Exam 9: Sending E-Mail and Attachments
Exam 1: Getting Started75 Questions
Exam 2: Looking at Windows75 Questions
Exam 3: Installing and Using Software75 Questions
Exam 4: File Basics75 Questions
Exam 5: Organizing Files and Folders75 Questions
Exam 6: Protecting Files75 Questions
Exam 7: Connecting to the Internet74 Questions
Exam 8: Browsing and Searching the Web74 Questions
Exam 9: Sending E-Mail and Attachments75 Questions
Exam 10: Writing and Printing Documents75 Questions
Exam 11: Working With Spreadsheets75 Questions
Exam 12: Accessing Databases75 Questions
Exam 13: Making Presentations75 Questions
Exam 14: Recording and Editing Sound75 Questions
Exam 15: Working With Graphics75 Questions
Exam 16: Creating Desktop Video and Animation75 Questions
Exam 17: Looking Under the Hood75 Questions
Exam 18: Computing Programming75 Questions
Select questions type
A(n) ____ is a file that travels along with an e-mail message.
Free
(Multiple Choice)
4.7/5  (39)
(39)
Correct Answer:
A
An e-mail-based scam that's designed to persuade you to reveal confidential information is called ____.
Free
(Multiple Choice)
5.0/5  (38)
(38)
Correct Answer:
B
A(n) ____ is a type of utility software that captures unsolicited e-mail messages before they reach your Inbox.
Free
(Multiple Choice)
4.9/5  (29)
(29)
Correct Answer:
B
Unread mail is usually displayed in ____, and that feature helps to ensure that you've not missed an important message.
(Multiple Choice)
4.7/5  (27)
(27)
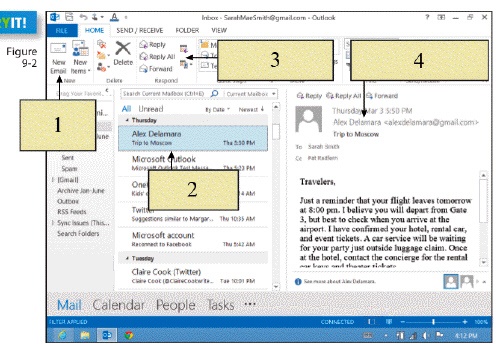 New mail is downloaded to the ____, represented by item 2 in the figure above.
New mail is downloaded to the ____, represented by item 2 in the figure above.
(Multiple Choice)
4.7/5  (37)
(37)
Your e-mail client might provide a way to prioritize messages, allowing you to deal with the most urgent correspondence first.
(True/False)
4.8/5  (33)
(33)
____ replaces a series of similarity colored pixels with a binary code that indicates the number of pixels and their colors.
(Multiple Choice)
4.9/5  (38)
(38)
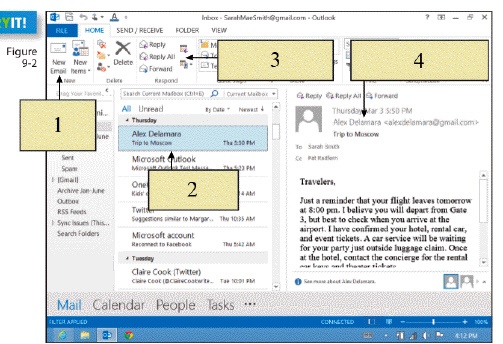 To compose a new e-mail message, you would click on ____ in the figure above.
To compose a new e-mail message, you would click on ____ in the figure above.
(Multiple Choice)
4.8/5  (21)
(21)
Case-Based Critical Thinking Questions Case 9-1 Tara has just gotten her first computer connected to the Internet. She is very excited to start e-mailing her friends and family. Tara has obtained an e-mail address and is ready to begin sending messages to her family and friends. Her Aunt Jane has just sent her the very first e-mail and she is excited and wants to forward it to her mom. The easiest way for her to forward her message is to ____.
(Multiple Choice)
4.8/5  (34)
(34)
The information required to obtain an e-mail address includes a user ID and ____.
(Multiple Choice)
5.0/5  (31)
(31)
When using a private computer to access your e-mail account, it is important to log off when you are done to make sure that unauthorized persons do not use your account.
(True/False)
4.9/5  (41)
(41)
A spam filter is a type of utility software that captures unsolicited e-mail messages before they reach your Inbox.
(True/False)
4.9/5  (34)
(34)
Most ____ techniques have adjustable compression levels so that you can decide how much data you can afford to lose.
(Multiple Choice)
4.8/5  (36)
(36)
When working with file types that do not offer built-in compression, you can use a standalone compression ____ to shrink the size of a file that you have saved in a non-compressed format.
(Multiple Choice)
4.8/5  (35)
(35)
The person who receives an attachment can double-click the ____ to open the attachment.
(Multiple Choice)
4.7/5  (34)
(34)
To get your mail, connect to the mail server and download new messages to your ____.
(Multiple Choice)
4.9/5  (40)
(40)
The ____________________ is a folder on your PC's hard disk that temporarily stores outgoing e-mail messages.
(Short Answer)
4.9/5  (34)
(34)
Showing 1 - 20 of 75
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)