Exam 8: Security Issues and Ethics in Education
Exam 1: Integrating Educational Technology Into the Curriculum102 Questions
Exam 2: Communications Networks the Internet and the World Wide Web103 Questions
Exam 3: Software for Educators102 Questions
Exam 4: Hardware for Educators103 Questions
Exam 5: Technology Digital Media and Curriculum Integration103 Questions
Exam 6: The Changing Face of Education 2d Teaching Online103 Questions
Exam 7: Evaluating Educational Technology and Integration Strategies103 Questions
Exam 8: Security Issues and Ethics in Education103 Questions
Select questions type
A well-known time bomb virus is the ____ virus, which destroys files on March 6.
(Multiple Choice)
4.7/5  (42)
(42)
____ is the use of a computer or data for unapproved or possibly illegal activities.
(Multiple Choice)
4.8/5  (35)
(35)
A ____ virus replaces the program that is used to start the computer system with a modified, infected version of the startup program.
(Multiple Choice)
4.7/5  (37)
(37)
Storing backup copies at another location, called a(n) ____________________, is an additional precaution often overlooked by schools and home users.
(Short Answer)
4.9/5  (38)
(38)
A ____ allows network users to share a single copy of the software.
(Multiple Choice)
4.7/5  (31)
(31)
____ computing involves reducing the use of electricity and the production of environmental waste while using a computer.
(Multiple Choice)
4.9/5  (43)
(43)
Unauthorized access is the use of a computer system or data for unapproved purposes.
(True/False)
4.9/5  (41)
(41)
Any item that you must carry to gain access to a computer or computer facility is called a(n) ____.
(Multiple Choice)
4.8/5  (41)
(41)
A(n) ____ occurs when the incoming electrical power increases significantly above the normal 120 volts.
(Multiple Choice)
4.8/5  (40)
(40)
A security system consisting of hardware and/or software that prevents unauthorized access to data and information on a network is called a(n) ____.
(Multiple Choice)
4.9/5  (36)
(36)
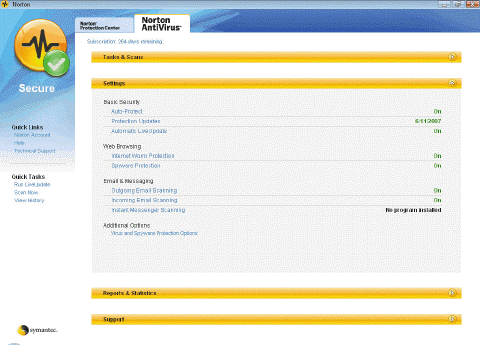 Antivirus programs like the one in the accompanying figure also are called ____.
Antivirus programs like the one in the accompanying figure also are called ____.
(Multiple Choice)
4.8/5  (35)
(35)
Critical Thinking Case 8-2
You believe that your information privacy has been violated. You receive a great deal of e-mail from companies trying to sell something. Which of the following is a likely cause of all the e-mail?
(Multiple Choice)
4.7/5  (35)
(35)
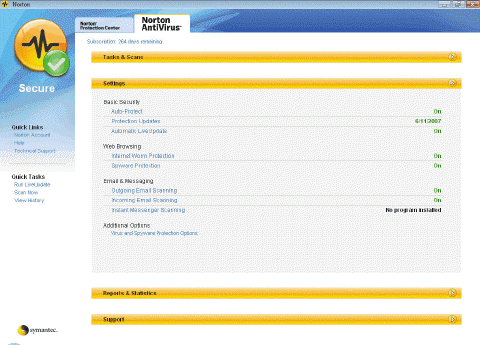 An antivirus program like the one in the accompanying figure also is called a serum.
An antivirus program like the one in the accompanying figure also is called a serum.
(True/False)
4.9/5  (42)
(42)
Modified Multiple Choice An area of computer ethics frequently discussed includes ____.
(Multiple Choice)
4.9/5  (42)
(42)
A(n) ____ is an injury or disorder of the muscles, nerves, tendons, ligaments, and joints.
(Multiple Choice)
4.9/5  (26)
(26)
A(n) ____________________ contains surge protection circuits and batteries that can provide power during power outages.
(Short Answer)
4.9/5  (41)
(41)
Showing 21 - 40 of 103
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)