Exam 16: Cybersecurity
Exam 1: Accounting As Information98 Questions
Exam 2: Risks and Risk Assessments100 Questions
Exam 3: Risk Management and Internal Controls100 Questions
Exam 4: Software and Systems106 Questions
Exam 5: Data Storage and Analysis98 Questions
Exam 6: Systems and Database Design98 Questions
Exam 7: Emerging and Disruptive Technologies100 Questions
Exam 8: Documenting Systems and Processes100 Questions
Exam 9: Human Resources and Payroll Processes100 Questions
Exam 10: Purchasing and Payments Process100 Questions
Exam 11: Conversion Processes100 Questions
Exam 12: Marketing, Sales, and Collection Processes100 Questions
Exam 13: Financial Reporting Processes103 Questions
Exam 14: Information Systems and Controls100 Questions
Exam 15: Fraud100 Questions
Exam 16: Cybersecurity99 Questions
Exam 17: Data Analytics99 Questions
Exam 18: Data Visualization100 Questions
Exam 19: Audit Assurance86 Questions
Select questions type
Which of the physical reconnaissance attacks is the unauthorized interception of communication?
(Multiple Choice)
4.9/5  (36)
(36)
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is displayed below.
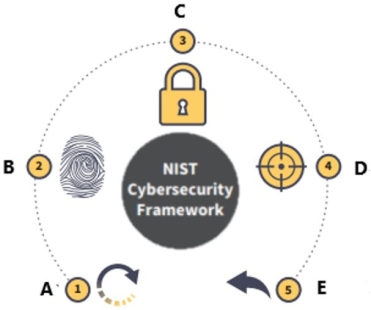 What is function D?
What is function D?
(Multiple Choice)
4.9/5  (36)
(36)
What type of logical access attack attempts to gain access to an on-going communication between two endpoints by pretending to be each of the parties?
(Multiple Choice)
4.8/5  (37)
(37)
What is it called when a company attempts to hack their own systems?
(Multiple Choice)
4.9/5  (32)
(32)
What does a company apply to ensure that systems are running up-to-date security when they are available?
(Multiple Choice)
4.8/5  (31)
(31)
Which of the physical reconnaissance attacks is looking through someone else's physical trash?
(Multiple Choice)
4.9/5  (37)
(37)
RAM Manufacturing LLC is a rapidly growing manufacturer of parts for the automotive industry. Maeve is an IT auditor at RAM Manufacturing, working on a project for the Cybersecurity department. Maeve has prioritized the following cyberattack categories:
• Denial-of-service attacks
• Viruses
• Worms
• Logic bombs
• Trojan horses
Match the following attack description to one of these cyberattack categories.
-Employees received an email with a funny meme that was forwarded throughout the company. The email contained a link that employees clicked on to view the meme. Users who clicked on the link in the email experienced unexpected pop-ups on their computers.
(Multiple Choice)
4.9/5  (41)
(41)
What is an attack that prohibits users from using resources such as computers, websites, servers, or an entire network called?
(Multiple Choice)
4.8/5  (36)
(36)
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is displayed below.
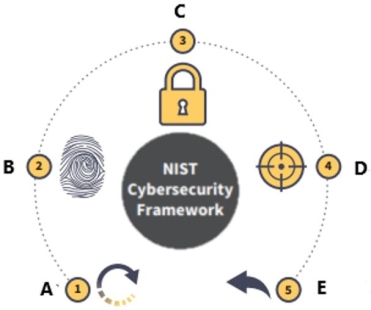 What is function B?
What is function B?
(Multiple Choice)
4.8/5  (50)
(50)
Which of the following is an example of a Denial-of-Service internal control?
(Multiple Choice)
4.9/5  (37)
(37)
Match the cybersecurity threat to the following control activity:
-Enforce a specified number of changed characters when new passwords are created.
(Multiple Choice)
4.9/5  (44)
(44)
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is divided into 18 control families. One of the control families is Maintenance. What ID does Maintenance family use?
(Multiple Choice)
4.8/5  (35)
(35)
NIST provides explicit guidelines that companies can require for password strength. What does NIST recommend for password construction?
(Multiple Choice)
4.9/5  (46)
(46)
Which of the following is an example of Malware internal controls?
(Multiple Choice)
4.7/5  (35)
(35)
A business can protect itself from DoS and DDoS attacks by ensuring that firewalls, routers, and ________ are up-to-date, are properly configured, and will automatically block the ports where fake requests enter the system.
(Multiple Choice)
4.8/5  (34)
(34)
What is an attack that uses destructive programs to take down a system called?
(Multiple Choice)
4.9/5  (33)
(33)
What is a type of malware used by hackers that replicates itself in a system and spreads quickly, causing damage to core system functions?
(Multiple Choice)
4.7/5  (29)
(29)
Showing 81 - 99 of 99
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)