Exam 12: Managing Systems Support and Security
Exam 1: Introduction to Systems Analysis and Design80 Questions
Exam 2: Analyzing the Business Case81 Questions
Exam 3: Managing Systems Projects78 Questions
Exam 4: Requirements Modeling98 Questions
Exam 5: Data and Process Modeling84 Questions
Exam 6: Object Modeling78 Questions
Exam 7: Development Strategies82 Questions
Exam 8: User Interface Design82 Questions
Exam 9: Data Design86 Questions
Exam 10: System Architecture78 Questions
Exam 11: Managing Systems Implementation81 Questions
Exam 12: Managing Systems Support and Security81 Questions
Exam 13: Toolkit A: The Systems Analysts Toolkit45 Questions
Exam 14: Toolkit B: Case Tools44 Questions
Exam 15: Toolkit C: Financial Analysis Tools45 Questions
Exam 16: Toolkit D: Internet Resource Tools44 Questions
Select questions type
Another of George's clients has software that is outdated and has become increasingly vulnerable to attack. How does George categorize this threat?
Free
(Multiple Choice)
4.8/5  (34)
(34)
Correct Answer:
B
As enterprise-wide information systems grow more complex, configuration management becomes trivial.
Free
(True/False)
4.8/5  (36)
(36)
Correct Answer:
False
_____ includes monitoring a system for signs of trouble, logging all system failures, diagnosing the problem, and applying corrective action.
Free
(Multiple Choice)
4.9/5  (39)
(39)
Correct Answer:
D
In maintenance management, _____ involves studying the parts of a system to understand the overall system.
(Multiple Choice)
5.0/5  (29)
(29)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-Combination of hardware and software that allows computers to interact with a network
(Multiple Choice)
4.7/5  (38)
(38)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-A risk control strategy that reduces the impact of a risk by careful planning and preparation
(Multiple Choice)
4.8/5  (29)
(29)
In a secluded engineering attack, an intruder uses social interaction to gain access to a computer system.
(True/False)
4.9/5  (30)
(30)
_____ costs include expenses for items such as supplies, equipment rental, and software leases.
(Multiple Choice)
4.9/5  (38)
(38)
Many IT departments also use a job title of _____ to designate positions that require a combination of systems analysis and programming skills.
(Multiple Choice)
4.9/5  (38)
(38)
A _____ is the main line of defense between a local network, or intranet, and the Internet.
(Multiple Choice)
4.8/5  (31)
(31)
_____ is the overall time between a request for system activity and the delivery of the response.
(Multiple Choice)
4.8/5  (34)
(34)
The first step in managing IT security is to develop a _____ based on confidentiality, integrity, and availability.
(Multiple Choice)
4.8/5  (36)
(36)
A(n) _____ is an attack that takes advantage of a vulnerability.
(Multiple Choice)
4.9/5  (37)
(37)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-A risk control strategy that shifts risks to another asset or party
(Multiple Choice)
4.9/5  (33)
(33)
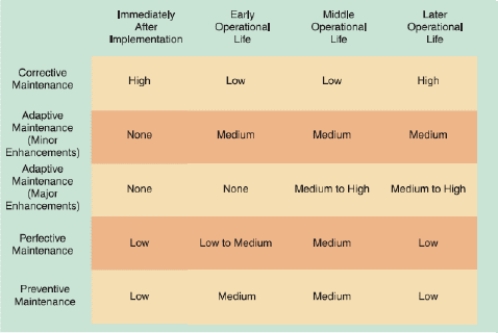 -As shown in the accompanying figure, maintenance expenses usually are high when a system is implemented because problems must be detected, investigated, and resolved by _____.
-As shown in the accompanying figure, maintenance expenses usually are high when a system is implemented because problems must be detected, investigated, and resolved by _____.
(Multiple Choice)
4.8/5  (38)
(38)
The systems support and _____ phase begins when a system becomes operational and continues until the system reaches the end of its useful life.
(Multiple Choice)
4.8/5  (30)
(30)
Showing 1 - 20 of 81
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)