Exam 12: Ethical Guidelines for Information Use
Exam 1: Linking Systems Strategy and the Organization47 Questions
Exam 2: Strategic Use of Information Resources in a Global Economy54 Questions
Exam 3: Organizational Strategy: Managerial Levers49 Questions
Exam 4: Work Design: Enabling Global Collaboration50 Questions
Exam 5: Building and Changing Global Business Processes55 Questions
Exam 6: Information Systems Strategy: Architecture and Infrastructure55 Questions
Exam 7: Cost Recovery of Information Systems67 Questions
Exam 8: Governance of the Information Systems Organization52 Questions
Exam 9: Sourcing Information Systems Around the World52 Questions
Exam 10: Managing Projects in a Global Ecosystem52 Questions
Exam 11: Business Analytics and Knowledge Management52 Questions
Exam 12: Ethical Guidelines for Information Use52 Questions
Select questions type
Match the managerial control concern with the challenges a manager may face on a regular basis.

(Not Answered)
This question doesn't have any answer yet
In today's digital word,individuals can control their privacy through ______,consent,and correction.
(Short Answer)
5.0/5  (31)
(31)
Google Flu Trends aggregates personal search data in order to estimate world-wide flu activity.Google's site has drawn criticism due to the sharing of users' online behavior without getting their consent.This,in essence,violates the user's right to:
(Multiple Choice)
4.7/5  (45)
(45)
"Who owns information?" and "What are the just and fair prices for its exchange?" are part of this ethical issue:
(Multiple Choice)
4.7/5  (38)
(38)
Many organizations and even consumers use this to control access to a network like the Internet,allowing only authorized traffic to pass.
(Multiple Choice)
4.8/5  (35)
(35)
Provide an example of a company that has faced a dilemma reconciling their corporate policies within a country where it hopes to operate.
(Essay)
4.8/5  (45)
(45)
Give reasons why users are so willing to forgo privacy on the Internet.
(Short Answer)
4.9/5  (44)
(44)
This is the term used to describe ethical dilemmas that arise with the development and application of IT.
(Multiple Choice)
4.8/5  (31)
(31)
Today's managers must ensure that information about their employees and customers is only available to those who have a right to see it and use it,an issue referred to as:
(Multiple Choice)
4.8/5  (41)
(41)
Match the security tool to its security category.
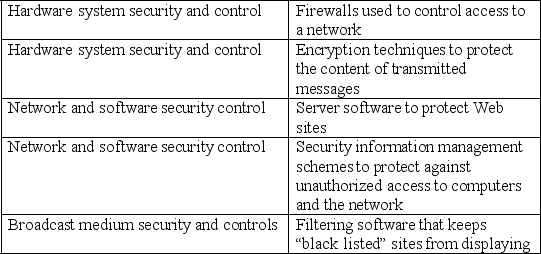
(Not Answered)
This question doesn't have any answer yet
Those who possess the "best" information and know how to use it,win.
(True/False)
4.9/5  (37)
(37)
Questions like "Who is responsible for the reliability of information?" and "Who will be accountable for errors in the information?" are part of this ethical issue.
(Multiple Choice)
4.9/5  (39)
(39)
Which normative theory of business ethics would TJX have displayed if it had informed customers as soon as the breach was corrected and told other retailers how to prevent future security breaches?
(Multiple Choice)
4.9/5  (35)
(35)
All of the following are examples of green computing EXCEPT:
(Multiple Choice)
4.9/5  (39)
(39)
What security and controls should a company use to protect its computer infrastructure? Why do managers need to be involved in the decisions about security and control measures?
(Not Answered)
This question doesn't have any answer yet
In today's digital word,individuals can control their privacy through choice,______ ,and correction.
(Multiple Choice)
4.9/5  (41)
(41)
The concern about privacy on Facebook and other social media sites is greater in the U.S.than it is in Europe.
(True/False)
5.0/5  (33)
(33)
Green computing is often associated with supporting the triple bottom line known as:
(Multiple Choice)
4.8/5  (42)
(42)
The social contract theory is made up of two distinct components - social welfare and _________.
(Short Answer)
4.9/5  (26)
(26)
List the four areas,as outlined in the text,which deal with control of information.
(Essay)
4.9/5  (36)
(36)
Showing 21 - 40 of 52
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)