Exam 6: Firewalls and Border Security
Exam 1: Operating Systems Security: Keeping Computers and Networks Secure86 Questions
Exam 2: Viruses, Worms, and Malicious Software86 Questions
Exam 3: Security Through Authentication and Encryption86 Questions
Exam 4: Account-Based Security86 Questions
Exam 6: Firewalls and Border Security86 Questions
Exam 7: Physical and Network Topology Security86 Questions
Exam 8: Wireless Security86 Questions
Exam 9: Web, Remote Access, and VPN Security86 Questions
Exam 10: E-Mail Security86 Questions
Exam 11: Security Through Disaster Recovery86 Questions
Exam 12: Security Through Monitoring and Auditing86 Questions
Select questions type
How many station addresses are available in a Class B network?
(Multiple Choice)
4.7/5  (40)
(40)
Which of the following protocols both sequences and acknowledges frames?
(Multiple Choice)
4.9/5  (35)
(35)
If you required 1000 IP host identities for your network, which of the following CIDR addresses would be valid if you want to make the best use of IP addressing?
(Multiple Choice)
4.8/5  (35)
(35)
Routers can isolate portions of a network to prevent areas of heavy traffic from reaching the broader network system.
(True/False)
4.7/5  (40)
(40)
Is one function of a proxy to screen application requests that go across a firewall placed between an internal network and an external or public network?
(True/False)
4.8/5  (37)
(37)
Does UDP provide the same level of reliability and error checking as TCP?
(True/False)
4.7/5  (44)
(44)
Which of the following applications use UDP for network communications?
(Multiple Choice)
4.7/5  (34)
(34)
In TCP communications, the number of data bytes transmitted in a frame is called the ____________________ because the number can be increased or decreased from one moment to the next by mutual agreement of the two communicating stations.
(Short Answer)
5.0/5  (32)
(32)
Routers that use a single protocol (such as TCP/IP) maintain multiple address databases.
(True/False)
4.8/5  (30)
(30)
Which field in an IP packet contains the network address and the address of the receiving device?
(Multiple Choice)
4.9/5  (37)
(37)
When using Class B addressing, which portion of the IP address 140.26.23.48 is the network address?
(Multiple Choice)
5.0/5  (32)
(32)
Are network classes A through C intended for unicast addressing methods?
(True/False)
4.9/5  (29)
(29)
Does dynamic NAT translate a range of addresses on the internal network to a range of specific decoy addresses?
(True/False)
4.9/5  (46)
(46)
IPv6 has a(n) _____ address capability and a 40-byte header.
(Multiple Choice)
4.9/5  (24)
(24)
TCP/IP consists of nearly 200 nonproprietary protocols that interconnect computer systems efficiently and reliably.
(True/False)
4.8/5  (35)
(35)
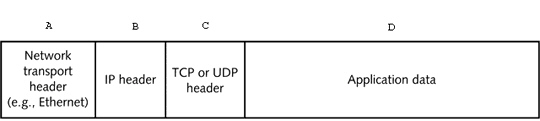 In the figure above, which letter indicates the portion of the TCP/IP packet that is the TCP segment?
In the figure above, which letter indicates the portion of the TCP/IP packet that is the TCP segment?
(Multiple Choice)
4.9/5  (35)
(35)
A route map is used to determine the best route through a network.
(True/False)
4.7/5  (35)
(35)
Network redundancy translation is used when there is a limited number of decoy addresses available, or when there are more computers on the internal network than decoy addresses.
(True/False)
4.8/5  (39)
(39)
Showing 61 - 80 of 86
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)