Exam 8: Security Issues and Ethics in Education
Exam 1: Integrating Educational Technology Into the Curriculum102 Questions
Exam 2: Communications Networks the Internet and the World Wide Web103 Questions
Exam 3: Software for Educators102 Questions
Exam 4: Hardware for Educators103 Questions
Exam 5: Technology Digital Media and Curriculum Integration103 Questions
Exam 6: The Changing Face of Education 2d Teaching Online103 Questions
Exam 7: Evaluating Educational Technology and Integration Strategies103 Questions
Exam 8: Security Issues and Ethics in Education103 Questions
Select questions type
A community/state site license normally does not provide substantial savings over single-use licenses.
(True/False)
4.8/5  (41)
(41)
____ is a scam in which a perpetrator sends an official-looking e-mail that attempts to obtain personal and financial information from the recipient.
(Multiple Choice)
4.9/5  (34)
(34)
People who try to access computer systems illegally are called ____________________.
(Short Answer)
4.8/5  (29)
(29)
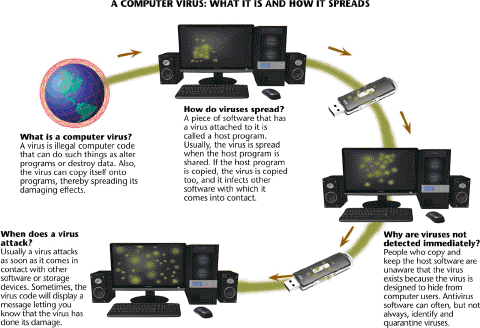 All of the following are true concerning viruses like those described in the accompanying figure EXCEPT ____.
All of the following are true concerning viruses like those described in the accompanying figure EXCEPT ____.
(Multiple Choice)
4.9/5  (43)
(43)
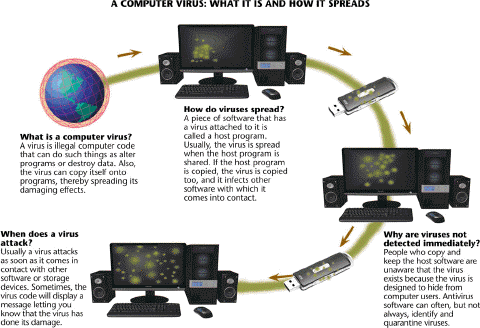 Most viruses like those described in the accompanying figure are harmless pranks that cause no permanent damage.
Most viruses like those described in the accompanying figure are harmless pranks that cause no permanent damage.
(True/False)
4.9/5  (48)
(48)
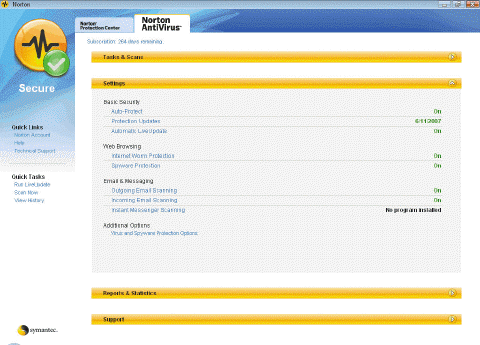 A(n) ____ disc is normally a CD that contains an uninfected copy of key operating system commands and startup information that enables the computer to restart correctly; this kind of disc may be required in some circumstances by the program in the accompanying figure.
A(n) ____ disc is normally a CD that contains an uninfected copy of key operating system commands and startup information that enables the computer to restart correctly; this kind of disc may be required in some circumstances by the program in the accompanying figure.
(Multiple Choice)
4.9/5  (34)
(34)
A(n) ____________________ allows network users to share a single copy of the software, which resides on the network server.
(Short Answer)
4.8/5  (34)
(34)
Many display devices and keyboards have features that help address ergonomic issues.
(True/False)
4.8/5  (29)
(29)
____ prevents your browser from displaying materials from targeted sites or sites that contain certain keywords or phrases.
(Multiple Choice)
4.8/5  (40)
(40)
In case a file is corrupted or destroyed, a user can utilize the backup copies to ____________________, or reload, the files on a computer.
(Short Answer)
4.9/5  (48)
(48)
Copyright laws protect original materials created by students and teachers and published on the Web.
(True/False)
4.7/5  (37)
(37)
Critical Thinking Case 8-1
Your computer is not behaving normally and you need to investigate.
You discover that the computer has limited resources and shuts down frequently. Which of the following viruses might your computer have?
(Multiple Choice)
4.8/5  (40)
(40)
____________________ is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once.
(Short Answer)
4.8/5  (38)
(38)
An Acceptable Use Policy (AUP) is a set of rules that governs the use of school and school district computers, networks, and the Internet by teachers, administrators, staff, and students. Briefly describe guidelines that many AUPs contain.
(Essay)
4.9/5  (41)
(41)
____ applies to all creative works and provides certain rights to authors.
(Multiple Choice)
4.8/5  (35)
(35)
Any illegal act involving a computer generally is referred to as a computer crime.
(True/False)
4.8/5  (43)
(43)
Showing 81 - 100 of 103
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)