Exam 3: Security Through Authentication and Encryption
Exam 1: Operating Systems Security: Keeping Computers and Networks Secure86 Questions
Exam 2: Viruses, Worms, and Malicious Software86 Questions
Exam 3: Security Through Authentication and Encryption86 Questions
Exam 4: Account-Based Security86 Questions
Exam 6: Firewalls and Border Security86 Questions
Exam 7: Physical and Network Topology Security86 Questions
Exam 8: Wireless Security86 Questions
Exam 9: Web, Remote Access, and VPN Security86 Questions
Exam 10: E-Mail Security86 Questions
Exam 11: Security Through Disaster Recovery86 Questions
Exam 12: Security Through Monitoring and Auditing86 Questions
Select questions type
Which authentication method is used on networks and in remote communications, typically employing Remote Authentication Dial-in User Servers and is compatible with many encryption methods?
(Multiple Choice)
4.9/5  (39)
(39)
Today, Kerberos is the most commonly used form of security for communications and transactions over the Web.
(True/False)
4.9/5  (37)
(37)
When following the ISO _____ format, a digital certificate includes a basic set of encrypted information.
(Multiple Choice)
4.8/5  (37)
(37)
When a network consists of Windows 2000 or later operating systems, Kerberos is the preferred logon authentication method.
(True/False)
4.9/5  (37)
(37)
____________________ is the science of creating secret messages.
(Short Answer)
4.9/5  (37)
(37)
What does SSH use to authenticate a communications session that uses passwords?
(Multiple Choice)
4.8/5  (28)
(28)
List and provide the key lengths for the three different flavors of RSA used by MPPE.
(Essay)
4.9/5  (35)
(35)
Which of the following cipher command-line parameters copies encryption key and certificate data to a file that is encrypted for use by the cipher user?
(Multiple Choice)
4.8/5  (31)
(31)
Are user passwords in Red Hat Linux encrypted using 3DES and stored in the /etc/passwd file?
(True/False)
5.0/5  (43)
(43)
Which version of hashing algorithm uses a mathematical formula to reduce a message to 160 bits and then hashes a digital signature to go with the message?
(Multiple Choice)
4.8/5  (39)
(39)
Was SSH developed by Netscape to provide authentication security for TCP/IP applications such as FTP and Telnet?
(True/False)
4.8/5  (30)
(30)
Was AES originally developed for the U.S. National Security Agency?
(True/False)
4.9/5  (36)
(36)
CFS can be used for remote file access through the NFS used by Netware systems.
(True/False)
4.8/5  (40)
(40)
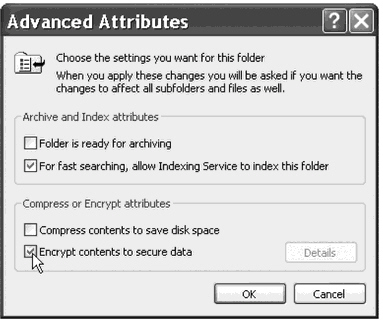 What form of encryption is being enabled in the figure above?
What form of encryption is being enabled in the figure above?
(Multiple Choice)
4.8/5  (33)
(33)
Showing 21 - 40 of 86
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)