Exam 3: Security Through Authentication and Encryption
Exam 1: Operating Systems Security: Keeping Computers and Networks Secure86 Questions
Exam 2: Viruses, Worms, and Malicious Software86 Questions
Exam 3: Security Through Authentication and Encryption86 Questions
Exam 4: Account-Based Security86 Questions
Exam 6: Firewalls and Border Security86 Questions
Exam 7: Physical and Network Topology Security86 Questions
Exam 8: Wireless Security86 Questions
Exam 9: Web, Remote Access, and VPN Security86 Questions
Exam 10: E-Mail Security86 Questions
Exam 11: Security Through Disaster Recovery86 Questions
Exam 12: Security Through Monitoring and Auditing86 Questions
Select questions type
Triple DES is a standard adopted by the U.S. government to replace AES.
(True/False)
4.9/5  (42)
(42)
Which authentication method authenticates by using tickets to verify client and server communications, and employs private-key encryption?
(Multiple Choice)
4.9/5  (34)
(34)
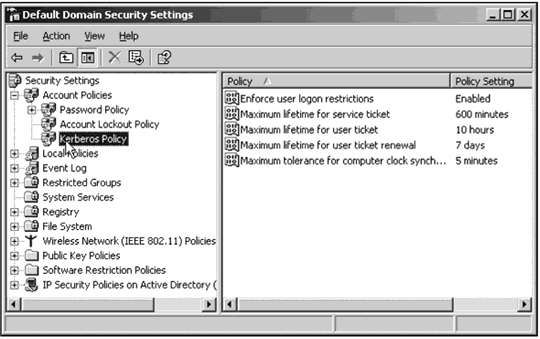 If getting users to log off when they go home at night is a problem, which option should you modify in the figure above?
If getting users to log off when they go home at night is a problem, which option should you modify in the figure above?
(Multiple Choice)
4.8/5  (41)
(41)
Message Digest 4 takes the original data and adds padded spaces until the length of the data section is 456 bytes.
(True/False)
4.9/5  (43)
(43)
What command can be used from the command prompt window to configure EFS?
(Multiple Choice)
4.7/5  (32)
(32)
Session authentication works by giving each frame or packet an identification or sequence number.
(True/False)
4.9/5  (28)
(28)
Which authentication method is used in Internet and network communications, and employs a handshaking protocol for authentication plus RSA for encryption?
(Multiple Choice)
4.8/5  (32)
(32)
Which version of hashing algorithm takes 8-bit (one-byte) chunks and creates an encrypted message that is padded until its length can be divided by 16?
(Multiple Choice)
4.8/5  (39)
(39)
When following the ISO X.509 format, what basic set of encrypted information does a digital certificate include?
(Essay)
4.9/5  (35)
(35)
Authentication makes data unintelligible to everyone except its intended recipients.
(True/False)
4.8/5  (30)
(30)
Sniffer software turns the NIC on its host computer into a virtual listening ear, capturing the network traffic that goes across that NIC on a particular network segment.
(True/False)
4.9/5  (34)
(34)
Which of the following sniffer application can be used in Windows-based operating systems?
(Multiple Choice)
4.9/5  (39)
(39)
_____ is the use of a secret code or other means to disguise data that is stored on a computer or transported across a network.
(Multiple Choice)
4.8/5  (37)
(37)
Which of the following encryption algorithms is considered to be the most secure?
(Multiple Choice)
4.8/5  (47)
(47)
The ____________________ field in the AH uses a special counter to activate anti-replay so that the receiver can determine if it has already received a packet.
(Short Answer)
4.8/5  (30)
(30)
What type of encryption is used for remote connections into Windows 2000 Server and Windows Server 2003?
(Multiple Choice)
4.8/5  (37)
(37)
Is the maximum size of the private key in AES 256 bits in length?
(True/False)
5.0/5  (31)
(31)
Showing 61 - 80 of 86
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)