Exam 16: Cybersecurity
Exam 1: Accounting As Information98 Questions
Exam 2: Risks and Risk Assessments100 Questions
Exam 3: Risk Management and Internal Controls100 Questions
Exam 4: Software and Systems106 Questions
Exam 5: Data Storage and Analysis98 Questions
Exam 6: Systems and Database Design98 Questions
Exam 7: Emerging and Disruptive Technologies100 Questions
Exam 8: Documenting Systems and Processes100 Questions
Exam 9: Human Resources and Payroll Processes100 Questions
Exam 10: Purchasing and Payments Process100 Questions
Exam 11: Conversion Processes100 Questions
Exam 12: Marketing, Sales, and Collection Processes100 Questions
Exam 13: Financial Reporting Processes103 Questions
Exam 14: Information Systems and Controls100 Questions
Exam 15: Fraud100 Questions
Exam 16: Cybersecurity99 Questions
Exam 17: Data Analytics99 Questions
Exam 18: Data Visualization100 Questions
Exam 19: Audit Assurance86 Questions
Select questions type
Which of the following is an example of a Denial-of-Service internal control?
(Multiple Choice)
5.0/5  (42)
(42)
Which of the physical reconnaissance attacks is a deceptive request designed to trick victims into sharing private information?
(Multiple Choice)
4.8/5  (38)
(38)
Which of the following is an example of Malware internal controls?
(Multiple Choice)
4.8/5  (34)
(34)
RAM Manufacturing LLC is a rapidly growing manufacturer of parts for the automotive industry. Maeve, an accountant at RAM Manufacturing recently received an email from Justin, the VP of Human Resources, asking her to click on a link and re-enter her login credentials and social security number. Suspicious of the email, Maeve forwarded the email to the Cybersecurity department. After talking with the cybersecurity department, Maeve decided to review her inbox to check for any other suspicious emails. Below is a list of what Maeve found:
a. An email reminder from the Human Resources department to enter her time for the month.
b. An email addressed to "Dear Accountant at RAM Manufacturing".
c. An email from a plant manager to escalate payment of an invoice, as the vendor won't ship needed steel until this invoice is paid.
d. A request from the CFO to transfer a large sum of money to an account that Maeve hadn't worked with before.
e. A request from a product manager to run a report on the costs involved in launching a new product the prior year.
Required: Do you think any of the emails are suspicious and why? Justify your answer by identifying the nature of the red flag or why it can be dismissed as suspicious.
(Essay)
4.8/5  (35)
(35)
An attacker force access to the network by attempting many passwords or phrases until finding the correct one. What type of attack is being described?
(Multiple Choice)
4.8/5  (40)
(40)
NIST provides explicit guidelines that companies can require for password strength. What is the NIST recommended length?
(Multiple Choice)
4.9/5  (41)
(41)
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is divided into 18 control families. One of the control families is System and Information Integrity. What ID does System and Information Integrity family use?
(Multiple Choice)
4.9/5  (41)
(41)
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is displayed below.
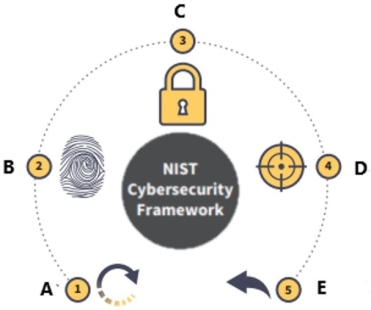 What is function C?
What is function C?
(Multiple Choice)
4.8/5  (38)
(38)
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is displayed below.
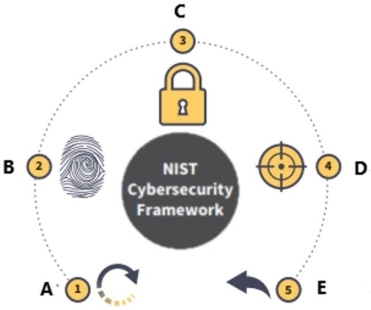 What is function E?
What is function E?
(Multiple Choice)
4.9/5  (39)
(39)
Match the cybersecurity threat to the following control activity:
-Ensure that the information system enforces minimum password complexity of specified case sensitivity, character numbers, and mix of uppercase and lowercase letters, including minimum requirements for each type.
(Multiple Choice)
4.8/5  (36)
(36)
What is a type of malicious code used by hackers that is programmed into a system and remains dormant until certain conditions are met?
(Multiple Choice)
4.8/5  (34)
(34)
For hackers to narrow their results, they use ________, which indicates which ports are open and sending or receiving data on the network.
(Multiple Choice)
4.9/5  (43)
(43)
NIST provides explicit guidelines that companies can require for password strength. What does NIST recommend for character types?
(Multiple Choice)
4.8/5  (34)
(34)
RAM Manufacturing LLC is a rapidly growing manufacturer of parts for the automotive industry. Justin, a newly hired Network Administrator, arrives at one of RAM Manufacturing's remote manufacturing facilities to perform a network upgrade. Justin approaches the main entrance and encounters Alison, a courier delivery person, waiting. Alison tells Justin that she delivers to the facility often and knows where the package goes. She asks if she could follow Justin in because she is behind schedule on her deliveries. Justin has never met Alison before. What should Justin do?
(Essay)
4.8/5  (39)
(39)
At larger companies, the cybersecurity program is usually the responsibility of a dedicated executive leader. This could include the
(Multiple Choice)
5.0/5  (34)
(34)
Attackers us these three types of attacks to plan, enter, and damage a victim's network:
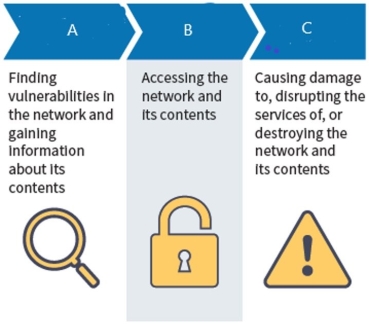 What type of attack is B?
What type of attack is B?
(Multiple Choice)
4.7/5  (38)
(38)
NIST provides explicit guidelines that companies can require for password strength. What is the NIST recommendation for resetting a password?
(Multiple Choice)
4.9/5  (34)
(34)
Which of the following is an example of Malware internal controls?
(Multiple Choice)
4.8/5  (41)
(41)
Showing 61 - 80 of 99
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)