Exam 8: Security Issues and Ethics in Education
Exam 1: Integrating Educational Technology Into the Curriculum102 Questions
Exam 2: Communications Networks the Internet and the World Wide Web103 Questions
Exam 3: Software for Educators102 Questions
Exam 4: Hardware for Educators103 Questions
Exam 5: Technology Digital Media and Curriculum Integration103 Questions
Exam 6: The Changing Face of Education 2d Teaching Online103 Questions
Exam 7: Evaluating Educational Technology and Integration Strategies103 Questions
Exam 8: Security Issues and Ethics in Education103 Questions
Select questions type
Spam is a scam in which a perpetrator sends an official-looking e-mail that attempts to obtain personal and financial information from the recipient.
(True/False)
4.9/5  (41)
(41)
A ____ is a program that is activated when a certain condition is detected.
(Multiple Choice)
4.8/5  (33)
(33)
 Antivirus programs like those in the accompanying figure work by looking for programs that attempt to modify the boot program, the operating system, and other programs.
Antivirus programs like those in the accompanying figure work by looking for programs that attempt to modify the boot program, the operating system, and other programs.
(True/False)
4.9/5  (27)
(27)
Biometrics is an applied science devoted to incorporating comfort, efficiency, and safety into the design of items in the workplace. _________________________
(True/False)
4.8/5  (32)
(32)
 Cryptogram is the process of converting readable data into unreadable characters by applying a formula that uses a code as shown in the accompanying figure. _________________________
Cryptogram is the process of converting readable data into unreadable characters by applying a formula that uses a code as shown in the accompanying figure. _________________________
(True/False)
4.8/5  (38)
(38)
A(n) ____________________ is a malfunction of a computer system.
(Short Answer)
4.9/5  (36)
(36)
By acquiring data from public and other sources, national marketing organizations can create an electronic profile of an individual.
(True/False)
4.8/5  (43)
(43)
Critical Thinking Case 8-2
You believe that your information privacy has been violated. You receive a call from your bank indicating that a large amount of money has been withdrawn. Which of the following is a likely cause of someone obtaining your personal and financial information?
(Multiple Choice)
4.8/5  (36)
(36)
____ is a service that blocks e-mail messages from designated sources.
(Multiple Choice)
4.7/5  (31)
(31)
 Briefly describe encryption, as shown in the accompanying figure, and tell why a school might need to use it.
Briefly describe encryption, as shown in the accompanying figure, and tell why a school might need to use it.
(Essay)
4.9/5  (42)
(42)
____ studies have shown that using the correct type and configuration of chair, keyboard, display device and worksurface helps users work comfortably and efficiently, and helps protect their health.
(Multiple Choice)
4.8/5  (36)
(36)
 In addition to detecting viruses and inoculating against them, antivirus programs like the one in the accompanying figure can ____.
In addition to detecting viruses and inoculating against them, antivirus programs like the one in the accompanying figure can ____.
(Multiple Choice)
4.9/5  (37)
(37)
Product registration is an antipiracy technology designed to verify that software products have been licensed legitimately. _________________________
(True/False)
5.0/5  (38)
(38)
A worm is a malicious software program that hides within a legitimate program.
(True/False)
4.9/5  (38)
(38)
A(n) ____________________ is a type of logic bomb that is activated on a particular date.
(Short Answer)
4.9/5  (36)
(36)
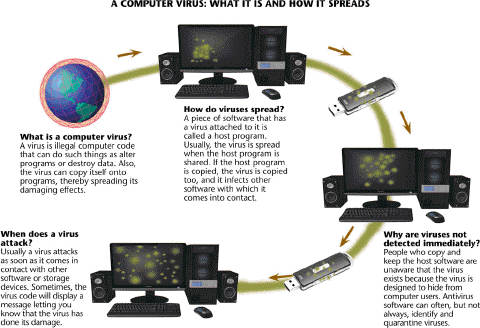 A(n) ____________________ is designed to detect, disinfect, and protect computers and networks from viruses like those in the accompanying figure.
A(n) ____________________ is designed to detect, disinfect, and protect computers and networks from viruses like those in the accompanying figure.
(Short Answer)
4.9/5  (49)
(49)
The daVinci virus destroys data on March 6, the date of the artist's birthday. _________________________
(True/False)
4.8/5  (44)
(44)
 Software licenses like the one in the accompanying figure are agreements that ____.
Software licenses like the one in the accompanying figure are agreements that ____.
(Multiple Choice)
4.8/5  (36)
(36)
Fair use guidelines allow teachers to use any copyrighted works for educational purposes without any restrictions.
(True/False)
4.8/5  (38)
(38)
Showing 41 - 60 of 103
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)