Exam 9: Cybersecurity: Network and Host Protection
Exam 1: Networking: Fundamental Concepts33 Questions
Exam 2: Cybersecurity: Fundamentals13 Questions
Exam 3: Essential Layers of Computer Networking40 Questions
Exam 4: Ip Address Planning and Management38 Questions
Exam 5: Intermediary Devices31 Questions
Exam 6: Wi-Fi and Cellular Network43 Questions
Exam 7: Ethernet Lan24 Questions
Exam 8: Cybersecurity: Threats23 Questions
Exam 9: Cybersecurity: Network and Host Protection19 Questions
Exam 10: Cybersecurity: Data Protection24 Questions
Exam 11: Fundamentals of Packet Routing29 Questions
Exam 12: Wide Area Network33 Questions
Exam 13: Physical Layer Data Transmissions19 Questions
Exam 14: Enterprise Network: LAN Topology, Routing, and Connectivity30 Questions
Select questions type
I am trying to reach a web server, www.chicago.edu. The response message from the DNS server tells my computer the _____.
Free
(Multiple Choice)
4.8/5  (41)
(41)
Correct Answer:
B
The ____ packet filtering screens individual packets in isolation.
Free
(Multiple Choice)
4.8/5  (32)
(32)
Correct Answer:
C
Which of the following filtering rules is considered a 'complete' rule on a firewall?
Free
(Multiple Choice)
4.9/5  (37)
(37)
Correct Answer:
E
Which of the following technologies is NOT used for authentication?
(Multiple Choice)
4.7/5  (30)
(30)
The analyst of cyber threat intelligence more likely uses ________ heavily for day-to-day tasks.
(Multiple Choice)
4.9/5  (40)
(40)
Choose a CORRECT pairing between a security layer and its corresponding technical solution (remember to choose the most accurate one).
(Multiple Choice)
4.9/5  (31)
(31)
Which filtering rule of a firewall is more likely a 'stateful' rule than the others?
(Multiple Choice)
4.7/5  (31)
(31)
The statement, "127.0.0.1 localhost", should be in included in the _________ file of a computer.
(Multiple Choice)
4.8/5  (39)
(39)
The following represent technical measures relevant to the host security layer EXCEPT:
(Multiple Choice)
4.9/5  (45)
(45)
The 'root' and 'authority' server concepts are relevant to the _________ protocol.
(Multiple Choice)
4.9/5  (29)
(29)
The authoritative server concept applies to the _________ protocol.
(Multiple Choice)
4.8/5  (28)
(28)
Which protocol information may be LEAST used by the firewall to filter packets?
(Multiple Choice)
4.8/5  (42)
(42)
Which CORRECTLY pairs a security layer and a technology solution?
(Multiple Choice)
4.9/5  (36)
(36)
Which command is issued to obtain the IP address of a domain name, "www.sdsu.edu", as in the figure?

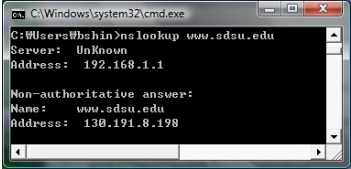
(Multiple Choice)
4.8/5  (35)
(35)
"If destination IP = 161.154.23.59 and TCP port = 25, then pass the packet" is a form of the _____ filtering rule.
(Multiple Choice)
4.8/5  (33)
(33)
The _____ is better positioned to conduct 'deep packet inspection'.
(Multiple Choice)
4.7/5  (36)
(36)
Which of the following filtering rules of the firewall is considered a stateful rule ?
(Multiple Choice)
4.7/5  (33)
(33)
The intrusion detection and intrusion prevention systems are designed to enable/provide ______.
(Multiple Choice)
4.8/5  (43)
(43)
The uniform resource locator (URL) field includes information on:
(Multiple Choice)
4.7/5  (32)
(32)
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)