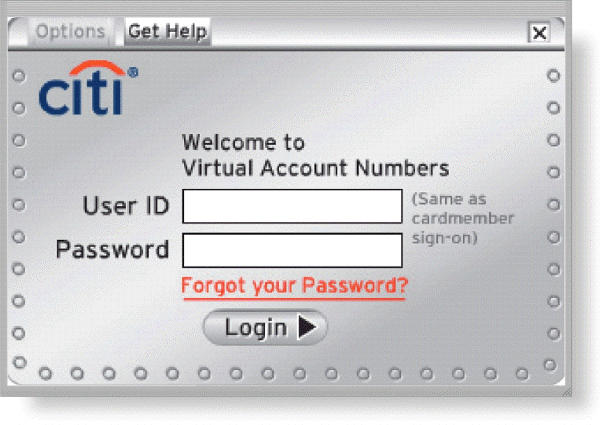 Many websites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
Many websites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
(Multiple Choice)
4.9/5  (34)
(34)
Which of the following kinds of certificate is a notice that guarantees a user or website is legitimate?
(Multiple Choice)
5.0/5  (26)
(26)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
An authorized person or company that issues and verifies digital certificates.
Responses:
script kiddie
digital security risk
AUP
Correct Answer:
Premises:
Responses:
(Matching)
4.9/5  (37)
(37)
Which of the following is the least likely motive for a DDoS?
(Multiple Choice)
4.7/5  (42)
(42)
Websites often collect data about you so that they can customize advertisements and send you personalized email messages.
(True/False)
4.7/5  (30)
(30)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Usually does not have advanced computer and technical skills.
Responses:
CA
botnet
Digital Millennium Copyright Act (DCMA)
Correct Answer:
Premises:
Responses:
(Matching)
4.9/5  (42)
(42)
To protect yourself from social engineering scams, shred all sensitive or confidential documents.
(True/False)
4.9/5  (41)
(41)
Into which of the following kinds of ports do external fingerprint readers plug?
(Multiple Choice)
4.8/5  (26)
(26)
Which of the following terms is used to describe a set of steps that can convert readable plaintext into unreadable ciphertext?
(Multiple Choice)
4.9/5  (25)
(25)
Which of the following is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed?
(Multiple Choice)
4.7/5  (35)
(35)
Perpetrators of back doors trick their victims into interacting with phony websites.
(True/False)
4.9/5  (34)
(34)
Showing 41 - 60 of 200
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)