Exam 12: Managing Systems Support and Security
Exam 1: Introduction to Systems Analysis and Design80 Questions
Exam 2: Analyzing the Business Case81 Questions
Exam 3: Managing Systems Projects78 Questions
Exam 4: Requirements Modeling98 Questions
Exam 5: Data and Process Modeling84 Questions
Exam 6: Object Modeling78 Questions
Exam 7: Development Strategies82 Questions
Exam 8: User Interface Design82 Questions
Exam 9: Data Design86 Questions
Exam 10: System Architecture78 Questions
Exam 11: Managing Systems Implementation81 Questions
Exam 12: Managing Systems Support and Security81 Questions
Exam 13: Toolkit A: The Systems Analysts Toolkit45 Questions
Exam 14: Toolkit B: Case Tools44 Questions
Exam 15: Toolkit C: Financial Analysis Tools45 Questions
Exam 16: Toolkit D: Internet Resource Tools44 Questions
Select questions type
_____ prevents unauthorized users from creating, modifying, or deleting information.
(Multiple Choice)
4.9/5  (31)
(31)
_____ include changing programs, procedures, or documentation to ensure correct system performance; adapting the system to changing requirements; and making the system operate more efficiently.
(Multiple Choice)
4.9/5  (34)
(34)
Both adaptive and perfective maintenance activities decrease in a dynamic business environment.
(True/False)
4.9/5  (31)
(31)
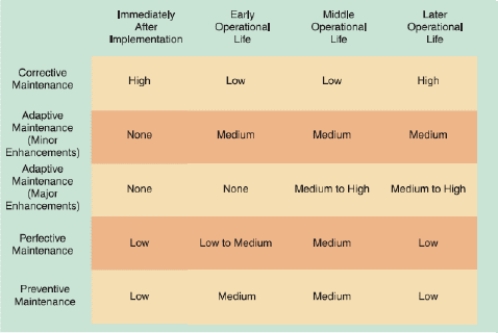 -As shown in the accompanying figure, once a system becomes stable, maintenance costs usually remain low and involve minor _____ maintenance.
-As shown in the accompanying figure, once a system becomes stable, maintenance costs usually remain low and involve minor _____ maintenance.
(Multiple Choice)
4.7/5  (26)
(26)
A help desk can boost its productivity by using _____, which allows IT staff to take over a user's workstation and provide support and troubleshooting.
(Multiple Choice)
5.0/5  (28)
(28)
Typically, an intruder accesses a system using a compromised account, and may attempt a(n) _____, which is an unauthorized attempt to increase permission levels.
(Multiple Choice)
4.9/5  (31)
(31)
In a broad sense, credentials include formal degrees, diplomas, or certificates granted by learning institutions to show that a certain level of education has been achieved.
(True/False)
4.9/5  (36)
(36)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-Uses analytical techniques to identify potential quality and performance improvements in an information system
(Multiple Choice)
4.8/5  (32)
(32)
_____ develops safeguards that reduce risks and their impact.
(Multiple Choice)
4.8/5  (38)
(38)
_____ ensures that authorized users have timely and reliable access to necessary information.
(Multiple Choice)
4.8/5  (35)
(35)
The hardening process that makes a system more secure is fully automatic.
(True/False)
4.9/5  (27)
(27)
In a public key encryption environment, each user on the network has a pair of keys: a foreign key and a private key.
(True/False)
4.9/5  (34)
(34)
_____ protects information from unauthorized disclosure and safeguards privacy.
(Multiple Choice)
4.7/5  (26)
(26)
A(n) _____ is a centralized resource staffed by IT professionals who provide users with the support they need to do their jobs.
(Multiple Choice)
4.9/5  (32)
(32)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-Records everything that is typed into the keyboard, including passwords, while the system continues to function normally
(Multiple Choice)
4.9/5  (30)
(30)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-Hostile act that targets systems or a company itself
(Multiple Choice)
4.9/5  (39)
(39)
The _____ is the configuration of a system documented at the beginning of the project and consists of all necessary system requirements and design constraints.
(Multiple Choice)
4.8/5  (36)
(36)
_____ is a process for controlling changes in system requirements during software development.
(Multiple Choice)
4.8/5  (38)
(38)
Showing 21 - 40 of 81
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)