Exam 16: Cybersecurity
Exam 1: Accounting As Information98 Questions
Exam 2: Risks and Risk Assessments100 Questions
Exam 3: Risk Management and Internal Controls100 Questions
Exam 4: Software and Systems106 Questions
Exam 5: Data Storage and Analysis98 Questions
Exam 6: Systems and Database Design98 Questions
Exam 7: Emerging and Disruptive Technologies100 Questions
Exam 8: Documenting Systems and Processes100 Questions
Exam 9: Human Resources and Payroll Processes100 Questions
Exam 10: Purchasing and Payments Process100 Questions
Exam 11: Conversion Processes100 Questions
Exam 12: Marketing, Sales, and Collection Processes100 Questions
Exam 13: Financial Reporting Processes103 Questions
Exam 14: Information Systems and Controls100 Questions
Exam 15: Fraud100 Questions
Exam 16: Cybersecurity99 Questions
Exam 17: Data Analytics99 Questions
Exam 18: Data Visualization100 Questions
Exam 19: Audit Assurance86 Questions
Select questions type
Attackers us these three types of attacks to plan, enter, and damage a victim's network:
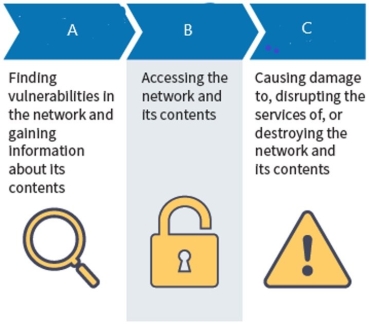 What type of attack is C?
What type of attack is C?
(Multiple Choice)
4.7/5  (26)
(26)
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is divided into 18 control families. One of the control families is Physical and Environmental Protection. What ID does Physical and Environmental Protection family use?
(Multiple Choice)
4.8/5  (41)
(41)
________ are the biggest weakness in a company's internal control environment.
(Multiple Choice)
4.8/5  (41)
(41)
Attackers us these three types of attacks to plan, enter, and damage a victim's network:
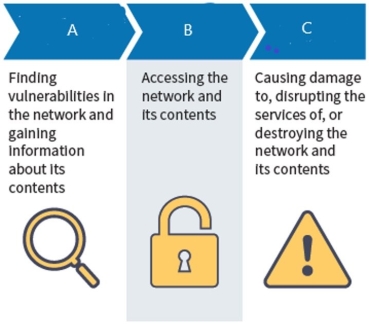 What type of attack is A?
What type of attack is A?
(Multiple Choice)
4.8/5  (34)
(34)
At larger companies, the cybersecurity program is usually the responsibility of a dedicated executive leader. This could include the
(Multiple Choice)
4.8/5  (36)
(36)
What is code used by hackers that is disguised as benign software but carries malicious code that may be activated via a logic bomb?
(Multiple Choice)
4.9/5  (37)
(37)
Colonial Pipeline, which provides almost 50% of the fuel for the East Coast, is an example of an attack of
(Multiple Choice)
4.7/5  (31)
(31)
Which of the following logical access attacks describes IP spoofing?
(Multiple Choice)
4.8/5  (36)
(36)
Match the cybersecurity threat to the following control activity:
-Review and update the baseline configuration of the information system as an integral part of information system component installations and upgrades.
(Multiple Choice)
4.7/5  (37)
(37)
What is a type of malware used by hackers that replicates without the assistance of human interaction?
(Multiple Choice)
4.9/5  (41)
(41)
Cybercriminals look for vulnerabilities in the network, through either a ________, who exposes valuable information or a ________ in the network.
(Multiple Choice)
4.9/5  (36)
(36)
What type of logical access attack disguises the source identity and impersonates a legitimate computer on the network?
(Multiple Choice)
4.8/5  (39)
(39)
RAM Manufacturing LLC is a rapidly growing manufacturer of parts for the automotive industry. Maeve is an IT auditor at RAM Manufacturing, working on a project for the Cybersecurity department. Maeve has prioritized the following cyberattack categories:
• Denial-of-service attacks
• Viruses
• Worms
• Logic bombs
• Trojan horses
Match the following attack description to one of these cyberattack categories.
-On Saturday, June 2nd, at exactly 12:00 noon, a program stopped allowing users to log in.
(Multiple Choice)
4.8/5  (36)
(36)
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is displayed below.
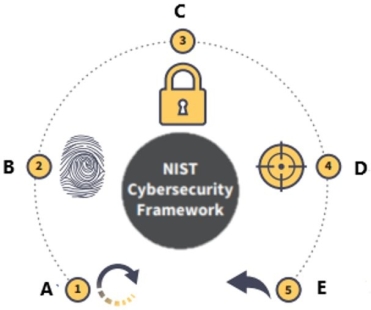 What is function A?
What is function A?
(Multiple Choice)
4.7/5  (36)
(36)
On-path attacks, which were once known as man-in-the-middle attacks, attempt to gain access to an ongoing communication between two endpoints. Which of the following is the definition of eavesdropping?
(Multiple Choice)
4.8/5  (42)
(42)
Showing 41 - 60 of 99
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)