Exam 8: Operating Systems and Utility Programs
Exam 1: Introduction to Computers191 Questions
Exam 2: The Internet and World Wide Web191 Questions
Exam 3: Application Software191 Questions
Exam 4: The Components of the System Unit191 Questions
Exam 5: Input181 Questions
Exam 6: Output191 Questions
Exam 7: Storage191 Questions
Exam 8: Operating Systems and Utility Programs191 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management191 Questions
Exam 11: Computer Security, Ethics, and Privacy191 Questions
Exam 12: Information System Development191 Questions
Exam 13: Programming Languages and Program Development191 Questions
Exam 14: Enterprise Computing191 Questions
Exam 15: Computer Careers and Certification191 Questions
Select questions type
____ is a program placed on a computer without the user's knowledge or consent that secretly collects information about the user, often related to Web browsing habits.
(Multiple Choice)
4.9/5  (34)
(34)
Some operating systems include a Web browser and an e-mail program, enabling users to begin accessing the Web and communicating with others as soon as they set up the Internet connections.
(True/False)
4.8/5  (36)
(36)
Discuss booting, including definitions of both warm and cold boots. Outline the steps that take place during a cold boot on a PC running Windows Vista.
(Essay)
4.8/5  (38)
(38)
____________________ is an operating system based on Windows CE that includes functionality, applications, and a user interface designed for specific types of devices.
(Short Answer)
4.9/5  (30)
(30)
In most cases, the operating system is installed and resides on a computer's floppy disk.
(True/False)
4.9/5  (38)
(38)
Windows Vista Ultimate includes all features of Windows Vista Home Premium and provides additional featured designed to make mobile users' computers more secure and easier to network.
(True/False)
4.9/5  (31)
(31)
A file ____ utility is a utility that transforms the contents of a file or data from one format to another.
(Multiple Choice)
4.8/5  (36)
(36)
The boot process is very different for large and small computers.
(True/False)
4.9/5  (42)
(42)
 Figure 8-3 In a ____ like the one shown in Figure 8-3, a user types commands or presses special keys on the keyboard (such as function keys or key combinations) to enter data and instructions.
Figure 8-3 In a ____ like the one shown in Figure 8-3, a user types commands or presses special keys on the keyboard (such as function keys or key combinations) to enter data and instructions.
(Multiple Choice)
4.8/5  (31)
(31)
A(n) ____ is a small program that tells the operating system how to communicate with a specific device.
(Multiple Choice)
4.8/5  (39)
(39)
Some personal computer maintenance utilities continuously monitor a computer while it is used and repair problems before they occur.
(True/False)
4.9/5  (24)
(24)
If the user name and password entered match the user name and password kept on file, a network operating system denies access to the user.
(True/False)
4.9/5  (31)
(31)
When you purchase a computer, it usually includes a recovery disk.
(True/False)
4.8/5  (30)
(30)
In Windows Vista, the ____________________ feature protects your computer from spyware.
(Short Answer)
4.9/5  (34)
(34)
If a new device, such as a printer or scanner, is attached to a computer, its ____ must be installed before the device can be used.
(Multiple Choice)
4.8/5  (34)
(34)
A(n) ____________________ operating system allows a single user to work on two or more programs that reside in memory at the same time.
(Short Answer)
4.9/5  (40)
(40)
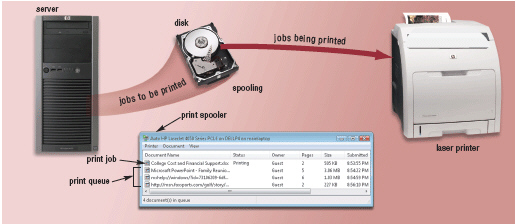 Figure 8-2 In Figure 8-2, multiple print jobs line up in a(n) ____________________ in the buffer.
Figure 8-2 In Figure 8-2, multiple print jobs line up in a(n) ____________________ in the buffer.
(Short Answer)
4.9/5  (38)
(38)
When users press a key or move the mouse, a screen saver disappears and the screen returns to the previous state.
(True/False)
4.9/5  (41)
(41)
A(n) ____ operating system enables two or more users to run programs simultaneously.
(Multiple Choice)
4.7/5  (39)
(39)
Showing 61 - 80 of 191
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)