Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses
Exam 1: Digital Literacy: Introducing a World of Technology200 Questions
Exam 2: The Internet: Accessing, Searching, Sharing, and Communicating200 Questions
Exam 3: Computers and Mobile Devices: Evaluating the Possibilities200 Questions
Exam 4: Programs and Apps: Using Software at Work, School, and Home200 Questions
Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses200 Questions
Exam 6: Internet Services, Devices, and Software140 Questions
Select questions type
Secure sites typically use digital certificates along with security protocols.
(True/False)
4.9/5  (25)
(25)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Outlines the activities for which a computer or network may and may not be used.
Responses:
firewall
clickjacking
AUP
Correct Answer:
Premises:
Responses:
(Matching)
4.9/5  (26)
(26)
The term ____________________ describes an attack whose goal ranges from disabling a government's computer network to crippling a country.
(Short Answer)
4.9/5  (26)
(26)
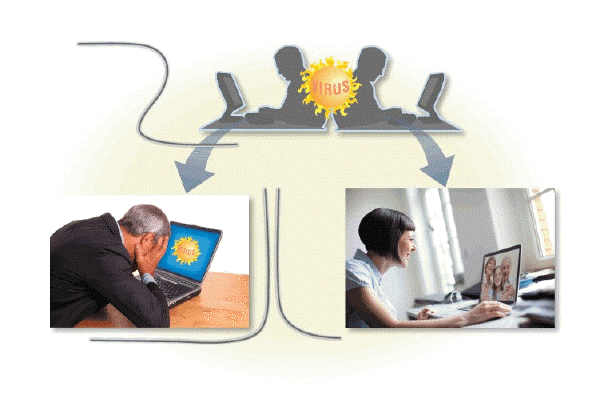 The Computer Abuse Amendments Act outlaws transmission of harmful computer code such as viruses like the kind shown in the accompanying figure.
The Computer Abuse Amendments Act outlaws transmission of harmful computer code such as viruses like the kind shown in the accompanying figure.
(True/False)
4.8/5  (36)
(36)
Which encryption algorithm inserts characters between existing characters?
(Multiple Choice)
4.8/5  (34)
(34)
Which of the following does your new smartphone use to unlock the device?
(Multiple Choice)
4.9/5  (31)
(31)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Any event or action that could cause a loss of or damage to computer or mobile device hardware.
Responses:
bot
Digital Millennium Copyright Act (DCMA)
clickjacking
Correct Answer:
Premises:
Responses:
(Matching)
4.9/5  (37)
(37)
When a waiter at a restaurant steals credit card numbers to make fraudulent purchases, this is called _____________.
(Multiple Choice)
4.8/5  (28)
(28)
Which of the following statements is not a safeguard against the failure of hardware?
(Multiple Choice)
4.9/5  (39)
(39)
Many Internet security programs include a firewall, antivirus program, and filtering capabilities combined.
(True/False)
4.9/5  (25)
(25)
What is the general term for programs that act without a user's knowledge and deliberately alter the computer's operations?
(Multiple Choice)
4.8/5  (31)
(31)
COPPA protects minors from inappropriate content when accessing the Internet in schools and libraries.
(True/False)
4.8/5  (33)
(33)
Which of the following statements is not true about Internet and network attacks?
(Multiple Choice)
4.8/5  (32)
(32)
Which of the following terms means in a location separate from the computer site?
(Multiple Choice)
4.8/5  (38)
(38)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Protects any tangible form of expression.
Responses:
firewall
ciphertext
piracy
Correct Answer:
Premises:
Responses:
(Matching)
4.9/5  (27)
(27)
A(n) ____________________ is a written plan that describes the steps an organization would take to restore its computer operations in the event of a disaster.
(Short Answer)
4.7/5  (37)
(37)
Personal computers, display devices, and printers should comply with guidelines of which of the following programs?
(Multiple Choice)
4.8/5  (43)
(43)
A(n) ____________________ is a program that hides in a computer or mobile device and allows someone from a remote location to take full control of the computer or devices.
(Short Answer)
4.8/5  (34)
(34)
Showing 101 - 120 of 200
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)