Exam 7: Wireless Networking
Exam 1: Browser Basics149 Questions
Exam 2: Basic Communication on the Internet: Email150 Questions
Exam 3: Searching the Web150 Questions
Exam 4: Information Resources on the Web149 Questions
Exam 5: User-Generated Content on the Internet150 Questions
Exam 6: Internet Security150 Questions
Exam 7: Wireless Networking147 Questions
Exam 8: Creating Effective Web Pages149 Questions
Exam 9: Electronic Commerce150 Questions
Select questions type
MATCHING
-a standard developed by the Wi-Fi Alliance to address inherent weaknesses in WEP
(Multiple Choice)
4.7/5  (37)
(37)
The action of issuing a command to delete everything stored on a wireless device is sometimes called a(n) ____________________ wipe.
(Short Answer)
4.8/5  (36)
(36)
Devices using infrared technology can easily beam information across a crowded room, or even around a corner.
(True/False)
4.9/5  (35)
(35)
Voice over Internet Protocol converts audio signals to digital packets so that you can use a broadband Internet connection to make telephone calls. _________________________
(True/False)
4.8/5  (42)
(42)
An "evil twin" attack involves a hacker standing close to the user of a wireless device in an attempt to spot login information, passwords, and other sensitive data.
(True/False)
4.8/5  (33)
(33)
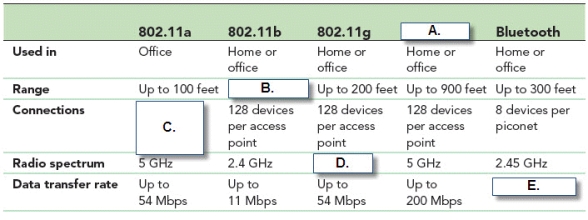 -In the accompanying figure, Box "A." represents the column heading "____".
-In the accompanying figure, Box "A." represents the column heading "____".
(Multiple Choice)
4.7/5  (36)
(36)
Like most people of her generation, Martha has used cell phones for years. But she never gave much thought to the details of the technology. Now that she has graduated from college and is about to join the workforce, she's trying to determine what kind of cellular technology will be most useful to her.
-Martha is about to buy her cell phone, and plans to use as many of its features as possible. She discovers that 4G wireless networks can process many tasks at the same time, a feature sometimes called ____ support.
(Multiple Choice)
4.9/5  (34)
(34)
Pavel is trying to understand the differences between the major Wi-Fi standards. He asks you to quiz him.
-You ask Pavel which Wi-Fi standard would be typically found in a home setting. Pavel tells you the answer is ____.
(Multiple Choice)
4.8/5  (39)
(39)
Pavel is trying to understand the differences between the major Wi-Fi standards. He asks you to quiz him.
-You tell Pavel that he needs to set up a Wi-Fi network whose range will need to be about 350 feet. Pavel tells you that you need to use ____ devices.
(Multiple Choice)
4.8/5  (38)
(38)
A(n) MiFi device is a small, battery-operated, mobile personal hotspot for connecting Wi-Fi devices to the Internet. _________________________
(True/False)
4.9/5  (35)
(35)
When WEP is enabled, it ____________________ the data sent over the network.
(Short Answer)
4.7/5  (29)
(29)
Currently, WWANs provide wireless connections to the Internet using ____ networks created by cellular phone carriers.
(Multiple Choice)
4.8/5  (38)
(38)
If you change the default name of the wireless router or access point, you also prevent unknown users from detecting your network by attempting to randomly connect to a wireless network using a manufacturer name or the word "____" as an SSID.
(Multiple Choice)
4.9/5  (36)
(36)
MATCHING
-converts audio signals to digital packets for making phone calls via the Internet
(Multiple Choice)
4.7/5  (38)
(38)
A ____ attack occurs when transmissions, such as messages between users, logins, and normal connections with Web servers, that are being sent between two devices are intercepted by a third party.
(Multiple Choice)
4.8/5  (29)
(29)
WiMAX network in a metropolitan area
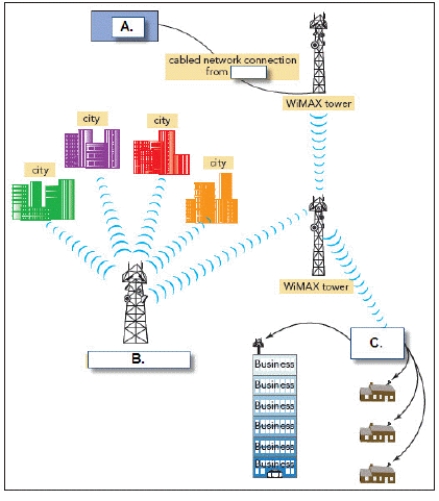 -In the accompanying figure, "C." represents WiMAX ____________________.
-In the accompanying figure, "C." represents WiMAX ____________________.
(Short Answer)
4.8/5  (33)
(33)
Disabling the SSID broadcast of a network makes that network ____ to roaming devices.
(Multiple Choice)
4.8/5  (32)
(32)
Showing 21 - 40 of 147
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)