Exam 7: Connecting to the Internet
Exam 1: Getting Started75 Questions
Exam 2: Looking at Windows75 Questions
Exam 3: Installing and Using Software75 Questions
Exam 4: File Basics75 Questions
Exam 5: Organizing Files and Folders75 Questions
Exam 6: Protecting Files75 Questions
Exam 7: Connecting to the Internet74 Questions
Exam 8: Browsing and Searching the Web74 Questions
Exam 9: Sending E-Mail and Attachments75 Questions
Exam 10: Writing and Printing Documents75 Questions
Exam 11: Working With Spreadsheets75 Questions
Exam 12: Accessing Databases75 Questions
Exam 13: Making Presentations75 Questions
Exam 14: Recording and Editing Sound75 Questions
Exam 15: Working With Graphics75 Questions
Exam 16: Creating Desktop Video and Animation75 Questions
Exam 17: Looking Under the Hood75 Questions
Exam 18: Computing Programming75 Questions
Select questions type
The original wireless encryption was called ____________________ because it was designed to provide a level of confidentiality similar to that of a wired network.
(Short Answer)
4.8/5  (28)
(28)
Preventing Wi-Fi signal interception is difficult, but ____ transmitted data makes it useless to intruders.
(Multiple Choice)
4.8/5  (42)
(42)
Case-Based Critical Thinking Questions Case 7-1 Toby is looking into purchasing Internet service. He is researching the different types of service that are available to him and trying to figure out what best suits his needs. Toby lives in the city near high-speed cellular communication towers. Through his research, he has learned that ____ Internet service may be two good options.
(Multiple Choice)
4.9/5  (38)
(38)
A computer can have a temporarily assigned ____________________ IP address.
(Short Answer)
4.9/5  (37)
(37)
Comcast, Cox, and Charter are examples of local and national ____________________ companies.
(Short Answer)
4.9/5  (44)
(44)
Ethernet is a wired network technology used on LANs as well as on the Internet.
(True/False)
5.0/5  (41)
(41)
As the result of a(n) ____, software can be surreptitiously installed and operated under the remote control of a hacker.
(Multiple Choice)
4.8/5  (29)
(29)
Describe the most common ways of gaining unauthorized access to a network-based computer.
(Essay)
4.7/5  (31)
(31)
A broadband Internet access technology that runs over standard phone lines is called ____.
(Multiple Choice)
4.9/5  (34)
(34)
Case-Based Critical Thinking Questions Case 7-1 Toby is looking into purchasing Internet service. He is researching the different types of service that are available to him and trying to figure out what best suits his needs. Toby has a wireless connection to the Internet. The first thing that he wants to do is purchase a gift for a friend online. Toby needs to prevent Wi-Fi signal interception, so his Wi-Fi network should be protected by ____.
(Multiple Choice)
5.0/5  (42)
(42)
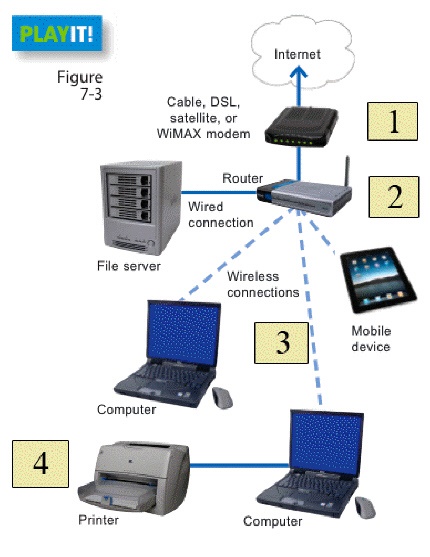 In the figure above, which item represents the device used to connect to the Internet?
In the figure above, which item represents the device used to connect to the Internet?
(Multiple Choice)
4.9/5  (41)
(41)
Some Internet connections are symmetrical, which means that the ____ speed of data traveling from your computer to the Internet is the same as the downstream speed of data traveling from the Internet to your computer.
(Multiple Choice)
4.9/5  (31)
(31)
The TCP/IP protocol divides documents, e-mail, photos, and other digital messages into standard-sized ____ of data.
(Multiple Choice)
4.9/5  (37)
(37)
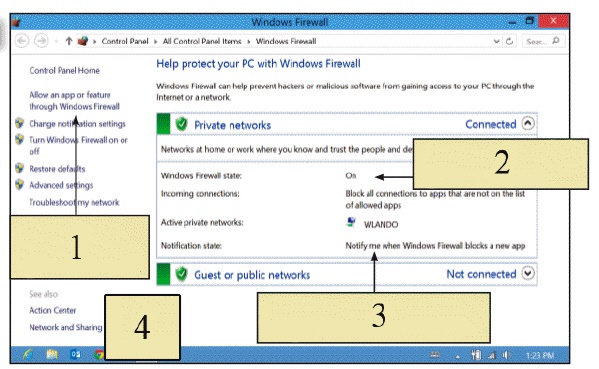 In the figure above, which item points to the option to adjust settings to specify what is allowed and what is blocked by the firewall?
In the figure above, which item points to the option to adjust settings to specify what is allowed and what is blocked by the firewall?
(Multiple Choice)
4.7/5  (36)
(36)
Cable Internet service uses a voiceband modem and telephone lines to transport data between your computer and your ISP.
(True/False)
4.8/5  (34)
(34)
An intrusion is any access to data or programs by hackers, criminals, or other unauthorized persons.
(True/False)
4.9/5  (34)
(34)
TCP/IP divides documents, e-mails, photos, and other digital messages into standard-sized packets of data.
(True/False)
4.8/5  (44)
(44)
Showing 21 - 40 of 74
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)