Exam 7: Wireless Networking
Exam 1: Browser Basics149 Questions
Exam 2: Basic Communication on the Internet: Email150 Questions
Exam 3: Searching the Web150 Questions
Exam 4: Information Resources on the Web149 Questions
Exam 5: User-Generated Content on the Internet150 Questions
Exam 6: Internet Security150 Questions
Exam 7: Wireless Networking147 Questions
Exam 8: Creating Effective Web Pages149 Questions
Exam 9: Electronic Commerce150 Questions
Select questions type
To protect a Bluetooth device from "bluejacking," you can set it to ____________________ mode.
(Short Answer)
4.8/5  (34)
(34)
A "cafe latte" attack is another name for a(n) ____ attack.
(Multiple Choice)
4.8/5  (34)
(34)
When WEP is enabled, it encrypts data sent over a network using a key, sometimes also called a(n) passphrase, that is entered by the user. _________________________
(True/False)
4.8/5  (35)
(35)
MATCHING
-a relatively harmless attack that merely sends an anonymous message
(Multiple Choice)
4.8/5  (30)
(30)
Because the 2.4 Ghz radio spectrum is ____________________, it is free.
(Short Answer)
4.9/5  (36)
(36)
Name at least 5 of the 8 things noted in the security checklist for installing a wireless router or access point.
(Essay)
4.9/5  (26)
(26)
Wired Passphrase Encryption (WPE) is a security protocol for wireless LANs that works by encrypting data sent over the network.
(True/False)
4.8/5  (36)
(36)
In a(n) ____ attack, a hacker sets up a computer to act as a legitimate access point, and then steals personal information from users trying to connect to it.
(Multiple Choice)
4.7/5  (35)
(35)
WWAN networking provides wireless connections to the Internet using networks created by cellular phone carriers.
(True/False)
4.7/5  (28)
(28)
A(n) ____________________ is a hardware device with one or more antennae that permit communication between wired and wireless networks so wireless clients can send and receive data.
(Short Answer)
4.8/5  (36)
(36)
If you have both WPA and WEP available to you, your system will be most secure if you use ____.
(Multiple Choice)
4.8/5  (38)
(38)
A WiMAX coverage area between the base station and devices varies based on the geography of the area, but most of these hotspots are approximately ____ square miles.
(Multiple Choice)
4.9/5  (26)
(26)
When you see the term "Wi-Fi," it most often refers to the 802.11 ____ standard.
(Multiple Choice)
4.9/5  (35)
(35)
Phishing is the act of driving through a neighborhood looking for unsecured wireless networks.
(True/False)
4.7/5  (37)
(37)
Text messages were first made available to cell phone users with the advent of ____ technology.
(Multiple Choice)
4.9/5  (30)
(30)
The most serious security threat to Bluetooth-enabled devices is ____, which occurs when a hacker gains access to the device and its functions without the owner's consent.
(Multiple Choice)
4.7/5  (38)
(38)
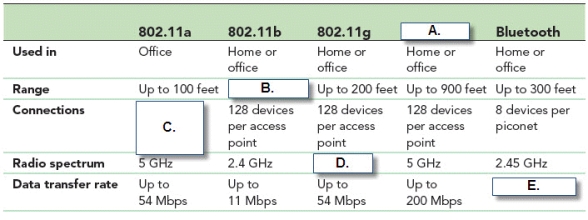 -In the accompanying figure, Box "E." should show a data transfer rate of up to ____ Mbps.
-In the accompanying figure, Box "E." should show a data transfer rate of up to ____ Mbps.
(Multiple Choice)
4.8/5  (31)
(31)
Showing 121 - 140 of 147
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)