Exam 5: Automation and DevOps, Associate
Exam 1: Junos, Associate (JNCIA-Junos)193 Questions
Exam 2: Data Center Design, Specialist (JNCDS-DC)74 Questions
Exam 3: Security Design, Specialist (JNCDS-SEC)69 Questions
Exam 4: Cloud, Associate33 Questions
Exam 5: Automation and DevOps, Associate79 Questions
Exam 6: Security, Associate (JNCIA-SEC)93 Questions
Exam 7: Mist AI, Associate (JNCIA-MistAI)131 Questions
Exam 8: Security, Specialist38 Questions
Exam 9: Enterprise Routing and Switching, Specialist39 Questions
Exam 10: Service Provider Routing and Switching, Specialist78 Questions
Exam 11: JCloud, Specialist (JNCIS-Cloud)46 Questions
Exam 12: Mist AI, Specialist93 Questions
Exam 13: Security, Professional57 Questions
Exam 14: Enterprise Routing and Switching, Professional (JNCIP-ENT)39 Questions
Exam 15: Service Provider Routing and Switching, Professional (JNCIP-SP)30 Questions
Exam 16: New Data Center, Professional39 Questions
Select questions type
Which UTM feature uses MIME pattern filters to identify traffic in HTTP and e-mail protocols?
(Multiple Choice)
4.8/5  (36)
(36)
Which statement describes stateless firewalls on SRX Series devices?
(Multiple Choice)
4.8/5  (25)
(25)
Which solution should you use if you want to detect known attacks using signature-based methods?
(Multiple Choice)
4.9/5  (29)
(29)
Click the Exhibit button. 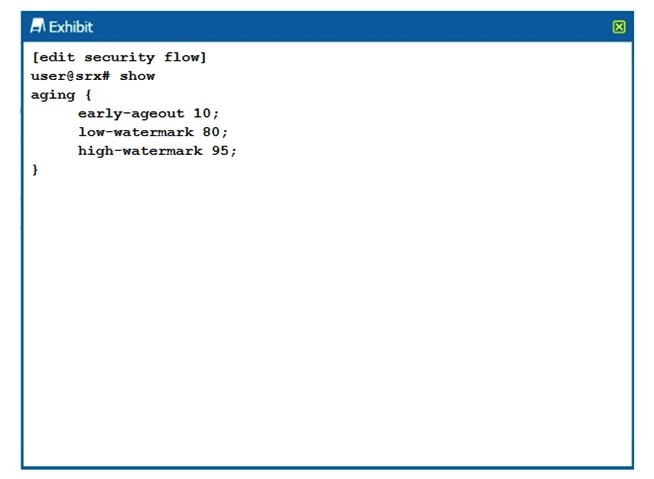 Which two statements are true about the configuration shown in the exhibit? (Choose two.)
Which two statements are true about the configuration shown in the exhibit? (Choose two.)
(Multiple Choice)
4.8/5  (32)
(32)
Which type of security policy protects restricted services from running on non-standard ports?
(Multiple Choice)
4.9/5  (35)
(35)
What is the default session timeout value for ICMP and UDP traffic?
(Multiple Choice)
4.7/5  (34)
(34)
You want to use Sky ATP to protect your network; however, company policy does not allow you to send any files to the cloud. Which Sky ATP feature should you use in this situation?
(Multiple Choice)
4.7/5  (43)
(43)
What is the default timeout period for a TCP session in the session table of a Junos security device?
(Multiple Choice)
4.9/5  (42)
(42)
You have deployed JSA and you need to view events and network activity that match rule criteria. You must view this data using a single interface. Which JSA feature should you use in this scenario?
(Multiple Choice)
4.7/5  (36)
(36)
Which security log message format reduces the consumption of CPU and storage?
(Multiple Choice)
4.8/5  (39)
(39)
Your company has been assigned one public IP address. You want to enable Internet traffic to reach multiple servers in your DMZ that are configured with private IP addresses. In this scenario, which type of NAT would be used to accomplish this task?
(Multiple Choice)
4.8/5  (34)
(34)
Click the Exhibit button. 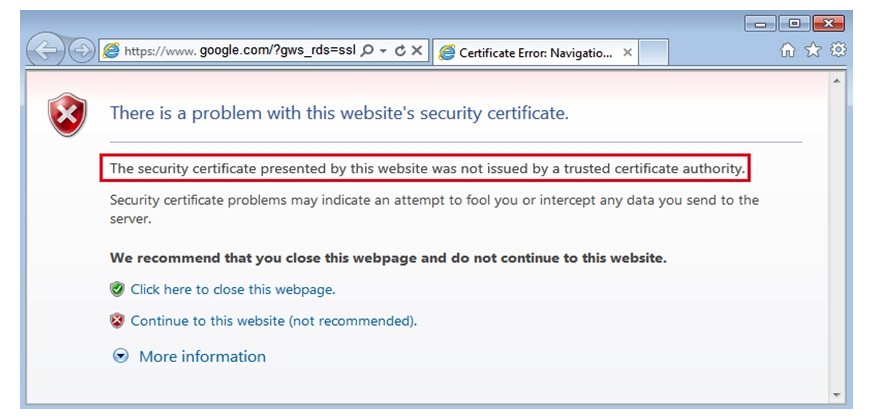 You have implemented SSL proxy client protection. After implementing this feature, your users are complaining about the warning message shown in the exhibit. Which action must you perform to eliminate the warning message?
You have implemented SSL proxy client protection. After implementing this feature, your users are complaining about the warning message shown in the exhibit. Which action must you perform to eliminate the warning message?
(Multiple Choice)
4.8/5  (22)
(22)
Click the Exhibit button. 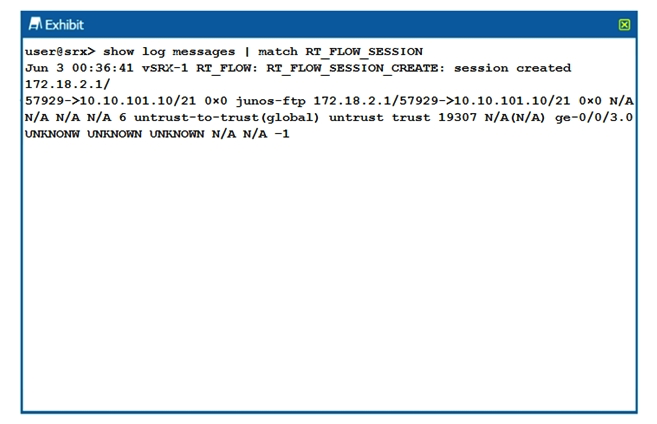 The output shown in the exhibit is displayed in which format?
The output shown in the exhibit is displayed in which format?
(Multiple Choice)
4.9/5  (29)
(29)
What is the maximum number of supported interfaces on a vSRX hosted in a VMware environment?
(Multiple Choice)
4.8/5  (31)
(31)
Click the Exhibit button. 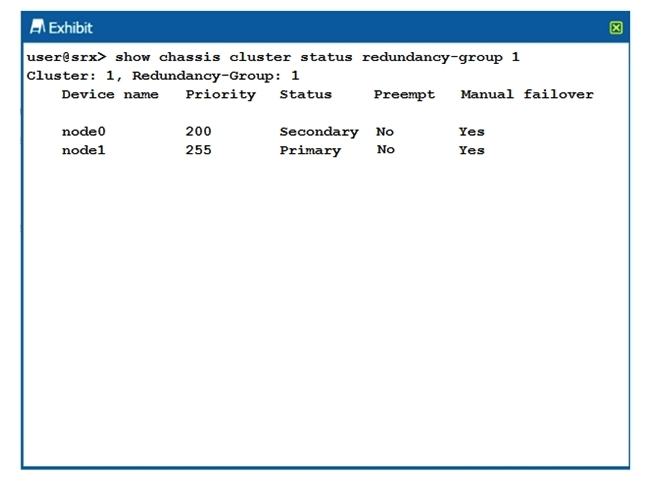 Which two statements describe the output shown in the exhibit? (Choose two.)
Which two statements describe the output shown in the exhibit? (Choose two.)
(Multiple Choice)
4.9/5  (26)
(26)
Which two statements are true about security policies in the factory-default configuration of an SRX340? (Choose two.)
(Multiple Choice)
4.8/5  (32)
(32)
Which two functions are performed by Juniper Identity Management Service (JIMS)? (Choose two.)
(Multiple Choice)
4.9/5  (44)
(44)
What is the purpose of the Shadow Policies workspace in J-Web?
(Multiple Choice)
4.8/5  (30)
(30)
Showing 21 - 40 of 79
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)