Exam 10: Database Management
Exam 1: Introduction to Computers191 Questions
Exam 2: The Internet and World Wide Web191 Questions
Exam 3: Application Software191 Questions
Exam 4: The Components of the System Unit191 Questions
Exam 5: Input181 Questions
Exam 6: Output191 Questions
Exam 7: Storage191 Questions
Exam 8: Operating Systems and Utility Programs191 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management191 Questions
Exam 11: Computer Security, Ethics, and Privacy191 Questions
Exam 12: Information System Development191 Questions
Exam 13: Programming Languages and Program Development191 Questions
Exam 14: Enterprise Computing191 Questions
Exam 15: Computer Careers and Certification191 Questions
Select questions type
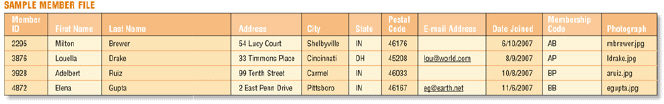 Figure 10-2 For the database pictured in Figure 10-2, the ____________________ defines the maximum number of characters a field can contain.
Figure 10-2 For the database pictured in Figure 10-2, the ____________________ defines the maximum number of characters a field can contain.
Free
(Short Answer)
4.8/5  (40)
(40)
Correct Answer:
field size
In a database, the data ____ specifies the kind of data a field can contain and how the field is used.
Free
(Multiple Choice)
4.8/5  (35)
(35)
Correct Answer:
C
A relational database typically processes and summarizes large numbers of records efficiently.
Free
(True/False)
4.8/5  (26)
(26)
Correct Answer:
False
A(n) ____________________ is a database that stores data in tables that consist of rows and columns.
(Short Answer)
4.8/5  (45)
(45)
Discuss at least three applications appropriate for an object-oriented database.
(Essay)
4.8/5  (29)
(29)
A(n) ____________________ allows users to design a report on the screen, retrieve data into the report design, and then display or print the report.
(Short Answer)
4.9/5  (34)
(34)
____ backup is a backup plan in which all data is backed up whenever a change is made.
(Multiple Choice)
4.9/5  (38)
(38)
Individual groups or departments often extract data from a data warehouse to create their data stations .
(True/False)
4.7/5  (36)
(36)
A DBMS that creates a log usually provides a(n) ____ utility that uses the logs and/or backups to restore a database when it becomes damaged or destroyed.
(Multiple Choice)
4.8/5  (42)
(42)
____ is a process designed to ensure the data within the relations (tables) contains the least amount of duplication.
(Multiple Choice)
4.9/5  (31)
(31)
A program determines the ____ by applying a formula to the numbers in the primary key value.
(Multiple Choice)
4.7/5  (33)
(33)
A(n) ____ is a program with which users interact that generally has a more user-friendly interface than a DBMS.
(Multiple Choice)
4.9/5  (29)
(29)
Validity checks, sometimes called ____________________, reduce data entry errors.
(Short Answer)
4.8/5  (30)
(30)
____________________ is a collection of unprocessed items, which can include text, numbers, images, audio, and video.
(Short Answer)
4.8/5  (35)
(35)
In a rollforward , the DBMS uses the log to undo any changes made to a database during a certain period, such as an hour.
(True/False)
4.9/5  (31)
(31)
For a computer to produce correct information, the data that is input into a database must have integrity.
(True/False)
4.9/5  (38)
(38)
To access data in a ____, users fill in a form on a Web page.
(Multiple Choice)
4.9/5  (40)
(40)
Showing 1 - 20 of 191
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)