Exam 5: Automation and DevOps, Associate
Exam 1: Junos, Associate (JNCIA-Junos)193 Questions
Exam 2: Data Center Design, Specialist (JNCDS-DC)74 Questions
Exam 3: Security Design, Specialist (JNCDS-SEC)69 Questions
Exam 4: Cloud, Associate33 Questions
Exam 5: Automation and DevOps, Associate79 Questions
Exam 6: Security, Associate (JNCIA-SEC)93 Questions
Exam 7: Mist AI, Associate (JNCIA-MistAI)131 Questions
Exam 8: Security, Specialist38 Questions
Exam 9: Enterprise Routing and Switching, Specialist39 Questions
Exam 10: Service Provider Routing and Switching, Specialist78 Questions
Exam 11: JCloud, Specialist (JNCIS-Cloud)46 Questions
Exam 12: Mist AI, Specialist93 Questions
Exam 13: Security, Professional57 Questions
Exam 14: Enterprise Routing and Switching, Professional (JNCIP-ENT)39 Questions
Exam 15: Service Provider Routing and Switching, Professional (JNCIP-SP)30 Questions
Exam 16: New Data Center, Professional39 Questions
Select questions type
Click the Exhibit button. 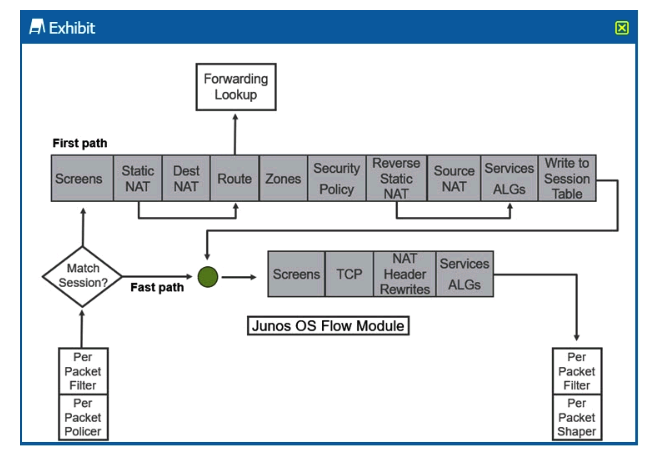 Referring to the SRX Series flow module diagram shown in the exhibit, where is IDP/IPS processed?
Referring to the SRX Series flow module diagram shown in the exhibit, where is IDP/IPS processed?
(Multiple Choice)
4.8/5  (38)
(38)
You want to deploy vSRX in Amazon Web Services (AWS) virtual private clouds (VPCs). Which two statements are true in this scenario? (Choose two.)
(Multiple Choice)
4.8/5  (24)
(24)
Which method do VPNs use to prevent outside parties from viewing packets in clear text?
(Multiple Choice)
4.7/5  (36)
(36)
You have configured a Web filtering UTM policy. Which action must be performed before the Web filtering UTM policy takes effect?
(Multiple Choice)
4.7/5  (24)
(24)
When referencing a SSL proxy profile in a security policy, which two statements are correct? (Choose two.)
(Multiple Choice)
4.9/5  (30)
(30)
You must ensure that all encrypted traffic passing through your SRX device uses strong protocols and ciphers. Which feature should you implement to satisfy this requirement?
(Multiple Choice)
4.8/5  (30)
(30)
Which two statements describe application-layer gateways (ALGs)? (Choose two.)
(Multiple Choice)
4.9/5  (44)
(44)
By default, revenue interfaces are placed into which system-defined security zone on an SRX Series device?
(Multiple Choice)
4.9/5  (35)
(35)
You want to automatically generate the encryption and authentication keys during IPsec VPN tunnel establishment. What would be used to accomplish this task?
(Multiple Choice)
4.9/5  (36)
(36)
You want to collect events and flows from third-party vendors. Which solution should you deploy to accomplish this task?
(Multiple Choice)
4.8/5  (30)
(30)
Click the Exhibit button. 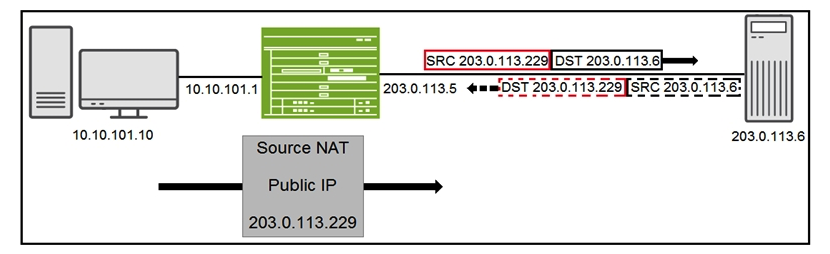 You have configured source NAT using an address pool as shown in the exhibit. Traffic is reaching the 203.0.113.6 server but return traffic is not being received by the SRX Series device. Which feature must be configured to allow return traffic to be accepted by the SRX Series device?
You have configured source NAT using an address pool as shown in the exhibit. Traffic is reaching the 203.0.113.6 server but return traffic is not being received by the SRX Series device. Which feature must be configured to allow return traffic to be accepted by the SRX Series device?
(Multiple Choice)
4.9/5  (36)
(36)
You are asked to enable AppTrack to monitor application traffic from hosts in the User zone destined to hosts in the Internet zone. In this scenario, which statement is true?
(Multiple Choice)
4.9/5  (36)
(36)
You are designing a new security policy on an SRX Series device. You must block an application silently and log all occurrences of the application access attempts. In this scenario, which two actions must be enabled in the security policy? (Choose two.)
(Multiple Choice)
4.7/5  (29)
(29)
You want to deploy, manage, and configure multiple SRX Series devices without an on-premises software solution. Which solution would satisfy this requirement?
(Multiple Choice)
4.8/5  (42)
(42)
You must fine tune an IPS security policy to eliminate false positives. You want to create exemptions to the normal traffic examination for specific traffic. Which two parameters are required to accomplish this task? (Choose two.)
(Multiple Choice)
4.8/5  (35)
(35)
Which two actions are performed on an incoming packet matching an existing session? (Choose two.)
(Multiple Choice)
4.9/5  (34)
(34)
Showing 61 - 79 of 79
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)