Exam 8: Operating Systems and Utility Programs
Exam 1: Introduction to Computers191 Questions
Exam 2: The Internet and World Wide Web191 Questions
Exam 3: Application Software191 Questions
Exam 4: The Components of the System Unit191 Questions
Exam 5: Input181 Questions
Exam 6: Output191 Questions
Exam 7: Storage191 Questions
Exam 8: Operating Systems and Utility Programs191 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management191 Questions
Exam 11: Computer Security, Ethics, and Privacy191 Questions
Exam 12: Information System Development191 Questions
Exam 13: Programming Languages and Program Development191 Questions
Exam 14: Enterprise Computing191 Questions
Exam 15: Computer Careers and Certification191 Questions
Select questions type
Fragmentation speeds up disk access and thus the performance of the entire computer.
(True/False)
4.7/5  (33)
(33)
____ is an open source multitasking operating system designed for smart phones.
(Multiple Choice)
4.9/5  (38)
(38)
A(n) ____ system is a set of programs containing instructions that coordinate all the activities among computer hardware resources.
(Multiple Choice)
4.7/5  (27)
(27)
A(n) ____ drive is the drive from which a personal computer starts.
(Multiple Choice)
4.9/5  (38)
(38)
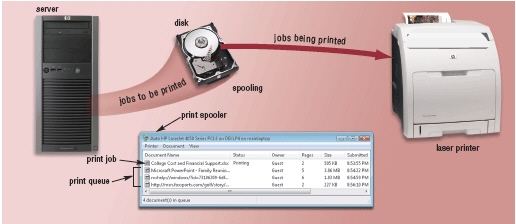 Figure 8-2 A(n) ____________________ is a segment of memory or storage, such as the disk in Figure 8-2, in which items are placed while waiting to be transferred from an input device or to an output device.
Figure 8-2 A(n) ____________________ is a segment of memory or storage, such as the disk in Figure 8-2, in which items are placed while waiting to be transferred from an input device or to an output device.
(Short Answer)
4.9/5  (32)
(32)
What functions do utility programs serve? Describe at least four common utility programs.
(Essay)
4.8/5  (42)
(42)
With ____ multitasking, the operating system interrupts a program that is executing and passes control to another program waiting to be executed.
(Multiple Choice)
4.8/5  (37)
(37)
A ____ is malware that hides within or looks like a legitimate program, such as a screen saver.
(Multiple Choice)
4.9/5  (32)
(32)
A disk ____ is a utility that searches for and removes unnecessary files.
(Multiple Choice)
4.8/5  (36)
(36)
The BIOS executes a series of tests, collectively called the ____, which check the various system components including the buses, system clock, adapter cards, RAM chips, mouse, keyboard, and drives.
(Multiple Choice)
4.9/5  (32)
(32)
Network administrators can set up a network to decrypt data as it travels over a network to prevent unauthorized users from reading the data.
(True/False)
4.7/5  (41)
(41)
If a hard disk is damaged, a computer can be booted from a(n) ____________________, which is usually a CD that contains a few system files that will start the computer.
(Short Answer)
4.9/5  (30)
(30)
When turning on a computer that has been powered off completely, users are performing a warm boot.
(True/False)
4.7/5  (32)
(32)
Identify the letter of the choice that best matches the phrase or definition.
Correct Answer:
Premises:
Responses:
(Matching)
4.8/5  (33)
(33)
The kernel is memory ____, which means it remains in memory while the computer is running.
(Multiple Choice)
4.9/5  (34)
(34)
Because virtual memory is faster than RAM, users may notice the computer speeding up while it uses virtual memory.
(True/False)
4.9/5  (33)
(33)
____________________ means the operating system automatically configures new devices as users install them.
(Short Answer)
5.0/5  (32)
(32)
Many backup programs ____, or shrink the size of, files during the backup process.
(Multiple Choice)
4.8/5  (28)
(28)
Showing 161 - 180 of 191
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)