Exam 12: Ethical Guidelines for Information Use
This theory of normative business ethics seeks to create value for people in a manner that is just and nondiscriminatory.
C
Explain how green computing can satisfy each of the three normative theories of business ethics.
Green computing can satisfy each of the three normative theories of business ethics - deontological, teleological, and virtue ethics - in the following ways:
1. Deontological ethics: This theory emphasizes the importance of following moral rules and duties. Green computing aligns with deontological ethics by adhering to the duty of minimizing harm to the environment. By reducing energy consumption, using sustainable materials, and properly disposing of electronic waste, businesses practicing green computing are fulfilling their duty to protect the environment and minimize their negative impact on society.
2. Teleological ethics: Also known as consequentialist ethics, this theory focuses on the outcomes or consequences of actions. Green computing can satisfy teleological ethics by producing positive outcomes for society and the environment. By reducing carbon emissions, conserving natural resources, and promoting sustainability, businesses practicing green computing are contributing to a healthier planet and better quality of life for future generations.
3. Virtue ethics: This theory emphasizes the development of moral character and virtues. Green computing aligns with virtue ethics by promoting the virtues of environmental stewardship, responsibility, and sustainability. Businesses that prioritize green computing demonstrate a commitment to these virtues, which can positively influence their organizational culture and reputation.
In conclusion, green computing can satisfy each of the three normative theories of business ethics by fulfilling duties to minimize harm, producing positive outcomes for society and the environment, and promoting moral virtues related to environmental stewardship and sustainability. By integrating green computing practices into their operations, businesses can demonstrate ethical behavior and contribute to a more sustainable and responsible business environment.
Match the situation below with the area of information control it falls under.
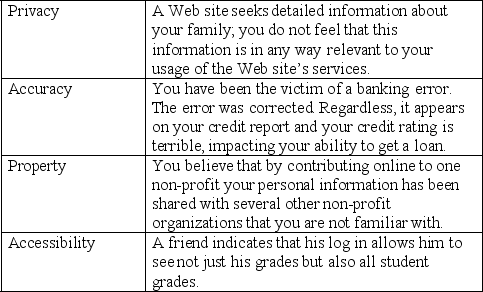
This is a growing service designed to help individuals and companies clean up their online presence so that a search for their name produces favorable results.
The European Union Directive on Data Protection does all of the following EXCEPT:
The European Union relies on a government data protection agency and specific privacy protection standards outlined in the ___________.
In TJX's case,the security breach made its customers vulnerable to this.
A manager that primarily focuses on the shareholders of the corporation rather than all of the vested parties in the businesses operations and activities is practicing which theory of normative business ethics?
In the chapter,there is the statement,"Internet companies are in business for the money and hence they really would prefer to keep their customers in the dark about how their personal data is being used to generate profits".Assuming this statement is true,with which ethical theory would you say these Internet companies are most aligned?
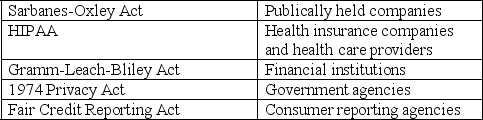
Match the U.S.legislative/regulatory act with the industry for which it governs the control of information.
This is a crime in which the thief uses a victim's personal information to impersonate the victim.
This term is used to define energy-efficient computing resources.
The question "What information does a person or an organization have a right or a privilege to obtain?" is part of this ethical issue.
Internal threats are considered the most lethal threat.What are they,why are they so lethal and what can a company do to protect against them?
A company should examine this area of the control of information if it wants to determine what data it has the right to monitor and capture from its employees.
Unlike the European Union,the U.S.has no general legislature ensuring Internet privacy rights.Instead,the U.S.encourages self-regulation and has introduced industry-specific regulations as needed.
Bradley Manning,a U.S.intelligence officer,took over 500,000 documents from the U.S.State Department and gave them to a public Web site called Wikileaks for publication.These documents were far ranging in their content. Match the actions below with the failure to control and the misuse of sensitive information.

Over time it becomes easier to maintain the accuracy of information.
Give an example of U.S.legislature designed to ensure the privacy and protection of information for a specific industry.
"Digital natives" are uncomfortable building relationships on the Internet because they understand the consequences of sharing information publically.
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)