Exam 7: Wireless Networking
Exam 1: Browser Basics149 Questions
Exam 2: Basic Communication on the Internet: Email150 Questions
Exam 3: Searching the Web150 Questions
Exam 4: Information Resources on the Web149 Questions
Exam 5: User-Generated Content on the Internet150 Questions
Exam 6: Internet Security150 Questions
Exam 7: Wireless Networking147 Questions
Exam 8: Creating Effective Web Pages149 Questions
Exam 9: Electronic Commerce150 Questions
Select questions type
With WEP encryption, the key being used to encrypt the data is sent over the network ____ the actual data is encrypted.
(Multiple Choice)
4.9/5  (32)
(32)
In 1994, cellular phone carriers created the first commercial digital networks, with a data transfer rate of ____.
(Multiple Choice)
4.9/5  (27)
(27)
A security problem associated with Bluetooth devices is ____.
(Multiple Choice)
4.9/5  (31)
(31)
To access the Internet using a WWAN, you need a WWAN PC card and ____.
(Multiple Choice)
4.8/5  (31)
(31)
Hackers use ____ programs to monitor activity on a wireless network in order to obtain personal information that unsuspecting users might transmit.
(Multiple Choice)
4.8/5  (37)
(37)
Like most people of her generation, Martha has used cell phones for years. But she never gave much thought to the details of the technology. Now that she has graduated from college and is about to join the workforce, she's trying to determine what kind of cellular technology will be most useful to her.
-Martha discovers that when mobile devices combine the functionality of a cell phone with an operating system that performs these and other functions, they are usually called ____.
(Multiple Choice)
4.8/5  (37)
(37)
According to the text, ____ is a company that provides subscription-based Wi-Fi service for visitors at many U.S. airports.
(Multiple Choice)
4.8/5  (31)
(31)
A collection of devices connected via Bluetooth technology is called a(n) ____.
(Multiple Choice)
4.9/5  (33)
(33)
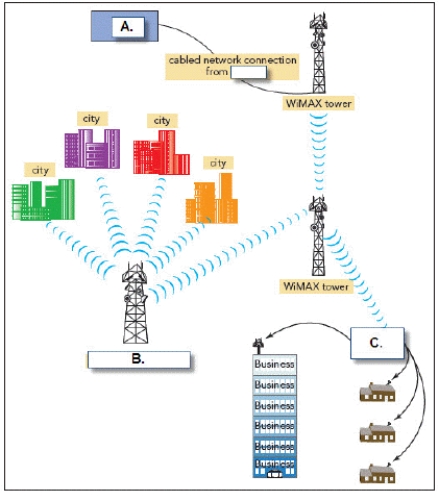 -In the accompanying figure, box "A." is connected to the WiMAX tower through a cabled network connection from a(n) ____.
-In the accompanying figure, box "A." is connected to the WiMAX tower through a cabled network connection from a(n) ____.
(Multiple Choice)
4.8/5  (40)
(40)
MATCHING
-a security attack using physical proximity to gain someone's personal information
(Multiple Choice)
4.7/5  (33)
(33)
One of the most serious mistakes that home users make when installing a wireless network is ____.
(Multiple Choice)
4.9/5  (34)
(34)
Using physical proximity to gain login information, passwords, or other personal information is known as a(n) ____.
(Multiple Choice)
4.9/5  (37)
(37)
Most experts recommend that, when you leave for vacation, you should change the passphrase to your wireless network for security. _________________________
(True/False)
5.0/5  (39)
(39)
In a wireless mesh network, the number of nodes that need to be wired to an Internet connection is one. _________________________
(True/False)
4.8/5  (30)
(30)
The "MAC" in the term "MAC address" is short for "Media ____________________"
(Short Answer)
4.8/5  (30)
(30)
In most cases, WLAN network connections are possible within 200 to ____________________ feet of the access point, depending on any obstacles to radio waves.
(Short Answer)
4.8/5  (27)
(27)
A 128-bit key contains ____________________ hexadecimal characters.
(Short Answer)
4.7/5  (38)
(38)
Showing 81 - 100 of 147
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)